Items filtered by date: December 2015
Cryptolocker Removal, Prevention and Mitigation
This article will help you deal with Cryptolocker, and hopefully prevent you getting it. If you are heere because you are already infected I have also givend some things you can try to get rid of the infection and hopefully recover some of your data.
Clean List
This does not unencrypt your files but cleans the infection. If your files are encrypted I would recommend buying a new hard drive and starting again on that drive while you wait to see if you can recover your files. Do not pay the ransom, there are no guarantees you will get your files back either. If you try an decrypt your files I would recommend performing that on an image of your drive, ye that’s right you could end up with 3 hard drives.
Recommended list of things to do to remove the Cryptolocker infection
- Image PC hard drive to another HDD
- Comodo Rescue - Boot from DVD, update and scan
- Hitman Pro Kickstart- Boot from DVD, update and scan
- Comodo CIS, install update and scan
- Malwarebytes, install update and scan
- sfc /scannow
- Netsh winsock reset
- Combofix
- Hitman Pro Alerts, install update and scan alerts
- Check for infections manually
- Scan with other Antivirus software (Avast/AVG....)
Prevent List
These are things you can do to reduce your chance of getting infected by Cryptolocker in the first place.
- Foolishit CyrptoPrevent - Modifies Registry and Group Ploicies
- Hitman Pro Alerts, install update and scan alerts
- Use Comodo CIS as your security solution and enable:
- HIPS
- Behaviour Analysis
- Virus Scope
- Auto Sandbox
- Comodo Secure DNS (or Your prefered secure DNS)
- Firefox - Use only this browser and:
- No Script
- Disble Flash by default
- Block all Adds (UBlock Origin)
- Run in a sandbox (Comodo CIS has this feature)
- Google Chrome
- Block all Adds (UBlock Origin)
- Run in a sandbox (Comodo CIS has this feature)
- Anythinthing else that is in the Firefox List
- Malwarebytes Anti-Exploit (Pro version is better)
- Malwarebytes Pro - Has a real time scanner
- User Account Rights
- Create an administrator account with a password on it
- Downgrade all accounts to Non-admin rights (Standard User)
- Software
- Use software whitelisting methods rather than blacklisting
- Update Windows (set to automatic updates)
- Update in particular
- Adobe PDF - better to completely remove
- Adobe Flash - better to completely remove
- Java - better to completely remove
- Update all software
- Remove unneeded software
- Network / Network Shares / Mapped Drives
- Secure DNS (Comodo/OpenDNS/Norton DNS etc..)
- Restrict what sites staff/computers can visit on a network level
- Disable public network settings in network sharing (advanced settings)
- make all shares read only or disable them, inluding c$, d$
- Dont use mapped drives
- Hardware SPI Firewall that scans the traffic on a hardware basis
- Always use a NAT router and never expose a computer to the internet witha real IP
- Disable all unneeded ports
- Point DMZ to a non-existant internal IP
- Email
- Spam filters on your email server
- Secure email to prevent credential capturing
- Antivirus Email scanning - A specific scanner that checks all incoming and outgoing mail for virus and then cleans the mail
- block all .exe in outlook or whatever email client you are using.
- HardCore (only if you really can)
- Remove internet access
- Disable all usb ports
- Remove all Web Browsers
- Use Group Policy and cripple the computer except for what is required of it.
* These measures could go in my security document
Mitigation
Backup Your Data
This is bar for one of the most importatn things you can do, but there are a few rules you must follow depending on your backup solution
- Backups should be created for all of the following reasons
- Restore from cryptolocker infection
- Prior version of files
- Hardware failure
- All backups must be stored off the machine with the data on
- Air-gapped backups are an excellent defence against cryptocloker but requires manual intervention
- When using shared folder to store backup
- Do not connect to backup shares with mapped drives
- Backup shares should be a unc path not a mapped drive. If there is no mapped drive, cryptolocker cannot see it.
- The share should have password protection on which is not the same as the logged on user. If cryptolocker does find the share, it is unable to logon because the user's account does not have permission.
- The username and password for the share will be stored within the backup software only preventing it being exposed to cryptolocker.
- Incremental backups
- Even if your files get encrypted you will have a prior version of ll your files.
- If you use just a backup and replace policy if your dont notice that your files are encrypted your backedup files will also get replaced with encrypted versions.
- Cloud Based backup
- These can be an excellent method of keeping your files safe as they tend to have incremental file backups in place.
- These systems will have massive hardware redundancy so you do not have to worry about this eithere
- The downside to these is there are a paid service so once you started to use them you have to keep paying them
Data Recovery Options
Image the affected Hard Drive before you do anything and make sure youo do not boot of the infected drive.
- Volume Shadow Copy / System Restore - Use these programs to browse SystemRestore Points
- ShadowExplorer.com - ShadowExplorer allows you to browse the Shadow Copies created by the Windows Vista / 7 / 8 Volume Shadow Copy Service. It's especially thought for users of the home editions, who don't have access to the shadow copies by default, but it's also useful for users of the other editions.
- System Restore Explorer - System Restore Explorer is a tool which allows you to browse system restore points on your computer and select individual ones for deletion should you wish to free up some disk space. It also allows you to mount the contents of a restore point into a folder so that you can browse and copy individual files, without the need to perform a full system restore.
- Previous Versions - Some folders store old versions of files using the System Restore technology. The Desktop fodlerdoes but i do not know what others do by default. You can acces these versions by
- Boot off the infected drive in to windows
- Navigate to the the Desktop folder via 'My computer' C:\Users\{User Account}\
- Right click on the Desktop folder
- Click on the 'Previous Versions' tab
- Restore files as needed.
- Browse the hard drive offline - In another computer and manually Copy off unaffected files.
Recommend Cleaning Software
- Comodo Rescue DVD
- Hitman Pro Kickstart DVD
- Comodo CIS
- Malwarebytes
- Hitman Pro Alerts
- Additional AV
- AVG
- Avast
Links
- http://www.bleepingcomputer.com/virus-removal/cryptolocker-ransomware-information
- http://www.surfright.nl/en/kickstart
- http://www.surfright.nl/en/cryptoguard
- https://www.youtube.com/watch?v=Gz2kmmsMpMI
- http://www.thewindowsclub.com/hitman-pro-alert-review-free
- http://www.surfright.nl/en/hitmanpro/
- How To Avoid CryptoLocker Ransomware — Krebs on Security
- CryptoLocker Virus – Best Practices to Ensure 100% Immunity | Comodo
Outlook/Live/Hotmail/Hosted Exchange SPAM Blacklist removal and Feedback loop
When sending an email to a Outlook.com / Live / Hotmail / Hosted Exchange email address you get the following or similiar email error message.
This message was created automatically by mail delivery software.
A message that you sent could not be delivered to one or more of its recipients. This is a permanent error. The following address(es) failed:
example-account@outlook.com
host mx4.hotmail.com [65.55.33.135]
SMTP error from remote mail server after MAIL FROM:<example@quantumwarp.com> SIZE=5281:
550 SC-001 (COL004-MC6F21) Unfortunately, messages from 192.168.1.1 weren't sent. Please contact your Internet service provider since part of their network is on our block list. You can also refer your provider to http://mail.live.com/mail/troubleshooting.aspx#errors.
Microsoft do not use a public Blacklist to block IPs so there is no public website where you can assertain the status of your server's standing with them. You are only likely to notice an issue when you get bounce backs from any Outlook.com / Live / Hotmail / Hosted Exchange email addresses. Outlook will block you from sending to any of their addresses when you are on their block list.
If you are on a shared host, it is your provider that will be able to resolve this for you. However if you are running on private server whether it is a VPS or a Dedicated server it is up to you to resolve this blacklisting. I will outline the steps for the latter group to remove themselves from the blacklisting.
Microsoft do offer the abillity to investigate the blacklisting and too eventually remove the listing. The information is a little fragmented so i will clear that up here and give defined steps on what to do.
Outline of the Process and Technology
When you run your own mailserver which is part of any VPS or dedicated server, that server's IP will resolve to a domain. That domain is the reverse DNS entry of the IP (rDNS) and it is this domain that has authoritive control over all email that server sends out. Microsoft will block the IP of a server if it thinks it is sending out spam consequently blocking all email traffic from your server to them, it does not care about indvidual domains.
To investigate or resolve issues with microsoft you need to register for a outlook/live account and prove that you have control of the authoritive domain. Once you have done this you are able to see the Blacklist status of your server and request it s removal. Once this is done you can then start sending emails to outlook/live email accounts from all your client accounts.
Further to this microsoft allows you to set something up called a Feedback Loop service. A Feedback Loop service is where outlook (or other providers) will send a copy of the SPAM complaint to a specified email address such as abuse@mydomain.co.uk . This allows yoou as a server admin to see who and where the SPAM is coming from so that you can resolve the infringment. This Feedback Loop service when set up will run whether you are on Microsoft blacklist or not which is incredible useful for preventing your server from becoming blacklisted in the first place.
Configuring a Feedback Loop with Microsoft is not mandatory for removal but is highly recommend. The reason for this is that just removing yourself from the blacklist will not necessarily resolve the sending of the SPAM and you could end up straight back on the blocklist. If your IP keeps getting triggered it will get hard to remove yourself from the list as it is likely that the wait time for removal will become longer.
So as you can see Microsoft would like you proactively stop SPAM and gives you the tools to do this aswell as a process for removing yourself from the blacklist.
The Process of Registering your Server and Blacklist Removal
Prerequsites
- Microsoft account - This is just a standard outlook/live/msn/hotmail account
- An email at the parent domain as defined by rDNS (This is the domain that is resolved when you perform a rDNS on the mail server's IP)
- Administrative control of the rDNS domain
Valid email addresses that Microsoft allows for authoritive control verification - do i need this section
These some examples of the valid emails Microsoft allows to verify your authority of the mail server. These addresses come from rDNS and will be different between server setups. Dont take this list as verbatim as when you go through the process Microsoft will show yoou the valid email addresses they will accept for your server.
- abuse@mus.mydomain.co.uk
- abuse@mydomain.co.uk
- abuse@unifiedlayer.com
- netops@unifiedlayer.com
- postmaster@mus.mydomain.co.uk
- postmaster@mydomain.co.uk
As you can see there are some non-mydomain.co.uk addresses in the list. These additional emails belong to your infrastructure providers as they must have some control over your server aswell. Not everyone will have these additional addresses as it depends on how you are connected to the internet.
Registering your Server with Microsoft
You must create an account with Microsoft and prove you have ownership of the server before you can do anything else.
- Create a Microsoft account at Outlook.com that you will use for your business if you do not already have one. I would avoid using a personal account here.
- Go to this link and sign in with your Microsoft account - Smart Network Data Services. This is the registration site for all Microsoft SPAM servers to you.
- Register your Domain/Server authority with Microsoft
- Click on request Access and submit your mail server's IP
- You will now be prompted with the following message and a list of valid email adresses for this process:
We've determined that the following email addresses are associated with the specified network in an appropriately authoritative way. Please choose one that you can receive mail at and we will send instructions for completing the signup process to that address. If you have questions about why the addresses below were chosen, please see the FAQ.
- Make sure you have access to one of these email addresses and if none of them exist you need to create one.
- Fill in the rest of the form and submit it.
- The email address you have supply will get a verification link you need to click on to verify that you have access to the is account.
If successful Microsoft will now associate you authoritive control of the server's IP to you Microsoft account allowing you to see the Blacklist status of your server. You might have to wait a small period of time before you can see the dat in your account.
You can also register multiple servers in the same account.
View Your Blacklist Status
In the Smart Network Data Services the View IP Status will show you the server's Blacklist status. If your server is blacklisted it will be quite obvious and if everything is ok you will see the following message.
All of the specified IPs have normal status.
Setting Up a Feedback Service with Microsoft (Junk Mail Reporting Program)
The Junk Mail Reporting Program (JMRP) is a service provided for email senders by Outlook.com. It lets you set up a feedback loop, so you can receive copies of messages Outlook.com users mark as junk.
You can access the JMRP through Smart Network Data Services or directly access the page at Junk Mail Reporting Program
The Steps
- You must already have an Authorized IP address from earlier when you registered you mail server's IP, if not go ahead and do that now.
- Fill in the following data and leave everthing else as default
- Company Name
- Contact email address - This is general contact email address where Microsoft will send you account updates like 'Your Server is now Blacklisted'
- Complaint feedback email address - This is where you want copies of the SPAM emails to go to, so dont make your main email address. I would set an account up just for this.
- Make sure your server's IP is ticked
- Click on 'Begin SetUp' and follow the steps outline.
You will now receive appropriate reports to you 'Contact email address' and copies of all the SPAM emails will go to the 'Complain feedback email address'. You can change these email addresses later so dont panic if you ever want to change them again.
Monitor the accounts to see if there are any SPAM activities happening on your server before proceeding to the next step.
Blacklist removal steps
Now that you are happy that your server is no longer sending out SPAM it is time to remove it of the Microsoft Block list.
Microsoft never tell you what is wrong, but if you cannot get unblocked after following these instructions the best thing is to join the SNDS and the JMRP. I did not get mitigation until Microsoft has accepted my application/document that i signed. They must use this as a big qualifier for mitigation.
I am not sure if you can remove the server from within Smart Network Data Services because i cannot remember.
Failed email Form method
- Get a bounced back email from outlook.com which should contain the failed messages
- If you send an email straight to to an outlook.com address you will receive no bounce back email
- To get a bounce back email you need to send an email from an outlook address and then reply to it. Microsoft replies to you with an error message rather than sending to a black hole.
- Navigate to this form - Sender Information for Outlook.com Delivery
- I filled in the form using the bounced back email and the other required details
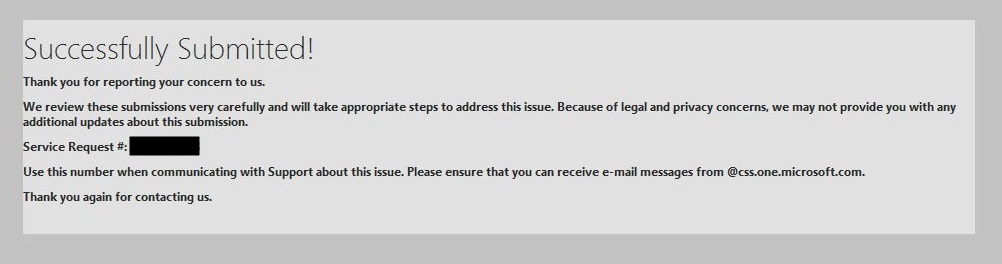
- I then received the following message on screen
Successfully Submitted! Thank you for reporting your concern to us. We review these submissions very carefully and will take appropriate steps to address this issue. Because of legal and privacy concerns, we may not provide you with any additional updates about this submission. Service Request #: xxxxxxxxxx Use this number when communicating with Support about this issue. Please ensure that you can receive e-mail messages from @css.one.microsoft.com. Thank you again for contacting us.
Remove the IP from the blocklist via Smart Network Data Services
This process might not exist and the emails belong to the form submission method. I will update this next time my server is blocked.
- I can't remember exactly what I did but i received the following emails.
- I received The following email almost instantly
Dear xxxxxx Please note that your ticket number is in the subject line of this mail. X.X.X.X Note: Errors are unlikely, however, if an error is indicated, please resubmit the specific IP or IP range. Thank you, Outlook.com Deliverability Support Please do not reply to this message as it is from an unattended mailbox. Any replies to this email will not be responded to or forwarded. This service is used for outgoing emails only and cannot respond to inquiries.
- 15 minutes later I received the following email
Dear xxxxxx We have completed reviewing the IP(s) you submitted. The following table contains the results of our investigation. Conditionally mitigated X.X.X.X Our investigation has determined that the above IP(s) qualify for conditional mitigation. These IP(s) have been unblocked, but may be subject to low daily email limits until they have established a good reputation. Please note that mitigating this issue does not guarantee that your email will be delivered to a user’s inbox. Ongoing complaints from users will result in removal of the mitigation. Mitigation may take 24 - 48 hours to replicate completely throughout our system. If you feel your issue is not yet resolved, please reply to this email and one of our support team members will contact you for further investigation. Regardless of the deliverability status, Outlook.com recommends that all senders join two free programs that provide visibility into the Outlook.com traffic on your sending IP(s), the sending IP reputation with Outlook.com and the Outlook.com user complaint rates. Junk Email Reporting program (JMRP) When an Outlook.com user marks an email as "junk", senders enrolled in this program get a copy of the mail forwarded to the email address of their choice. It allows senders to see which mails are being marked as junk and to identify mail traffic you did not intend to send. To join, please visit http://support.msn.com/eform.aspx?productKey=edfsjmrpp&page=support_home_options_form_byemail&ct=eformts. Smart Network Data Services program (SNDS). This program allows you to monitor the ‘health’ and reputation of your registered IPs by providing data about traffic such as mail volume and complaint rates seen originating from your IPs. To register, please visit http://postmaster.live.com/snds/. There is no silver bullet to maintaining or improving good IP reputation, but these programs help you proactively manage your email eco-system to help better ensure deliverability to Outlook.com users. Thank you, Outlook.com Deliverability Support
- The server is no longer blocked even though the status is not updated in Smart Network Data Services / View IP Status.
- The whole process took about 30 - 45 minutes
Relevant Sites
- https://postmaster.live.com/snds/ipStatus.aspx - This page can also confirm the status of the server
Links
- How to Remove Your IP from the Hotmail Blacklist - Below, I share the process we use in our Hotmail blacklist removal services. Using this process, we have near 100% removal success rate using this process. Excellent article.
- How to Check Microsoft Email Blacklist for Hosted Exchange | pinpointe - Microsoft Blacklist Check and removal. Explains how to tell if your emails are being blocked by Microsoft Exchange and how to get removed. Excellent article with example fail messages. Covers the other services aswell.
- SOLVED AND SOLVED AGAIN! How to remove a server IP from your black - Microsoft Community
- How to Remove (delist) your mail server IP from Hotmail, Live.com and MSN mail server blacklist | ☩ Walking in Light with Christ - Faith, Computing, Diary
- How to Remove Server IP Address from MSN Hotmail Block Blacklist « My Digital Life
- blocked using Blocklist 1; To request removal from this list please forward this message to delist@messaging.microsoft.com
- MxToolbox Forums • View topic - Include Microsoft Blacklist to tool? [RESOLVED]
- Delist new Blacklisted IP in delist@messaging.microsoft.com - Argh !!! - LowEndTalk
- SOLVED AND SOLVED AGAIN! How to remove a server IP from your black - Microsoft Community
- Outlook.com mailservers blacklisted - Microsoft Community
- Hotmail blacklist removal | Hosting Fixes
Cannot Send email with POP3 with outlook in Windows 10
This seems to be an issue when you upgrade to windows 10 that you cannot send emails with a POP3 account. The recommend solution is to run the following command as an administrator and the reboot your computer. Make sure Outlook is not running when you run the command
sfc /scannow
This fixes the majority of peoples setups.
Outlook 2013
I have a client who could not send from a POP3 account at all but then has performed the above command. He still cannot send emails from a POP3 account normally but when he exits and restarts Outlook as an administrator, those POP3 emails will send.
Notes
- There was an PDF addon causing issues/conflicts in outlook but this made no real difference
Client's setup:
- Windows 10 (pre 1511)
- Outlook 2013
- Single Profile
- Main account account is a Hosted Exchange account
- Secondary Account is a standard POP3 account
Things not Tried so far
- Delete whole profile and re-create
- Run pop3 and exchange accounts in different profiles
- Remove office ecommpletely and re-create
- Make sure all windows and office updates are applied, including the major windows update that has just come out
- Update to the new Windows 10
- Apply all office 2013 updates
- Change outlook version
.htaccess Proxy Examples
There might be occasional times you want to supply content from another site but appear under another domain so you can keep control of these assets. Using .htaccess for this is not supported on all servers because Hosting companies can turn this off. I cannot remember why i have different version, but option 1 does work.
1
RewriteEngine on RewriteRule ^(.*)$ http://demo.lancastrian-it.co.uk/$1 [P] ProxyPassReverse / http://demo.lancastrian-it.co.uk/
2
This method rewrites the urls and asset paths on the fly. The [PT] possibly could be [P,T]
RewriteEngine On
RewriteCond %{HTTP_HOST} ^www\.sitewithcontent\.eu$ [NC]
RewriteRule ^(.*)$ http://www.targetsite.co.uk/$1 [PT]
3
RewriteRule ^.*$ http://www.google.co.uk/$0 [L,P]
4
RewriteRule ^/redmine/.*$ http://localhost:3000/$0 [L,P]
Remove black box
The black box is called the Artboard (equvalent to the page or the bit that will be outputted)
To Remove
- View > Hide Artboards
Bounding Box
A Bounding Box is the grouped slector for an object. it is not the artboard (ie the blackbox denoting the page)
Remove Bounding Box
- View > Hide Bounding Box. (toggle on and off)
Bounding Box Links
Remove white background
When you first start using Adobe Illustrator you will come across the annoying white background.
This background is not part of the image and is possibly called the 'Art Board'.
To remove it there are several options outlined below:
- export as a psd (from ai). This also has the side effect of correctely cropping the image id the background is mismatch for the image/logo. The PSd has layers and seem to match up well with the objects. You can then do what you want including "save for web" which allows you to save it as a PNG with transparency
- "save for web" - this is the simplisted method but does not crop the image if mismatched to the background
- shift+CTRL+D - How to Make Adobe Illustrator Background Transparent | BudgetVideo4BIZ Blog
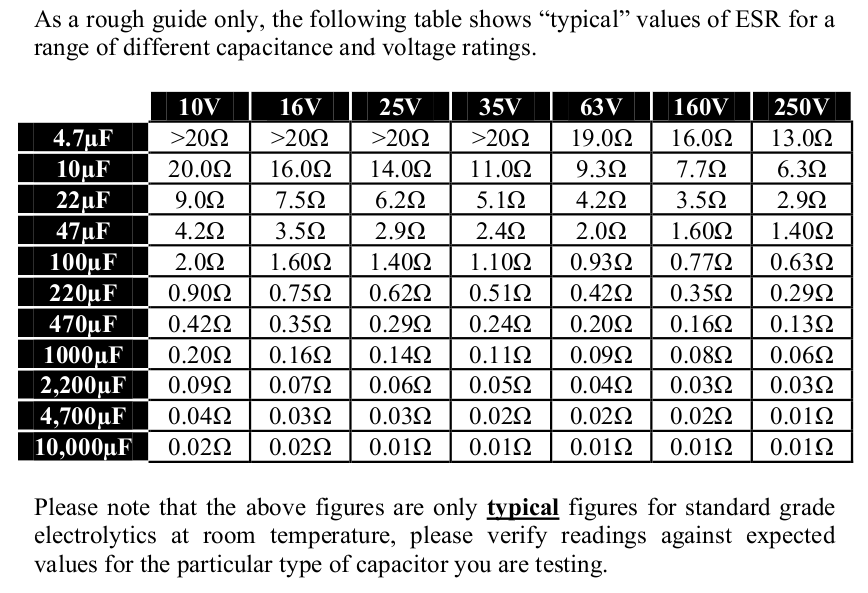
ESR Chart
This is a quick chart for getting average ESR values for capacitors. It is only a guideline and should not be used for an accurate record.
Login to the Rasberry Pi GUI
When you are loaded at the command prompt you want to login to the GUI.
- Type startx
The Default Username and Password are:
- user: pi
- Password: raspberry
Move a Magento Installation
To move a magento installation you cannot just move the files, you need to make changes in the database aswell as the database connection settings.
Domain Configuration
Search for these in the database, Table core_config_data has rows and change them:
web/unsecure/base_url http://[you_domain_here]/ web/secure/base_url https://[your_secure_domain_here]/
Then clear the cache by deleting the files in the following directories
/var/cache /var/session
Database Settings
The database config settings of magento are stored in the file below. I cannot remember if you need to change anything elese here other that the database connection settings.
/app/etc/local.xml
Do not leave old XML files in this directory (ie rename old-local.xml) because magento will try and parse these files aswell.
.htaccess
Dont forget to change any domain specific rules such as a canonical redirects.
Browser
- Clear your browser cache
- restart your browser
Links
3 Red Circles
These animated icons can be used for almost anything and are very easy to change. They can add something different to your page.
Design.
We design and build responsive, functional web solutions for clients all across the UK. Working closely with you to ensure that you get the best possible product.
Develop.
We believe in maintaining our design and code standards. We do not cut corners. The result is fantastic bespoke websites completely tailored to your business.
Support.
Our support team are ready to help with any queries you may have. From email support, queries regarding your website to sales and upgrades.
CSS
/* Red Circle's Animation and styling Code */
.service-circle, .service-box, .service-icon {
margin:auto;
-webkit-transition-timing-function: cubic-bezier(0.13, 0.71, 0.30, 0.94);
-moz-transition-timing-function: cubic-bezier(0.13, 0.71, 0.30, 0.94);
-o-transition-timing-function: cubic-bezier(0.13, 0.71, 0.30, 0.94);
transition-timing-function: cubic-bezier(0.13, 0.71, 0.30, 0.94);
-webkit-transition-duration: 0.5s;
-moz-transition-duration: 0.5s;
-o-transition-duration: 0.5s;
transition-duration: 0.5s;
}
.service-circle{
position: relative;
display: block;
width: 125px;
height: 125px;
text-align: center;
border-radius: 108px;
margin-bottom: 30px;
overflow: hidden;
}
.service-circle {
-webkit-box-shadow: inset #B02B2C 0 0 0 3px;
-moz-box-shadow: inset #b02b2c 0 0 0 3px;
box-shadow: inset #B02B2C 0 0 0 3px;
}
.service-circle .fa {
display: block;
position: absolute;
top: 0;
left: 0;
width: 125px;
height: 125px;
font-size: 50px;
line-height: 125px;
color: #B02B2C;
}
.service-circle .circle {
background: #B02B2C;
}
.service-circle .circle {
display: block;
position: absolute;
top: 12px;
left: 12px;
width: 101px;
height: 101px;
border-radius: 96px;
}
.service-circle .circle {
-webkit-transition-timing-function: cubic-bezier(0.13, 0.71, 0.30, 0.94);
-moz-transition-timing-function: cubic-bezier(0.13, 0.71, 0.30, 0.94);
-o-transition-timing-function: cubic-bezier(0.13, 0.71, 0.30, 0.94);
transition-timing-function: cubic-bezier(0.13, 0.71, 0.30, 0.94);
-webkit-transition-duration: 0.5s;
-moz-transition-duration: 0.5s;
-o-transition-duration: 0.5s;
transition-duration: 0.5s;
-webkit-transform: scale(0);
-moz-transform: scale(0);
-o-transform: scale(0);
-ms-transform: scale(0);
transform: scale(0);
}
.service:hover .service-circle {
-webkit-box-shadow: inset #B02B2C 0 0 0 10px;
-moz-box-shadow: inset #b02b2c 0 0 0 10px;
box-shadow: inset #B02B2C 0 0 0 10px;
}
.service:hover .service-circle .circle {
-webkit-transform: scale(1);
-moz-transform: scale(1);
-o-transform: scale(1);
-ms-transform: scale(1);
transform: scale(1);
}
.service:hover .service-circle .fa {
color: #FFF;
}
.service-circle .fa {
-webkit-transition-timing-function: cubic-bezier(0.13, 0.71, 0.30, 0.94);
-moz-transition-timing-function: cubic-bezier(0.13, 0.71, 0.30, 0.94);
-o-transition-timing-function: cubic-bezier(0.13, 0.71, 0.30, 0.94);
transition-timing-function: cubic-bezier(0.13, 0.71, 0.30, 0.94);
-webkit-transition-duration: 0.5s;
-moz-transition-duration: 0.5s;
-o-transition-duration: 0.5s;
transition-duration: 0.5s;
}
.service-circle, .service-box, .service-icon {
-webkit-transition-timing-function: cubic-bezier(0.13, 0.71, 0.30, 0.94);
-moz-transition-timing-function: cubic-bezier(0.13, 0.71, 0.30, 0.94);
-o-transition-timing-function: cubic-bezier(0.13, 0.71, 0.30, 0.94);
transition-timing-function: cubic-bezier(0.13, 0.71, 0.30, 0.94);
-webkit-transition-duration: 0.5s;
-moz-transition-duration: 0.5s;
-o-transition-duration: 0.5s;
transition-duration: 0.5s;
}
HTML
<div> <div class="service" style="float: left; width: 30%; min-width: 180px; margin: 5px;"> <div class="service-circle"> <div class="circle"></div> <i class="link-icon fa fa-car"></i> </div> <h2>Design.</h2> <p> We design and build responsive, functional web solutions for clients all across the UK. Working closely with you to ensure that you get the best possible product. </p> </div> <div class="service" style="float: left; width: 30%; min-width: 180px; margin: 5px;"> <div class="service-circle"> <div class="circle"></div> <span class="link-icon fa fa-phone"></span> </div> <h2>Develop.</h2> <p> We believe in maintaining our design and code standards. We do not cut corners. The result is fantastic bespoke websites completely tailored to your business. </p> </div> <div class="service" style="float: left; width: 30%; min-width: 180px; margin: 5px;"> <div class="service-circle"> <div class="circle"></div> <i class="link-icon fa fa-user"></i> </div> <h2>Support.</h2> <p> Our support team are ready to help with any queries you may have. From email support, queries regarding your website to sales and upgrades. </p> </div> </div>
Changes
Make Circles Larger
/* Make Circles Larger */
.service-circle{
width: 216px;
height: 216px;
}
.service-circle .fa {
width: 216px;
height: 216px;
font-size: 100px;
line-height: 216px;
}
.service-circle .circle {
width: 192px;
height: 192px;
}
Change Colour
/* Change Colour */
.service-circle {
-webkit-box-shadow: inset #B02B2C 0 0 0 3px;
-moz-box-shadow: inset #b02b2c 0 0 0 3px;
box-shadow: inset #B02B2C 0 0 0 3px;
}
.service-circle .fa {
color: #B02B2C;
}
.service-circle .circle {
background: #B02B2C;
}
.service:hover .service-circle {
-webkit-box-shadow: inset #B02B2C 0 0 0 10px;
-moz-box-shadow: inset #b02b2c 0 0 0 10px;
box-shadow: inset #B02B2C 0 0 0 10px;
}
Notes
- Depending on you implementation of Font Awesome your code for the icon can be slightly different. You might need to play around with the syntax.
Original code from www.web-easy-sites.co.uk <i class="fa icon-line-speech-bubble"></i> JSN Time <i class="link-icon fa fa-car"></i> NS Font Awesome <i class="fa fa-bar-chart-o fa-4"></i> ** the fa-4 is a preset size and does not need to be used
- You can probably use other vector icons instead.
