Items filtered by date: December 2015
My Concrete, Mortar, Cement and Aggregate Notes
All you need to know about concrete
- It will always go off
- It will always crack
- No-one will steal it
Mixes Table
| Mix Ratio (by volume) Cement/Sand/Aggregate |
Name | Generally used for | Notes |
| 1 : 2 : 4 | Concrete | Small slabs, Fence posts |
|
| 1 : 3 : 3 | Concrete | Slabs, Floors, Walls, footings (foundations) |
|
| 1 : 2 : 3 | Concrete | DIY projects |
|
| 1 : 3 : 0 | Concrete Mortar | Mortaring/Pointing Retaining walls and Chimneys. |
|
| 1 : 4 : 0 | Mortar | Bricklaying |
|
| 1 : 4 (with plasticiser) |
Scratch Coat (bottom coat) |
Rendering brick |
|
| 1: 5 (with waterproofer) |
Finish Coat (top coat) |
Rendering brick, Pebble dashing |
|
| 0 : 3 : 3 | Pre-mixed Ballast / All-In Ballast | Part of the mix for footings |
|
- This ratios are done by volume, i.e. 1 shovel of cement, 2 shovels of sand and 4 shovels of aggregate.
- The sand is always building/builders sand in mortar and concrete
- Not all concrete applications can you use building sand.
- There seems a lot of debate about this
- I always use building sand in my home projects
- What Is Sharp Sand? | Sharp Sand Uses | Avon Material Supplies - What is washed sharp sand and why use it? See why sharp sand (also known as grit) is ideal for mortar, concrete, paving and landscaping.
- Plasticiser should only be used with mortars.
- in the M5, M7.5....., M20 categorisation of the aggregate content seems to always be twice the sand content
Notes
These are my notes on concrete mixes and various project using concrete, mortar and cement.
- General
- Choosing the Right Cement for Your Needs - JTD Building Supplies - Choosing the right cement for your building project is the first step to success. Whether youâre trying some masonry work, repairing a driveway.
- Concrete vs Mortar
- 7 Differences Between Mortar and Concrete Everyone Should Know - YouTube - Mortar and Concrete are the two most important and widely used materials in the Construction industry. Knowledge of these both is important for everyone.
- Difference between concrete and mortar - YouTube - This video shows Difference between concrete and mortar. Mortar is a mixture of sand, cement and water while concrete is a mixture of cement , sand , water and coarse aggregate.
- Concrete vs Cement vs Mortar: Which One Should You Use When Building Or Remodeling Your Home? | Homebuilding / Remodeling Guide - Trying to decide between concrete vs cement? They have very specific uses. Cement is rarely used by itself. Concrete is used in most building projects.
- The Differences Between Cement, Concrete, and Mortar | The Spruce - The terms cement, concrete, and mortar are often used interchangeably, but they actually have different uses. Learn the definition of each.
- Mix Ratios / Mixing Ratios
- What are the Correct Concrete Mixing Ratios - Ratio Chart
- When making your own concrete it's important to use the correct concrete mixing ratios to produce a strong, durable concrete mix.
- Some basic mixing ratios for concrete are 1:2:3, 1:3:3, 1:2:4. These mixing ratios are based on the proportions of cement : sand : stone in that order. The ratio you use will depend on what psi strength you need.
- Has tables showing the different mixes
- Mortar Advice | Travis Perkins - Mixing mortar help and advice
- Complete Guide To Mortar Mixing & Ratios | Guides4Homeowners - Quick Answer: The most common mortar mixing ratio used is 1 part cement, 4 parts sand. It does however depend what job you are undertaking as it may need to be stronger. We’ve written a complete guide to get the best mortar mixing ratios for whatever task you you are undertaking.
- How to Mix Cement to Make Cement Mortar or Concrete | Marshalls - In this blog we will concentrate on the two types of mixes that utilise cement to bind other components together, to make a robust building material.
- Mortar Mix Ratio Guide | Homehow - Introduction to Mortar Mixing, Finding the ideal mortar mix ratio is a vital part of any construction or maintenance project in which mortar is being used.
- How to Mix Mortar for Paving | Simply Paving - Before you consider finding the right paving stone for your patio, you need to know how to mix mortar. Read on to see how to do it yourself.
- A Guide to Mortar Mix Ratios & Cement Mixing | Beesley & Fildes - Welcome to Beesley & Fildes builders merchants online store. Bricks, timber, plumbing, landscaping & building supplies at the lowest prices.
- How to Choose the Right Mortar Mix Type: N, O, S, or M
- Selecting mortar mix type N, O, S, or M for any masonry project is based on the performance characteristics of the mortar and the compressive strength.
- Has an excellent diagram.
- The Ultimate Guide to Mortar Mix Ratios [Updated 2022] - Discover the best mortar mixes for various projects including brickwork, blockwork, chimneys, roofing and flooring projects and many more.
- How to Mix Mortar for a Variety of Jobs | DIY Doctor - How to mix mortar for a variety of different jobs including house walls, chimneys, pointing, paving, render and floor screed
- What are the different types of mortar mixes? | Never Paint Again - One aspect of our work that defines us apart from your local painter and decorator is the fact we also do rendering, alteration and repairs to render as well as painting houses. We have to be very clued-up about the use of mortar and all it's permutations, so we thought today we would share some of that knowledge with yourselves.
- Concrete and Mortar Guide - Mix Ratios, Curing Times and More - How to mix Concrete and Mortar. A complete DIY guide to concrete and mortar. Use the best concrete mix for the task, learn how to mix mortar and more.
- What is meant by ratio of 1:4:4 in concrete mixture? And is it ok if I use this composition for building? - Quora
- Different Types of Concrete Grades and their uses | Base Concrete
- What are the different types of concrete grades and what are they used for?
- psi chart of the different mixes
- Understanding Concrete Mix Ratios | All Mixes for All Concrete Projects - Concrete Flooring Solutions delves into the different concrete mix ratios to help DIYers create effective mixes and provide contractors with a useful mixing reference.
- Mortar mix for retaining wall? | MIG Welding Forum - I've done a fair bit of lime plaster, gypsum plaster, concrete, stone walls... But zero block work. Need to build a very small retaining wall.
- Concrete Mix Ratio and How to Mix Concrete | DIY Doctor - We explain what concrete mix ratio you need and how to mix concrete, including a handy concrete mix ratio calculator for your materials
- What are the Correct Concrete Mixing Ratios - Ratio Chart
- Calculators / Calculations
- Calculators | Pavingexpert - A listing of the various calculators made available throughout the pavingexpert web site
- Concrete Mix on Site | Construction Calcs - This concrete calculator will estimate the quantity of sharp sand, cement and aggregate.
- The Quick & Easy - Mix Your Own Concrete Calculator - Builder HQ - This concrete estimator is for knocking up concrete on site. The results are in 25kg bags of cement and 850kg or 25kg of all-in ballast.
- Metric calculator for concrete - cement, sand, gravel etc - Concrete Materials Calculators - easy to use metric calculators for working out the cement, sand, gravel or all-in ballast required for concrete.
- Aggregate Quantity Calculator for Bulk Aggregate Orders - Use our handy quantity calculator to estimate how much of our bulk aggregates you need. Simply measure the area needed to cover and we will calculate roughly how many tonnes, bulk bags or mini bags required.
- How to Calculate Quantities of Cement, Sand and Aggregate for Nominal Concrete Mix (1:2:4)? - Happho - Happho
- A simple yet more accurate method (DLBD method) of calculating cement, sand and aggregate for Nominal Concrete mix M15, M20, M25 and M30 grade Concrete
- has a chart for the mixes M15, M20, M25, M30
- Aggregate is always twice the sand???
- Decorative Gravel Calculator - Estimate Material QTYs Fast Online | AWBS - Simple online Aggregate Calculator for accurately estimating quantities of sand, hardcore and gravel for your building or landscaping project.
- Retaining Wall
- Hard Landscape Features - Walls and Brickwork | Pavingexpert
- A brief guide to walls suitable for use in hard-landscaping projects
- Excellent diagrams
- Retaining Wall Drainage: How to Drain Water Properly - Pool Research - I walk you through how to design your retaining wall to properly drain water and maintain the integrity of your wall.
- Retaining wall design | Screwfix Community Forum
- Retaining Wall Drainage & Backfill Basics - Landscaping Network - Discover four retaining wall design basics – base, backfill, drainage & height – that will help ensure you get a quality wall when hiring a landscaping contractor.
- Sleeper Retaining Wall - Drainage & Best Practices | Renovate Forum
- How To Build A Garden Wall | Blog | Bradstone - Looking to build a wall, but not too sure where to start? Check out our simple to follow how to build a garden wall guide here.
- How to build a new extension from scratch part 1: The foundations - YouTube - In these videos we are building a new extension and will be going through the stages from the foundation to the superstructure
- Hard Landscape Features - Walls and Brickwork | Pavingexpert
- Retaining Wall Foundation
- Creating good concrete foundations for a garden wall - I have seen many a garden wall that has cracked or moved because of the builder cheating or miscalculating the quantity of materials for the construction of the wall foundations.
- Foundations for a 50 meter garden wall - YouTube - Hi everyone here I am working on a large project, a 50 meter wall. This video is in some detail and shows the many issues facing a job like this. In this video I show how I overcame them.
- How To Lay Foundations - YouTube - Digging the foundations for a wall is a physically hard job, and it could take you a couple of days, but its worth doing properly as the success of your wall building endeavours will depend on the quality of your footings. Here is how its done.
- How to cast a concrete footing for a timber summerhouse base - YouTube
- The HouseSpouse is back in the garden in the middle of winter to produce a concrete footing. Here is part 1 of the build, demonstrating how to mix your concrete.
- 1 Cement : 6 Ballast
- 1 Shovel of Cement : 6 Shovels of Ballast (might be callec `All In Ballast` ?)
- Foundations
- How We Pour Footings and set levels accurately - YouTube
- Pouring a footing using a spirit level and peg method. The aim is to give accuracy and keep the tools out the concrete after its poured. Its advised not to leave the roofing battens in the footings. This Technique is great for garden walls and and small projects. On larger sites a laser level can be used. Steels (reinforcing bar or mesh) in the footings are optional and not necessary unless specified in the project brief.
- A simple no-nonsense video that shows exactly what needs doing.
- How We Pour Footings and set levels accurately - YouTube
- Flags and Slabs
- Laying Courses and Bedding Materials for Flags and Slabs | Pavingexpert - A look at the types of materials used as bedding material when laying Paving Flags or Slabs
- Aggregates
- Choosing The Right Building Aggregate For You | JTD Building Supplies - Building and landscape aggregates are a versatile substance used in foundations, construction and gardens. Here's our complete guide.
- How to Choose The Right Aggregate for Your Project | AWBS - With many different types of aggregates available, for use in different applications, how do you know which is best for your particular task and how much you’re going to need?
- The Difference Between Building Sand & Ballast | UK Home Improvement - Starting a home improvement project and need to know the difference between building sand and ballast? Then this article is perfect for you
- All-in Ballast, Bulk Bag | DIY at B&Q - All-in Ballast, Bulk Bag - B&Q for all your home and garden supplies and advice on all the latest DIY trends
- Brick Laying
- Basic Bricklaying and Cement-Mixing Guide for Beginners - Dengarden - This simple guide will show you the basics of bricklaying and mixing cement mortar. I will also go over what tools you need, especially when you're just starting out.
- How i built my breeze block shed part 2 - YouTube - how i built my shed using a 'Bricky' tool.
- How to do a foundation for a small extension - YouTube - In this youtube video I take you through step by step in the setting out, digging, concreting, and laying the first courses of block work up to damp course.
- Curing Process
- What happens to concrete if it gets buried before it fully dries? - Quora
- How Long Does Concrete Take to Set? Expert Advice from Concrete Specialists - Concrete Flooring Solutions
- Expert Advice from Concrete Specialists How Long Does Concrete Take to Set?
- In most cases, standard concrete (or full strength concrete) has a setting time of around one day, sometimes two days depending on the environment in which it is set. However, concrete reaches its full strength after approximately 25-28 days. You should be able to walk and perform normal tasks on concrete one week after its application. However, the concrete will only be at around 70-70% of its full strength, so driving heavy machinery on it is not advised during this time.
- How Long Does Concrete Take to Dry? | Dynamic Concrete Pumping - Concrete typically takes 24 to 48 hours to dry, but concrete drying is a fluid event. Learn about concrete drying time from Dynamic Concrete Pumping today!
- How Long Does Concrete Take to Cure? What Factors Affect the Process? | The Concrete Network
- Concrete doesn’t reach its full strength instantly after hardening – it has to go through the curing process first. That means you have to wait a little longer before putting any weight on it – so if you’ve just laid a driveway, keep your car away from it for the time being and read this article to learn all about the concrete curing process.
- Technically, concrete never stops curing. In fact, concrete gets stronger and stronger as time goes on. But, as far as we’re concerned, to reach a practical strength, most industrial concrete mixes have a 28 day curing period.
- After 7 days, the concrete will have gained around three quarters of its compressive strength, but you should refrain from driving vehicles or heavy machinery over the surface until after the 28 day mark.
- How Long Does Mortar Take To Cure? - Powerblanket - As construction projects progress, it can be exciting to reach the final stages. Applying finishing touches to newly reconstructed or refurbished surfaces results in eye catching aesthetics. Mortaring tiles or other masonry, adds a final polish to all your hard work. Just like concrete, mortar requires careful planning and execution to make sure you achieve the ideal cure strength and a strong finish. Let’s take a closer look at what affects mortar cure time and the strengths of different mortars.
- Cement and Mortar Dyes
- Colour Matching Mortar and Cement Mixes | DIY Doctor - How to correctly colour match sand, cement and mortar mixes if you need them to match exactly to existing mortar, pointing or repairs
- Lime mortar mix with sand for beige/light colour pointing - MyBuilder - We use a 3.5 Hydraulic lime mix for pointing (ratios: 1 hydraulic lime, 2 soft sand, 1 sharp/grit sand), and for walling we use 5.0 Hydraulic
- Concrete Pigments | harristone - Here is a list of our most popular concrete dyes. Also referred to as cement dye the powdered pigment is packaged in 25kg bags and is used to colour precast concrete by adding it to the concrete as it is being mixed.
- Matching mortar for brickwork and blockwork joints - YouTube - Matching sand and cement mortar for brickwork joints and blockwork joints can be done to a pretty exact standard but it does take some patience and a bit of time. Using mortar toners and variations on the sand to cement ratio it can be seen from the video tutorial that most colours can be obtained.
- Mortars and Tools | matclad.co.uk - Various coloured mortars and some information about them.
- Coloured Mortar for Pointing | Marshalls - Marshalls provide only the strongest of mortars and with their range of Coloured Mortar brick and patio laying will become a breeze.
- Bostik Cementone Cement & Mortar Dye - Buff 1kg | Wickes.co.uk
- Bostik Cementone Cement & Mortar Dye - Buff 1kg
- Buff colour = Sandstone
- Rendering
- external render - MyBuilder - i'm thinking of rendering an external entry wall on my property.can you tell me the ideal mix/ratios of materials and also what type of sand do is best to use? also,what additives do i use? [i.e. plasticiser/waterproofer etc.......] and how much of this do i need to use?
- Rendering mixes/ratio for scratch and top coat - MyBuilder
- Strong mix ratio: 3 to 1 scratch coat, 4 to 1 top coat
- Standard mix ratio: 4 to 1 scratch coat, 5 to 1 top coat
- Ideal render mix and why? | Screwfix Community Forum
- 1st coat (scratch coat) 3:1 sharp sand with waterproofer and scratched. Is vital that the waterproofer is added in the correct amounts according the the manufactures instructions.
- 2nd coat (floating coat) 4:1 sharp sand with waterproofer as above etc. This coat should be applied while the first coat is still green to enable suction of the 2nd coat to take place.
- It is important to know that each coat should be weaker than the previous coat as this enables the render to cope with temperature variations and stops it cracking.
- Just make sure that they prep the walls properly before the render is applied otherwise it will fail. ie seal porous bricks etc and ideally most if not all the joints should be raked out to a depth of 20/25mm.
- Render Mix Ratio | What is the Best Mix for Rendering?
- Most renders are typically made up of sand, water, cement, and lime. A standard render mix ratio is 6 parts sand, 1 part cement, and 1 part lime (6:1:1).
- A simple rule is never to make the rendering mix stronger than the material to be rendered.
- What's The Best Mix For Rendering? Roger's Guide | Skill Builder
- What's the best mix for rendering? Roger helps you get the perfect ratio for your rendering mix.
- 6:1:1 which is six parts of sand, one part of cement and one part of hydrated lime
- Rendering A Wall (The Beginners Guide) - Plastering For Beginners
- One of the biggest areas of plastering is learning to render. Thats why we're going to provide you with a complete guide on rendering a wall aimed at beginners.
- This is an indepth tutorial.
- The Ultimate Guide to Mortar Mix Ratios [Updated 2022]
- Render Mortar Mixes (Modern Buildings)
- The first coat of render should ideally be slightly stronger than the second coat. While some tradespeople make the two mixes the same strength, the second coat should never be stronger than the first coat.
- A pure soft sand mix shouldn’t be used when rendering. It’s preferable to use either sharp sand, plasterer’s sand or a mixture of two. Soft sand can be added to the mix but we feel it shouldn’t comprise more than 25% of the entire mix.
- The first coat of render can be 2 parts plasterers sand and 2 parts sharp sand, 1 part cement and half part lime. Waterproofer can be applied to the first coat if the property is modern.
- The second coat must be slightly weaker than the first, so 3 parts plasterers sand, 2 parts sharp sand, 1 part cement and half lime. Plasticiser can be used in the second coat.
- For locations in the east and south of the country or any sheltered location that experiences less windswept rain, a slightly weaker mix can be used. For the first coat 4 parts sharp/plasterers and for the second coat 5 parts sharp/plasterers.
- Render Mortar Mixes (Modern Buildings)
- Pebble Dashing
- Preparing for Pebbledashing | Pebbledashing.com - Preparing for pebbledashing aggregates.
- So how do you pebbledash | Screwfix Community Forum - A forum thread from Screwfix.
- Everything You Need to Know About Pebble Dashing | Paul Atkins Plastering - Do you want to know what pebble dashing is and what it is used for? This article will tell you everything you should know about this rendering technique.
- How To Pebble Dash Rendered Walls - YouTube - James shows us how he likes to pebble-dash rendered walls in King Build Part 9.Our thanks go to James King for letting Roger film this extension project series.
- external plastering (pebble dashing) - YouTube - External plastering, Pebble dash method, with sand and cement Mortar, Dashed with Canterbury spar, or rose flint spar.
- Cracks in concrete
- General
- Has your ready-mixed concrete cracked? | Hanson UK - What causes cracks in concrete slabs?
- Why Does Concrete Crack? How to Stop Cracking - Concrete Network - Information on how to prevent concrete from cracking provided by the Concrete Network. This includes major reasons cracking occurs, including excess water in the mix, rapid drying of the concrete, improper strength, and lack of control joints.
- Is It OK if Concrete Cracks? When You Should Worry About It - Let’s crack the surface on this question
- Why Concrete Cracks | Concrete Crack Solutions | Ardex Ireland - Cracks in concrete are extremely common but often misunderstood. Learn how to diagnose 6 types of concrete cracks here.
- Repair Methods
- How to Repair Concrete Cracks - This guide will show you a step by step process of repairing cracked concrete using Resincoat Epoxy Crack Repair.
- How to Fix Cracked Concrete - Why does Concrete Crack? | Total Concrete - In this article, discover the most common causes of concrete cracks and the most effective ways to fix them. Learn more about why concrete cracks here.
- How To Fix Driveway Cracks For Good | Home Logic UK - Laying a new driveway is not something that a homeowner takes lightly. It can be an expensive investment, it can cause disruption and it can take a long time to find the best person to carry out the work.
- Concrete sealants: Say goodbye to unsightly cracks - Concrete sealants help you when you need to fix those pesky surface cracks in concrete areas. Please read our guide on how to fix this.
- How to Repair Wide Cracks in Concrete | The Spruce - Learn how to repair wide cracks in concrete, using a concrete patch material. Create the best seal by preparing and cleaning the crack first.
- Crack Injection for Concrete Basement Walls - Concrete Network - While concrete cracks appear to be typical, it is not recommended that they remain ignored.
- How to Handle Cracks in Concrete - Concrete Decor - This article details how to prepare your customers for potential issues by shedding light on how to handle cracks in concrete.
- Sealing and Waterproofing Cracks in Concrete | QUIKRETE: Cement and Concrete Products - Over time and exposure to the elements exterior concrete can develop cracks due to temperature changes, ground movement, improperly placed joints and excessive loads. Once a crack develops it is important to seal the crack from water to prevent further deterioration.
- Solved! What to Do About Cracks in a Concrete Driveway - Bob Vila - By analyzing the size and position of cracks in your concrete driveway you can determine what steps you can take to fix it. Here is what to do about those cracks.
- Fix Cracked Driveway Cement using Sika Flex Sealant - YouTube
- Fix Cracked Driveway Cement using Sika Flex fix and a caulking gun.
- I have several small to medium sized cracks about 1/4 inch wide. I wanted to seal them before the winter. If you do not seal them then the snow melt water gets in then over night freezes and moves makes the crack worse.
- I used a heavy duty caulking gun. About 8 tubes of Pro Select Crack Flex sealant. This stuff was again hard to find. I had to go to 3 different big box stores to find enough what I needed. Again hard to find and they only had a few in stock. These are kind of pricey at $11 a tube but it is good stuff.
- Buy Sika Crack Flex Sealant
- Sikaflex® Crack Flex Sealant - YouTube | Sika USA
- Sikaflex Crack Flex Sealant is a single component, textured, self-leveling, premium grade polyurethane sealant for permanently sealing horizontal cracks. Use: Sikaflex Crack Flex Sealant is used to seal horizontal cracks up to 1" wide in concrete and cementitious slabs, such as driveways, garages, sidewalks, balconies, pavements, terraces, decks, walkways, steps, and more.
- Shows how to apply it.
- Sika concrete crack sealer - YouTube
- DIY home repair, concrete crack repair, concrete sealer, 'Sika Pro Select, Self Leveling sealant'
- Shows how to apply it.
- YouTube search - 'sikaflex crack repair'
- How to Fill in Cracks in Concrete - YouTube - In this video I demonstrate how to prepare cracks in concrete to be filled and how to actually fill them so they are water tight.
- How to repair cracks in concrete with ARDEX P 10 SR - Rapid Hardening Crack Repair Resin Kit - YouTube
- ARDEX P 10 SR is ideal for the rapid repair and bonding of static, non-structural cracks and joints in concrete and sand/cement screeds.
- Sold as a complete kit, consisting of mixing bottles, stitching pins and gloves. ARDEX P 10 SR is easy to use and requires no special tools.
- It can also be used to bond carpet grippers, profiles and trims made of metal, plastic wood and other materials.
- How to repair cracks in Concrete with ARDEX P 10 SR Rapid Hardening Crack Repair Resin Kit - YouTube - In his third lockdown video, Steve Davies, our National Training Manager shows you how to repair cracks in concrete and sand/cement screeds with ARDEX P 10 SR Rapid Hardening Crack Repair Resin Kit.
- How to Fix a Crack in a Driveway - YouTube - This video is a review of Quikrete Concrete Crack Seal after 1 year. I will show you how the product looks a year after applying it to cracks.
- How to seal concrete control joints - YouTube - I am the owner/operator of Slab Rite Concrete Lifting in Draper, Utah. One of the services we offer is sealing the control joints and cracks in concrete slabs. This video shows the technique we use of sealing very wide joints up to 2 1/2" inches using non-sag sealant.
- SEAL / FILL / FIX / A CRACK IN CONCRETE DRIVEWAYS - YouTube
- This video explains the causes of cracks in concrete driveways.
- There are several types of cracks in concrete: Structural cracks, and shrinkage cracks. Structural concrete cracks should be sealed to prevent water from penetrating through the slabs. When water penetrates into the soil that supports the concrete, soil may settle, creating a bigger crack over time.
- Sealing a crack is not fixing a crack as most people think. Sealing a crack is the application of sealant (caulk) into the crack. The purpose of sealant or caulk in a crack is to just stop water leakage under the slabs and stop vegetation from growing in the crack.
- How To Fix Cracks In Concrete- And Blend In The Repair! - YouTube - Had a few cracks in my concrete driveway, wanted to fix them without the obvious difference in color that so many repairs end up with. Using some quikrete over the crack sealant makes it look much better.
- Concrete Driveway Crack Repair - YouTube
- To repair a crack in concrete you can use flexible caulking designed for concrete driveways or a concrete patch.
- I am using Slab to fill a wide and deep crack. If your crack is deeper than 1/2 inch fill the void with a filler rope to support the caulk.
- The stuff to use
- The Best Concrete Crack Filler Options of 2023 - Top Picks by Bob Vila - The best concrete filler will restore the look and weather resistance of any concrete surface. See top-rated options and shopping tips here.
- 5 Best Caulk for Concrete Cracks Reviews in 2023 - Top Selling & Popular Collections - YouTube - Are you thinking of buying the best Caulk for Concrete Cracks? Then the video will let you know what is the best Caulk for Concrete Cracks on the market right now.
- Epoxy Crack Repair | Concrete Crack Filler | Resincoat - Epoxy Crack Repair from Resincoat is a pourable, easy to mix and use concrete crack filler. Ideal for use on fine or hairline cracks up to 2cm deep.
- Repair cracks in concrete and tarmac - Smartseal - Easily repair cracks and holes in imprinted concrete and tarmac driveways with Crack Repair Compound.
- Parabond 600 Adhesive Mastic - PARABOND 600 is a fantastic adhesive mastic which is ideal for applications within the building and engineering industry.
- Sikaflex® Self-Leveling Sealant | SIKA
- A Self Leveling sealant with an accelerated curing capacity for sealing horizontal expansion joints in concrete.
- Chart showing this and other products usage
- Sikaflex® Crack Flex Sealant | SIKA
- A one-component textured self leveling sealant used for sealing horizontal cracks.
- Chart showing this and other products usage
- 250ml Concrete Crack Repair Epoxy - Sika | CPC
- A two part grey epoxy paste, mix in the tube adhesive for high strength repairs to concrete
- Can be injected into cracks
- Provides high strength repairs to concrete
- Can be used on damp concrete
- Resistant to water and most chemicals and solvents
- Colour: Grey
- Size: 250ml cartridge
- Everbuild Foam Sealant Joint Backer Rod 10mm x 10 Metre : Amazon.co.uk: DIY & Tools - Shop Everbuild Foam Sealant Joint Backer Rod 10mm x 10 Metre.
- CRL Closed Cell Backer Rod 15mm Ø - 30.5m - The Wholesale Glass Company
- CRL Closed Cell Backer Rod is a round, flexible, closed cell polyethylene foam with an exterior "skin" used as a backing and thickness control device for elastomeric and other cold-applied sealants. The Backer rod becomes an integral part of the joint into which it is installed
- The Backer rod limits the depth of the sealant, thereby preventing excessive use of the sealant, which promotes proper joint design. Because the sealant will not bond to the "skin" of the rod, it can stretch and recover with joint movement, with minimal stress being put on the points of adhesion to the substrate.
- Closed-cell backer rods should not be used with sealants that cure by reacting with moisture in the air because the closed cells will not allow air in from the back of the sealant bead, in turn retarding the cure.
- Fischer FIS V Hybrid Mortar Resin 360ml - Screwfix - Order Fischer FIS V Hybrid Mortar Resin 360ml at Screwfix.com.
- No Nonsense Mortar Repair Grey 310ml - Screwfix - Order No Nonsense Mortar Repair Grey 310ml at Screwfix.com.
- General
- Tools
- The New Bricky® Wall Building Tool. - The New Bricky® Adjustable Wall Building Tool.
- You Can Build It DVD - YouTube - Inventor of the Bricky Noel Marshall walks us through how he built his his home office.
- How To Build A Garage/ Workshop - Part 1 - YouTube - How To Build A Garage/ Workshop
- How To Build A Wall - YouTube - Check out http://bricky.com for more information.Marshall Building Profiles enable us to build walls with absolute precision & supreme efficiency.
- Building With Marshall Profiles & Bricky Pro - YouTube - Noel Marshall setting up at the recent Home Improvements Show, London. On display his Inventions Marshall Profiles & new adjustable Bricky. Walls can now be built faster & with mm precision.
- Bostik Mortar Plasticiser » www.matclad.co.uk - Mortar plasticiser helps brick slip pointing mortar to flow through the nozzles of pointing guns and bags. All our pointing mortars are graded with fine aggregates but sometimes just a drop of this can help it flow even better than it does already.
- The New Bricky® Wall Building Tool. - The New Bricky® Adjustable Wall Building Tool.
- Misc
- Lime and Plasticiser - Forum - Landscape Juice Network - I’m just wondering. How to people decide when use lime or plasticiser in mortar mixes and importantly when NOT to use them.
- A Guide To Pouring Concrete in the Rain (updated 2022) - A guide to pouring concrete in the rain.
- How to Sand Concrete with a Sander/Grinder or by Hand » The DIY Hammer - Read this comprehensive 6-step Guide and FAQs on How to Sand Concrete with a Sander / Grinder or by Hand with Sandpaper, incl. Concrete Finishes with Photos
- Timberlink Catalogue
- Full range of builders Aggregates- Building Sand, Concreting/Sharp Sand, Ballast, MOT, Decorative Gravel.. Bulk/ Loose, Dumpy Bags, 20Kg Bags in stock. Handy volume calculator.
- Nice pictures
- Huges Gray / Buildbase
- Nice pictures
- Buildbase Building & Timber Supplies work closely with leading manufacturers of Aggregates & Gravel to provide cost-effective solutions to all construction requirements.
- Odell Complete Concrete - YouTube
- Independent Contractor License Number CA. 620752 C-8, B. AZ. 337940Serving all of Orange County AND LA Ranked #1 In Both CountiesNo Job to large or too small, we do them all! My work Ranges from Home Remolding, Concrete work, drive ways, barbeque islands, Patios, Planters, Foundations, Block Walls, Tile, Stone Walls, And Much More just Contact me for details of any job you have in mind
- Absolute professional.
My Bed, Mattress and Duvet Notes
Bed
Your bed is linked to the mattress size you select.
My preference is for a Pine Wood bed with storage space underneath. I dont like Divans as I feel they are old.
Mattress
These are my notes for figuring out what bed and mattress I need.
- Considerations for bed size and matress selection
- What height are you?
- What weight are you?
- Do you sleep on your front/back or on your side?
- Do you have any back problems?
- Do you have a partner?
- Matress Size Guides - what size is right for you?
- Bed Size Guide - UK & European | Dreams - Choosing the right size mattress is an important decision when buying a bed to ensure a great sleep. Find more information online here!
- UK Bed Sizes: The Bed And Mattress Size Guide | mybedframes
- Learn everything you need to know about UK Bed and Mattress sizes. Dimensions are shown in both imperial and metric units. Single, Small Double, Double, King Size and Super King Size.
- Also includes Giant Bed sizes
- Mattress size guide - IKEA
- Choosing a size is step number one when shopping for a new mattress. And to make sure you’re comfortable at night, there are a few basic guidelines to look for when finding the perfect size.
- Europeans have bigger mattresses
- Bed Sizes UK: Bed and Mattress Size Guide - Bed Advice UK - There are so many things to consider when you’re buying a bed or mattress – not least what size you should opt for.
- Your Guide to UK Mattress Sizes | French Bedroom
- Find the right size mattress for your bed, we’ve put together this easy to understand guide for what size mattresses are in the UK, Europe and the US.
- Apparently there is an emporer size bed (7ft x 7ft).
- What Size Mattress & Bed Do I Need? | Dormeo UK - Not sure whether you need a double, queen, king or super king mattress? Find out the exact dimensions of each type of bed and learn which is best for you in our handy guide to mattress sizes.
- Beds for tall people - The Definitive Buying Guide | Bedstar - Choosing beds for tall people is a challenge; what is available? Read our Buying Guide on choosing the Best Bed of length is an issue.
- Which Mattress Type?
- Soft, Medium, Firm or Extra Firm – Which One Is Right For You? | Sleepeezee UK - Buying a bed or mattress can be daunting with so many different types and models. That’s why spending the right time researching and understanding the different options will ensure you choose the right mattress that best suits you!
- Buying a Mattress | Mattress Types & Sizes | John Lewis & Partners - Learn more about Buying a Mattress at John Lewis & Partners. Offering expert insight and advice, make informed product selections with our buying guides.
- Mattress buying guide 2023 How to choose the best one for you: Shopping tips | The Independent - Searching for a new mattress? Here we compile shopping tips and expert advice on how to choose the best mattress for you through our mattress buying guide
- Bed & Mattress Guide | Dreams - As Britain's leading beds and mattress specialist, our Bed & Mattress Guide is the only resource you need when buying your next bed and mattress.
- How to Choose a Mattress: Bed Buying Guide & Shopping Tips | goodhousekeeping.com - It all comes down to your body type, sleep position and any personal preferences.
- Mattress buying guide | Argos - Mattresses at Argos. From memory foam to firm mattresses, our guide will help you choose the best.
- How To Choose A New Mattress: Ultimate Bed Buying Guide - If you need help choosing a good mattress, then speak to the mattress experts at John Ryan. We have decades of experience and over 5000 useful articles!
- Bed Buyers' Guide - Bed Advice UK
- The Bed Buyers’ Guide to help you understand the factors in buying a bed and mattress, and helps you find your perfect bed and perfect night’s sleep.
- Many sections of realted infromation from caring from your bed to selecting a pillow.
- How to Choose a Mattress - Bed Advice UK
- Mattresses may look similar, but the differences within are vast - we look at some of the main options when deciding the best type of mattress for you.
- this gives the examples of the different types of springs you can get.
- Mattress Buying Guide Considerations - Furniture Village
- If you’re wondering how to choose a mattress, you’ve come to the right place. The Furniture Village mattress buying guide describes all the types of mattresses available, points you to the best mattress for your sleeping position and even answers top questions when buying a mattress.
- If your mattress is too firm, a mattress topper is a good way of adding an extra layer of softness without investing in a whole new mattress.
- Mattress Buying Guide | Choosing the Right Mattress | DFS - Struggling to find your dream mattress? DFS have created an extensive mattress buying guide highlighting mattress types, benefits and more.
- Mattresses | Dreams - Find the perfect mattress and achieve greater sleep with the Dreams collection. Expect a range of sizes, styles and exclusive brands all with free delivery.
- Suppliers
- Carpetright | Carpets, Flooring and Beds - Carpetright is the UK's largest retailer of carpets, flooring and beds. Carpetright has 350 UK stores and an extensive online range of carpets, vinyl, laminate, rugs and beds.
- DFS | Sofas, Sofa Beds, Corner Sofas and Furniture - DFS sofas come in fabric and leather. Choose from a great range of sofa beds, leather sofas, corner sofas, corner sofa beds and more household furniture
- Bensons for Beds - Your Sleep Experts | Beds, Mattresses & More - Find your best type of bed, your comfiest mattress, sofa beds for guests & bedroom furniture in your style. Brands including Slumberland, Silentnight & more
- Dreams | Beds from the UK's Leading Bed & Mattress Store - Shop online for beds, mattresses & more from leading brands with free delivery nationwide. All sizes. Comfort guarantee. We're never beaten on price!
- Dormeo | Memory Foam Mattress Specialists - Dormeo the UK memory foam and hybrid mattress specialists. Sleep better with our range of mattresses. Free UK delivery and 0% finance available
- John Ryan | Handmade Mattresses UK | Pocket Sprung Mattresses - John Ryan are the UK's most trusted bed retailer. Handmade, pocket sprung natural-fibre mattresses, made by experts for a perfect night's sleep.
- Sleepeezee | Buy Beds & Mattresses Online UK - Shop Beds & Mattresses Online at Sleepeezee.com. Design your own bespoke single, double and king sized luxury beds. Beds with storage, Ottoman beds and more. Every Sleepeezee product is made at our factory in Rochester, Kent, by over 300 expert craftspeople.
- EveSleep | Spring & Foam Mattresses - Free Delivery - Shop six award winning, gorgeously comfortable mattresses at eve sleep. Try for 365 days with free delivery and hassle free returns.
- Oak Furnitureland | Solid Wood Furniture and Sofas - Oak Furnitureland offers great value solid wood furniture and sofas, always made for life. Shop online with up to 50% off and transform your home today.
- Foam Only
- Emma Original Mattress | UK's Most Awarded Mattress
- Which? Best Buy Mattress ✓ Made in UK ✓ 200 Night Risk Free Trial ✓ Free delivery & Returns ✓ 10 Year Warranty ✓ ▷ Buy Emma online now!
- made in Britain, German company.
- Simba Sleep | Mattress In a Box Europe's Best Reviewed - One Mattress. Five Layers of Comfort. Tailored to Suit All. Bringing together experience & technology so that your mattress gives you the best night's sleep.
- Casper® | The Best Bed for Better Sleep - Get the sleep you've always dreamed of. Casper's award-winning mattresses, sheets & more are quality-crafted and ethically built in the USA. Free shipping & returns!
- Emma Original Mattress | UK's Most Awarded Mattress
- Travelodge (Dreamer Mattress by Sleepeezee)
- Dreamer mattress from Travelodge available to buy online - Get the best deal on the Travelodge Dreamer™ mattress available in single, double, kingsize and super king direct from the manufacturer Sleepeezzee.
- Travelodge Sleepezee Dreamer mattress - Hello I’m looking to purchase the mattress from travelodge which is the Sleepeeze dreamer but it only says 950 sprung. I need a double size for my husband and I. I would like to know more on what you think of it as I can’t find any reviews, we love the ones used in the Travelodge which are a luxury king size so will the double be equally as nice although smaller?
- Travelodge Mattress Review UK | October 2022 - A mattress that has grown in popularity lately is the Travelodge mattress. If you're reading this article, chances are also that you had a few good nights'
- Sleepeezee Reviews | Read Customer Service Reviews of sleepeezee.com - Do you agree with Sleepeezee's TrustScore? Voice your opinion today and hear what 985 customers have already said.
- Sleepeezee Travelodge Dreamer review - Which? - The Sleepeezee Travelodge Dreamer is a pocket-spring mattress which aims to replicate the comfort of a nightâs stay in a hotel. But is it up to the job and will you really feel like youâre in an uber-comfy hotel bed? Read our full test review to see how long this mattress will last and if your spine will get the support it deserves.
- Travelodge Dreamer™ | Buy Online | Travelodge | Sleepeezee - The Travelodge Dreamer™ mattress boasts over 950 individual pocket springs within each mattress. Partnered with a platform top divan it offers superior support. Each individual spring is designed to follow the natural contour of an individual’s body in order to provide the correct amount of support and comfort to ensure you receive a good quality night’s sleep. A comfortable night’s sleep is also good for the heart, with £20 from every sale donated to the British Heart Foundation. We also offer a mattress recycling service, giving you a cost-effective, hassle-free way of disposing of your old mattress and/or bed!
- Premier Inn (Hypnos Mattress - old)
- Premier Inn mattress review & alternatives - John Ryan by Design - How well does the Premier Inn Hypnos mattress compare to John Ryan By Design? Can you get a better bed for your money? We investigate for you.
- Premier Inn (Silentnight Mattress)
- Silentnight announced as Premier Inn bed supplier - Whitbread PLC - The UK’s biggest hotel company Premier Inn is delighted to confirm it has appointed Silentnight as its official bed supplier as it invests in its most technologically-advanced bed yet to the benefit of guest experience.
- Premier Inn switches bed supplier - Interiors Monthly Magazine! - Premier Inn, the UK’s biggest hotel company, has switched bed supplier. It has appointed Silentnight as its official bed supplier.
- The bed features a Geltex comfort layer and a zippable, removable topper. The chain says this supports its Force for Good sustainability agenda. Composite bed parts are 92% recyclable.
- Premier Inn bed | Sleep | Premier Inn - At Premier Inn, we’re all about comfort, quality and, a great night’s sleep. A big part of that is all thanks to our super comfy beds. Buy the beds here.
- Reviews
- Silentnight vs Hypnos Mattress Reviews | Updated 2021 - Find out if Silentnight or Hypnos is suitable for you! We have reviewed both and determined the firmness, composition, and customer satisfaction scores to determine the right mattress for you.
- Silentnight Mattress Reviews: 2023 Beds To Buy (or Avoid?) - Read eye-opening Silentnight mattress reviews from real customers that are proven and trusted. Our experts will share little-known and research-backed facts about the full Silentnight offering that you need to know now!
- Silentnight Mattress Reviews UK - Should You Buy? | 2023 - Silentnight is one of the UK’s largest mattress suppliers. But are these mattresses any good? Sleep Hero puts them to the test.
- Best mattress: 9 top-rated memory foam, hybrid, pocket-sprung | Express.co.uk - Hunting for the best mattress can be a headache, so we've done the hard work for you - testing a dizzying number of popular Bed In A Box brands and different mattress types to find the best mattress available in the UK today. In this guide, we've rounded up nine of the best mattresses, including memory foam, pocket sprung, and hybrid designs to accommodate all sleeping styles and budgets. Almost all of our top picks offer generous risk-free trial periods, taking the guesswork out of your next mattress purchase.
- Sleepeezee Reviews: 2023 Mattresses Ranked (Buy or Avoid?) - Read eye-opening Sleepeezee mattress reviews from real customers that are proven and trusted. Our experts will share little-known and research-backed facts about the full Sleepeezee offering that you need to know now!
- Best Mattress 2023: 17 Tried And Tested Mattresses | British GQ - Struggling to get comfortable? We’ve got you.
- Mattress brands Reviews, Ratings and more : What Mattress
- Compared: Simba vs. Emma ➡️ Which Mattress Is Best? (2023)
- DON'T get scammed, is the Simba or the Emma mattress best? Compare mattresses side-by-side with my unbiased versus review. 20% off coupon.
- There is a video.
- emma mattress unboxing - overview - compared to Simba UK foam | YouTube | Alan Ross Reviews
- Misc
- The no turn mattress scam - John Ryan by Design - Don't be tricked by the 'No Turn' mattress scam. Here we explain exactly what you need to know before buying a no turn mattress.
- Pillowtop = An additional layer on the top that looks like a permanent topper
- Foam only mattresses are not good, they do not last long.
- If you firm bed is too firm, you can use a topper to add a softer layer without replacing the mattress.
Mattress Dimensions
I have more notes in my XLSX....
| Type | Dimensions |
| Single | 3′ x 6’3″ (90cm x 190cm) |
| Double | 4’6″ x 6’3″ (135cm x 190cm) |
| King | 5′ x 6’6″ (150cm x 200cm) |
| Super king | 6′ x 6’6″ (180cm x 200cm) |
Duvet
Read through all of these articles to see what other people have done and give your more information
- How to choose your Duvet
- Buying Duvets & Pillows | Duvet Tog Guide | John Lewis & Partners - Learn more about Buying Duvets & Pillows at John Lewis & Partners. Offering expert insight, make informed product selections with our buying guides.
- Best Duvets 2023: Duvet Brands From Ikea To John Lewis Rated By Customers - Which? - We rate duvets from Ikea to John Lewis. Find out which brand came out on top inour survey, and the pros and cons of the main duvet types
- Best duvet filling 2022: Choose the right natural or synthetic filling for your needs | Expert Reviews - Anyone who has braved a British winter knows how crucial a warm, comfortable and high-quality duvet can be to getting a good night’s sleep. However, when replacing worn out items, duvets are often
- How To Choose The Best Duvet | Guide | scooms - Our best duvet buying guide covers the 10 most important things to think about when buying a duvet: tog rating, duvet filling, fill power & weight, how the duvet is made and the environmental impact. Plus, duvet sizes, anti-allergy bedding, accreditations to look for and how to care for your duvet.
- Duvet Size Guide | Soak&Sleep - Looking to buy a new duvet? Our handy size guide explains the differences between UK sizes and which duvet is the right size for your bed.
- Duvet Size Guide: Everything You Need To Know | Sleep Journal - There is much more to selecting the right duvet than simply choosing a single duvet for a single bed, a double duvet for a double bed, or perhaps a king size duvet for an extra-large bed. In this article, we are going to look at exactly how to find the right size duvet for your bed.
- Duvet Size Guide | What Size Duvet is Best for Your Bed? | Victorian Linen - We supply duvets and duvet sets for every size of bed so let us share our expertise when it comes to beds and the best duvets for each size.
- A Definitive Guide to Bed Sizes & Duvet Sizes – The Big Little Duvet Company - Helping you with beds sizes & duvet sizes. If you are lost in a minefield of bed sizes and duvet sizes and not sure which is right for you and the size of your bedroom then we are here to help you with impartial advice. Big Little Duvet Company don't sell beds but we understand how important it is to know the exact measurements of your bed before you can decide on your duvets. We've decided to give you all the information you need for bed sizes in the UK.
- Should I oversize my Duvet (i.e. Super King on a King size bed)
- Experts reveal that you should size up your duvet for a good night's sleep | Ideal Home
- Getting well-deserved rest is important, so you should make sure you're doing it right
- Sleep experts say your duvet should be one size bigger than your mattress
- Manchester Collection Blog Quilts Why Upsize To Super King Quilt For A King Mattress? - Why Upsize To Super King Quilt For A King Mattress? - Manchester Collection Blog Quilts Why Upsize To Super King Quilt For A King Mattress? - If you have a King mattress, then we highly recommend upsizing to a Super King quilt. It will help you enjoy a more comfortable sleep. Firstly what’s Super King? It’s the largest possible bedding size available in Australia.
- Has anyone got a super king duvet on a king size bed? | Mumsnet
- King Sized bed - which sized Duvet? in The AnswerBank: Home & Garden
- buying a lager duvet than bedsize - Page 1 - Homes, Gardens and DIY - PistonHeads UK
- Supersize your King Size Duvet Cover Sewing Tutorial UK size | YouTube | Sewjojo sewingandcrafts
- Experts reveal that you should size up your duvet for a good night's sleep | Ideal Home
- What is TOG
- TOG is the heat retention rating of the Duvet.
- Different manufacturers Duvets will have different physical dimensions and weights for the same TOG.
| BED SIZE | DUVETS (W x L) |
|---|---|
| Cot Bed | 120cm x 150cm 47" x 59" |
| Single | 135cm x 200cm 53" x 79" |
| Double | 200cm x 200cm 79" x 79" |
| King Size | 230cm x 220cm 91" x 87" |
| Super King | 260cm x 220cm 102" x 87" |
| Emperor | 290cm x 235cm 114" x 93" |
What I want
- Bed
- King Size Pine wood bed.
- Mattress
- King Size
- A mattress that I can turn over (last twice as long?)
- Firm
- Pocket Springs
- Traditional Tufting
- Edge Support
- This is so you can sit on the edge of the mattress without it deforming.
- No Memory Foam
- This stuff is nasty and wears out quite quickly.
- A mattress protector
- A mattress protector will stop sweat and other liquids damaging the mattress. Make sure it is a quality protector.
- Duvet
- Super King Duvet
- This is an oversized duvet for my bed.
- This will give me extra cover and make sure my feed will never be out in the cold.
- It will drape over the sides of the bed and hide storage underneath the bed whilst giving a more modern look.
- The weight keeps the Duvet down on your mattress better.
- More Duvet if your partner is a Duvet thief.
- More heat efficient as there are less gaps.
- More snuggly.
- Super King Duvet
My TL631 Pro Motherboard Diagnostic and Debug Card Notes
I bought this diagnostic card from AliExpress but the instructions were not the best but there is a lot of information in the product page. I am merging the information I find here.
- TL631 Pro Universal Laptop And PC PCI PCI E Mini PCI E LPC Motherboard Diagnostic Analyzer Tester Debug Cards|Instrument Parts & Accessories| - AliExpress
- Some examples of how users have used their debug cards
- Eakins Store are good to deal with
Other Notes
- If a motherboard has a PCI slot and PCIE slots. there is a good change the debug headers are in the PCI socket, it will not be in both.
- only one of the PCIE/PCI sockets might support debug. This is useful to know.
Another description
- TL631 PRO uses the new 130-nanometer Actel ProASIC3 flash memory series chip with a new pure system.
- Gemini drive module: BGA type driver module, part design.
TL631 Pro interface description:
- LPC1 shared high-speed channel = connect to the motherboard 2.0 small pin LPC interface, 2.0 module
(Module expansion LPC3 interface can connect notebook MINI PCIE conversion card, A-DEBUG conversion card, ASUS notebook DEBUG-CON. EC-DEBUG). - PCI high-speed channel = support all PCI slots.
- LPC2 shared high-speed channel = connect to the motherboard 2.54 large pin LPC interface, ASUS COM-DEBUG. ASRock UART1, MSI JDP, SuperMini SPl.
- PCIE X1 high-speed channel = support Gigabyte without PCI motherboard (other brands do not support).
- 3VSB power indicator, to detect whether the power is normal.
- RST reset indicator, to detect whether the motherboard reset is normal (only when PCI or PCIE is inserted)
- CPU indicator light, to detect whether the CPU module is normal.
- DRAM memory indicator, to detect whether the memory module is normal.
- VGA graphics indicator light, to detect whether the graphics card module is normal.
- PCH south bridge indicator light, to detect whether the south bridge module is normal.
- DP decimal point, CLK signal display.
- DP decimal point, FRAME frame signal display.
- threading hole
Package Contents:
1 * TL631 Pro Diagnostic Card
1 * MINI adapter board
1 set * cables
1 * 2.0 modules
2 * 2.54 modules
TL631 Pro interface description:
- LPC1 high-speed shared channel, connect to the motherboard 2.0 small pin header LPC interface, 2.0 module (module expansion LPC3 interface which can be connected to notebook MINI PCIE conversion card, A-DEBUG conversion card, notebook DEBUG-CON, EC-DEBUG)
- PCI high-speed channel, support all PCI slots.
- LPC2 shared high-speed channel, connect to the motherboard 2.54 large pin LPC interface, COM-DEBUG, ASRock UART1, MSI JDP, Supermicro SPl.
- PCIE X1 high-speed channel, support Gigabyte no PCI motherboard (other brands do not support).
- 3VSB power indicator to detect whether the power is normal.
- RST reset indicator to detect whether the motherboard reset is normal (only when PCI or PCIE is inserted)
- CPU indicator light to detect whether the CPU module is normal.
- DRAM memory indicator to detect whether the memory module is normal.
- VGA graphics indicator light to detect whether the graphics card module is normal.
- PCH indicator light to detect whether the southbridge module is normal.
- CLK signal display, FRAME frame signal display.
Specifications:
- Name: Diagnose Card
- Material: printed circuit board
- TTL631 PRO Full Set
- Item size: 78 * 52mm / 3.07 * 2.05in
- Package size: 150 * 100 * 100mm / 5.91 * 3.94 * 3.94in
- Package weight: 170g / 6.00ounce
Packing List (TL631 PRO Full Set):
- 1 * TL631 PRO Diagnose Card
- 1 * MINI PCIE Conversion Card
- 1 * A-DEBUG Conversion Card
- 4 * Wires
Overview
The Full Kit (get this one)

Warnings
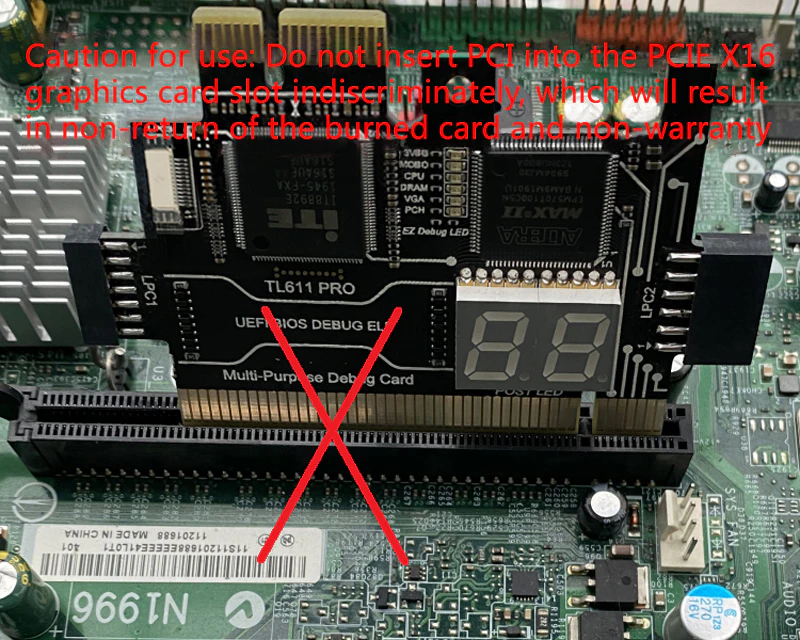
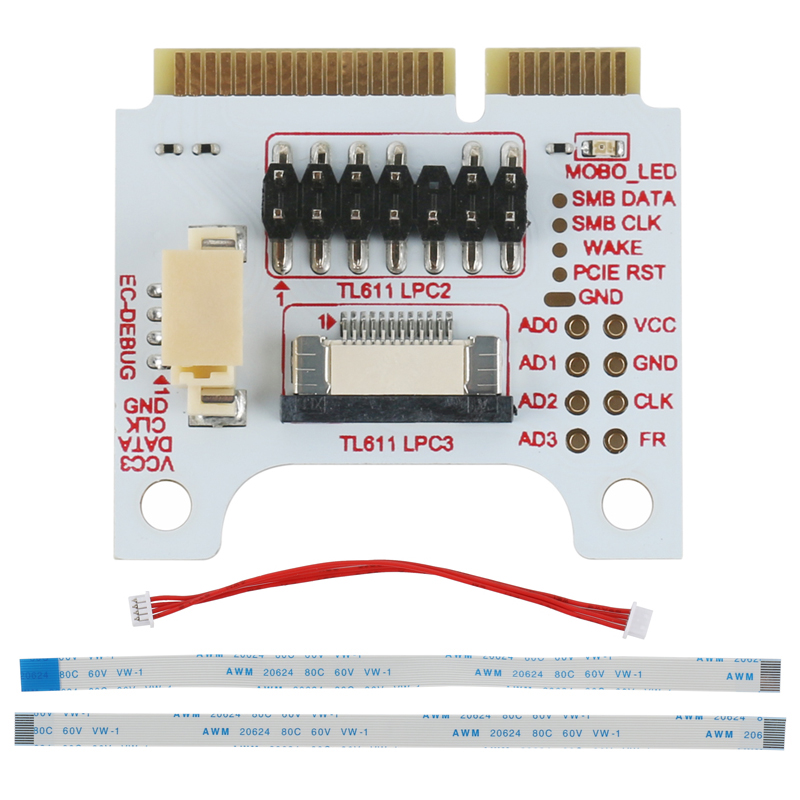
Adapters




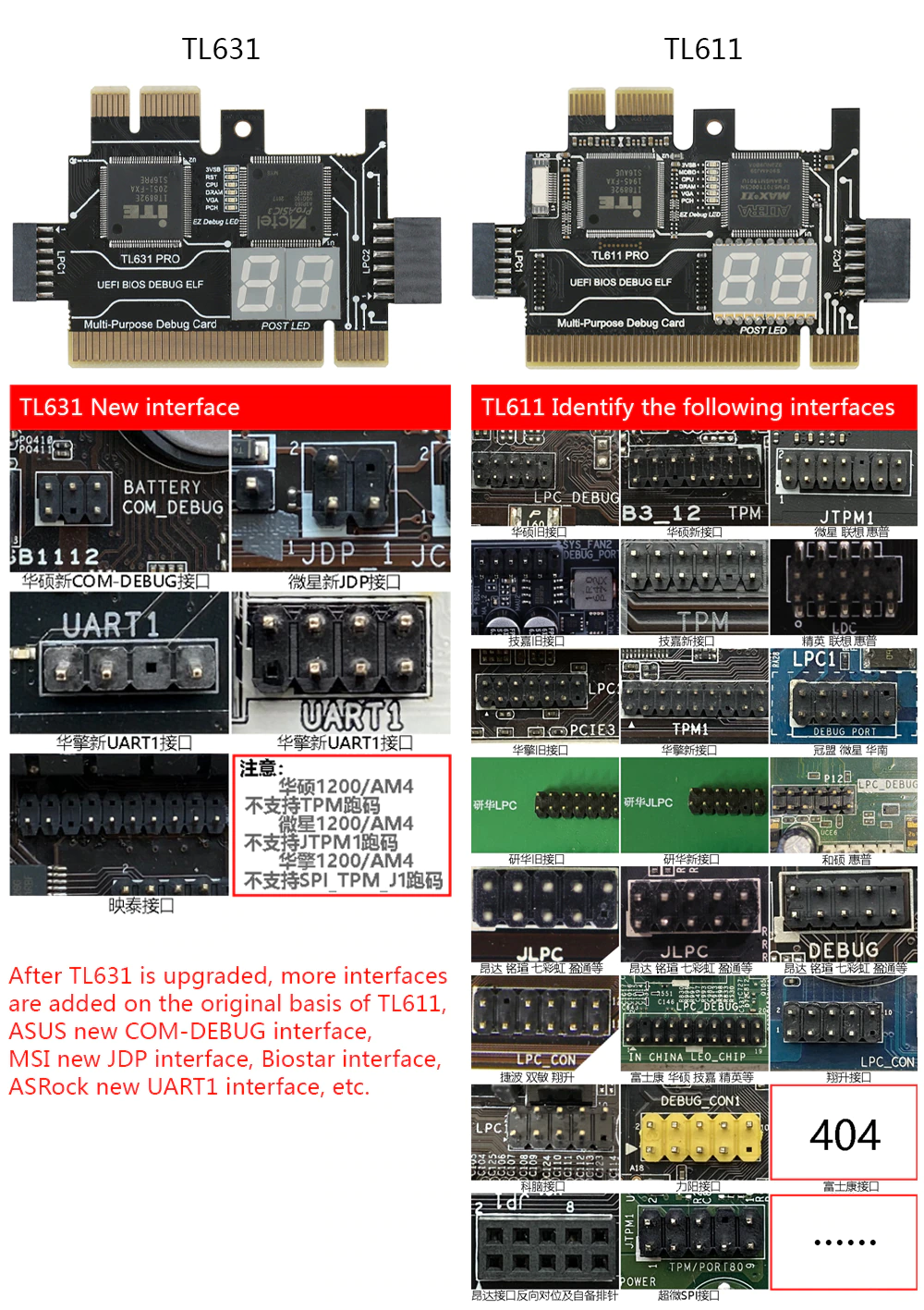
Supported Headers
The TL631 supports all the headers the TL611 did and the new ones.






Identification of Components

- LPC1 shared high-speed channel = connect to the motherboard 2.0 small pin LPC interface, 2.0 module
(Module expansion LPC3 interface can connect notebook MINI PCIE conversion card, A-DEBUG conversion card, ASUS notebook DEBUG-CON. EC-DEBUG). - PCI high-speed channel = support all PCI slots.
- LPC2 shared high-speed channel = connect to the motherboard 2.54 large pin LPC interface, ASUS COM-DEBUG. ASRock UART1, MSI JDP, Supermicro SPl.
- PCIE X1 high-speed channel = support Gigabyte without PCI motherboard (other brands do not support).
- 3VSB power indicator, to detect whether the power is normal.
- RST reset indicator, to detect whether the motherboard reset is normal (only when PCI or PCIE is inserted)
- CPU indicator light, to detect whether the CPU module is normal.
- DRAM memory indicator, to detect whether the memory module is normal.
- VGA graphics indicator light, to detect whether the graphics card module is normal.
- PCH south bridge indicator light, to detect whether the south bridge module is normal.
- DP decimal point, CLK signal display.
- DP decimal point, FRAME frame signal display.
- Threading hole
- This is possibly to attach a cord to be able to pull the card out easier.
LED Descriptions
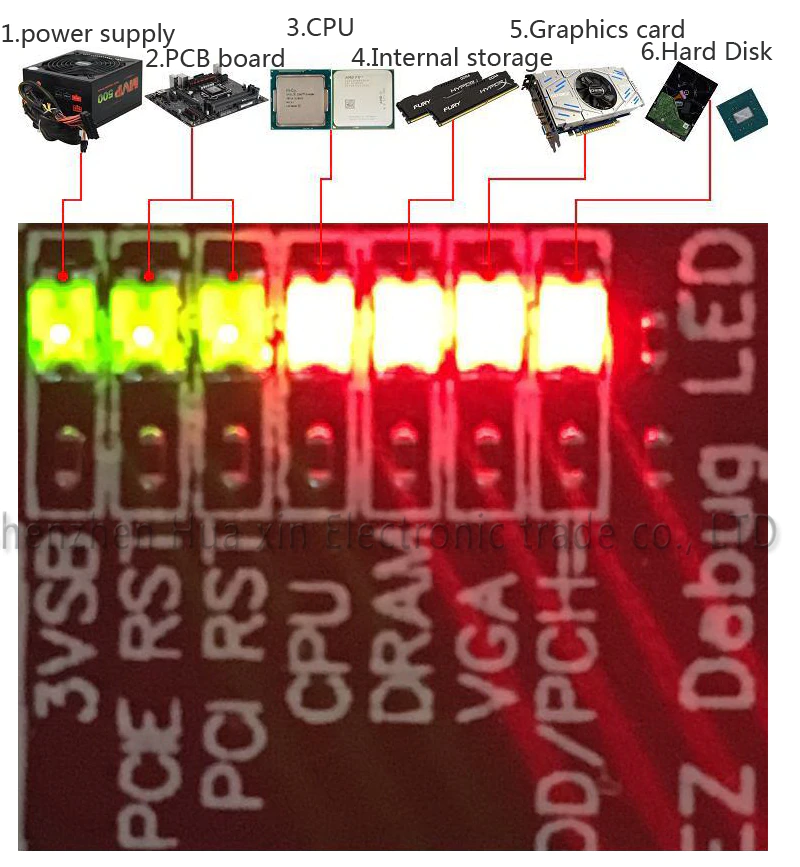
Number 4 is obviously RAM
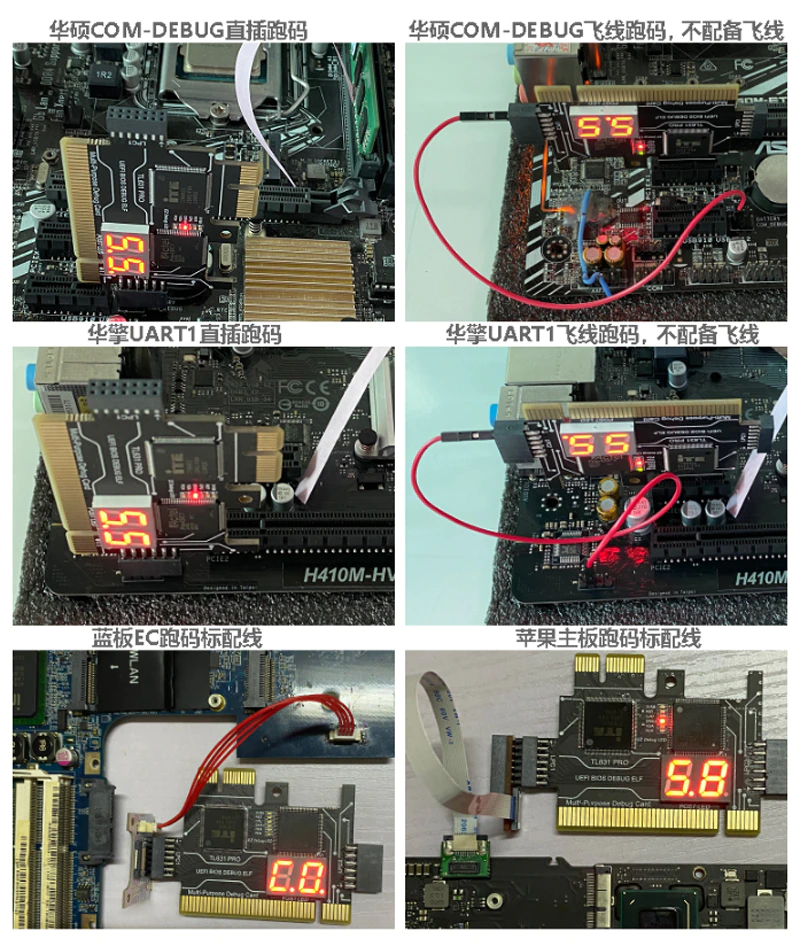
Debugging Examples
I believe are examples of how the device should be plugged in.
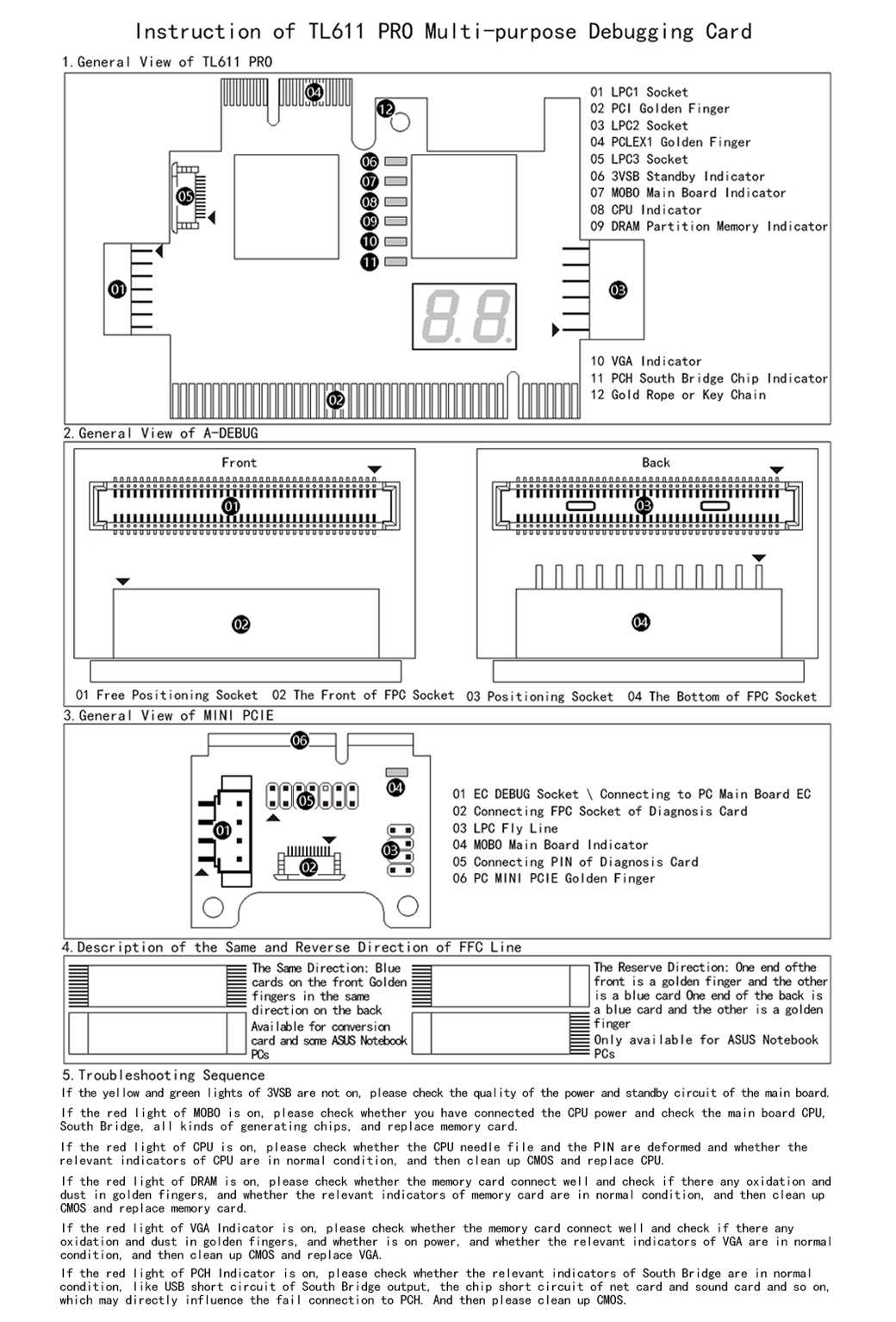
Manuals
This is the English manual for the TL611Pro but is very similar to the TL631Pro.
Page 1 of 2
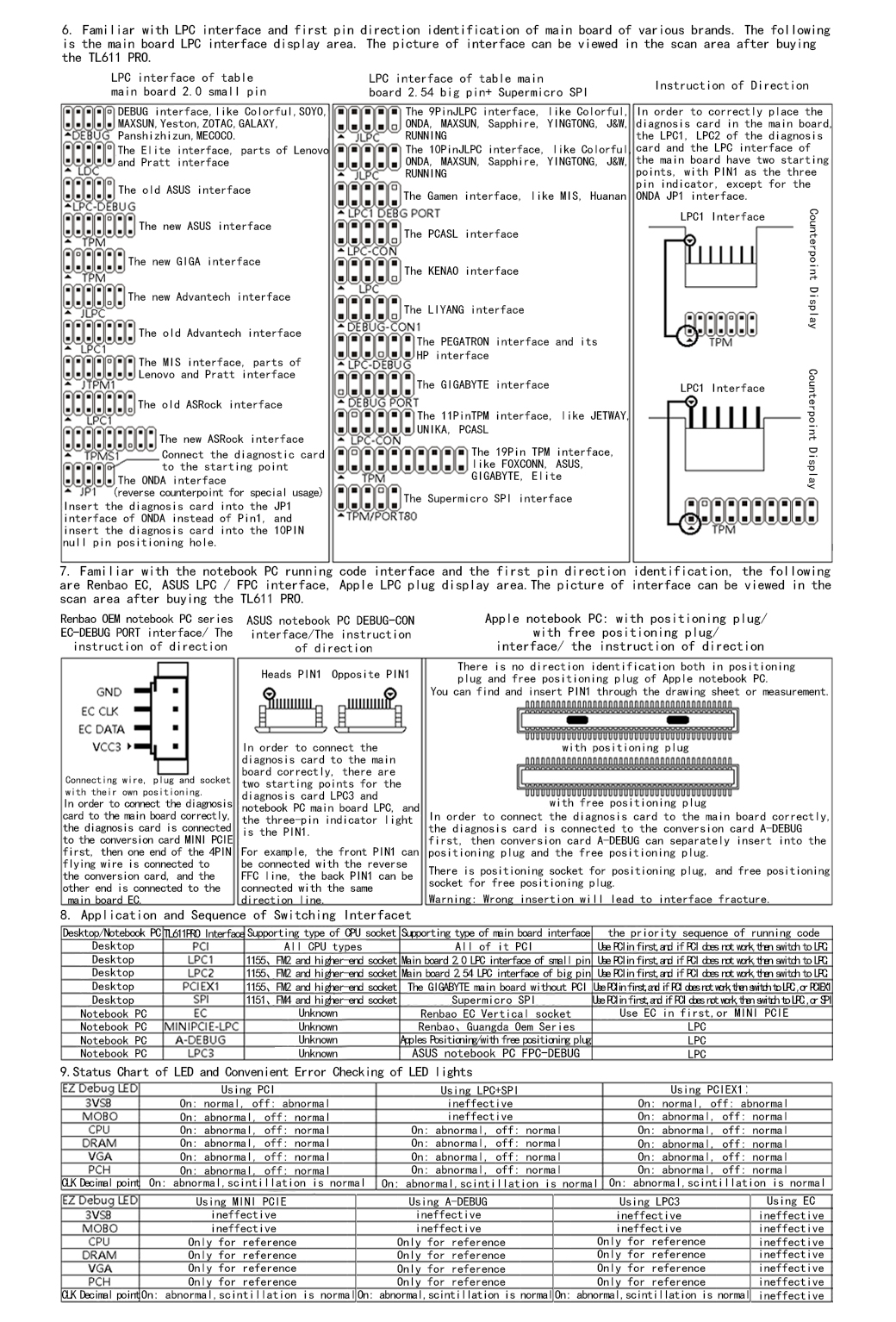
Page 2 of 2
My Home Network Project
These are just some rough notes for my Home network project. There is more information on my PC.
Links
- Suppliers
- Next-Gen Cables - DTECH Cabling Systems
- Level-Up Your Cabling Infrastructure With DTECH Next-Generation Cables. A Leading Manufacturer of High-Performance Cables for AV and DATA Professionals.
- I will buy the XG 40BaseT system from these guys including the cable, keystones and panels.
- Excel Networking Solutions
- Excel Networking is a world-class premium performance end-to-end infrastructure solution – designed, manufactured, supported and delivered – without compromise.
- Made my large server cabinet
- British Based
- Suppliers all categories of cable
- Search results for Cat6a 500m
- Cannot buy from this company directely but their whole catalogue is online with their specs and SKU
- This company suppliers everything and is good quality.
- Data Cables & Network Components | DTTUK
- Data Termination Technology (DTTUK) are leading suppliers of networking cables, computer network cabling, structured cable, data and fibre optic connectors.
- Excel supplier
- Next-Gen Cables - DTECH Cabling Systems
- CAT6A Cable
- Next-Gen Cables - DTECH Cabling Systems - Level-Up Your Cabling Infrastructure With DTECH Next-Generation Cables. A Leading Manufacturer of High-Performance Cables for AV and DATA Professionals.
- CAT 6A F/FTP 600MHZ HDBASE-T DOUBLE SHIELDED 23 AWG ETL LSZH - BS6701 CE - 305M | eBay
- Note this cable is BS6701 compliant. Jacket Colour/Type : BLUE - LSZH (C Grade).
- DTECH Cabling Systems 600MHZ N-Link Plus Category 6A F/FTP S-FOIL. This cable is manufactured specifically to deal with high frequency applications and network tested to perform up to 600Mhz.
- I bought this
- Excel Networking Solutions - Search results for Cat6a 500m
- Connectix 001-003-003-34 CAT6a F/FTP Solid Ethernet Cable Reel, 305m, Black, LDPE (Boxed) - Buy the Connectix 001-003-003-34 CAT6a F/FTP Solid Ethernet Cable Reel, 305m, Black, LDPE (Boxed)
- Cat6A Cable F/FTP S-Foil Dca LS0H 500m Reel - Ice Blue | Comms Express - Excel Cat6A Cable F/FTP S-Foil Dca LS0H 500m Reel
- Bulk Network Cable | Patch Leads | Cat5e | Cat6 | Cat6a - Bulk Networking Cable | CAT 5e | CAT 6 | CAT 6a | Patch Leads | Network Cabinets
- BS6701 | Connectix Cabling Systems
- BS6701: Amendment 1 - 2017. Specification for installation, operation and maintenance
- This is a list of all of the different cable classifications such as low smoke and fire resistance.
- KeyStones
- 100-181-24 - Excel Cat6A FTP Screened Low Profile Keystone Jack Toolless Silver (Box 24) - 100-181-24 Excel Cat6a FTP Screened Low Profile Keystone Jack Toolless Silver, available as part of our range of excel cat6a keystone jacks for RJ45 network connections.
- Excel Butterfly Keystone Jack - Toolless | Comms Express - View our range of Excel Butterfly Keystone Jack - Toolless available at Comms Express, Networking Reseller - Free Delivery Available Buy Online Today
- 100-180-24 - Excel Cat6A FTP Screened Keystone Jack Toolless Silver (Box 24) - 100-180-24 Excel Cat6a FTP Screened Keystone Jack Toolless Silver, available as part of our range of excel cat6a keystone jacks for RJ45 network connections.
- Excel Cat5e/Cat6/Cat6A FTP Shielded/Un-Shielded RJ45 Keystone Jack Toolless | eBay - SKU: #EX-KS-TOOLLESS BRAND: EAN: No aplicable WEIGHT: 0.036.
- Excel Cat6A FTP Screened Low Profile Keystone Jack Toolless Silver Box - Excel Cat6A FTP Screened Low Profile Keystone Jack Toolless Silver (Box 24) 100-181-24
- Excel Cat6A FTP Screened Low Profile Keystone Jack Toolless Silver - Excel Cat6A FTP Screened Low Profile Keystone Jack Toolless Silver. 100-181
- Excel Category 6A Low Profile Screened Keystone Jack • OneStopCable.Shop - Excel Category 6A Low Profile Screened Keystone Jack, is a reduced size toolless termination RJ45 socket. Perfect for using with shutters.
- Excel Category 6A Screened Keystone Jack • OneStopCable.Shop - Excel Category 6A Screened Keystone Jack, is a toolless termination RJ45 socket suitable for mounting in range of housings.
- Excel Category 6A Screened Toolless Keystone Jack 34.3mm • OneStopCable.Shop - Excel Category 6A Screened Keystone Jack is a toolless RJ45 socket suitable for mounting in a range of housings
- Patch Panels
- Excel 24 port 1U Unloaded Black Keystone Frame - Supplied Unloaded - Excel 24 port 1U Unloaded Black Keystone Frame - Supplied Unloaded - Available at Comms Express, Networking Reseller - Free Delivery Available
- ETS 24-Port CAT6A FTP Shielded 1U Patch Panel 19-Inch Loaded w/Tool-Less Keystone Jacks Rackmount or Wallmount | Amazon
- Excel 24 port 1U Unloaded Black Keystone Frame P/No 100-026 - Excel 24 port 1U Unloaded Black Keystone Frame P/No 100-026
- HDBaseT
- HDBaseT | Home - The ProAV industry’s premier multimedia distribution technology up to 100m/328ft over a single, standard Category cable.
- About Technology - HDBaseT - Extend fully uncompressed Audio, Video, USB, Gigabit Ethernet, power, and control up to 100 meters/328 feet over a single, standard Category cable.
- 40GBASE-T in Data Center Networks - Softing IT Networks - Data center network infrastructure is witnessing a transformation, driven by growing bandwidth and network performance demand.
- Cat8 Cable for 25GBASE-T and 40GBASE-T Network | FS Community
- What is the Cat8 cable? What are 25GBASE-T & 40GBASE-T and why choose Cat8 cable for 25G/40GBASE-T network?
- As you know, with the increasing bandwidth demands, choosing the right cabling is significant in future-proofing data centers, server rooms or other places for requirements that lie ahead. Nowadays, Cat8 cable is regarded as a new option for emerging 25GBASE-T and 40GBASE-T networks. Then, what is Cat8 cable? What are 25G/40GBASE-T and why choose Cat8 Cable for 25G/40GBASE-T network? Read this post to find answers to these questions.
- HDBaseT through UniFi Switch | UniFi
- HDBaseT isn't Ethernet, it just uses the same cabling (and can fall back to Ethernet). If you plug HDBaseT into an Ethernet switch, it switches to Ethernet Fallback Mode, which disables all the HDBaseT signals. Where you need HDBaseT, you can't pass it through any Ethernet switch.
- SW41HDBT — Blustream - 4-Way HDBaseT™ / HDMI Input Switch - 4K 60Hz 4:4:4, Simultaneous HDMI / HDBaseT™ Output, Manual / Auto Source Switching, PoC to TX & RX, Audio Breakout, Web GUI with CEC Source & Display Control
- HDMI over IP
- What Is HDMI over Ethernet and How Does it Work - HDMI over Ethernet, also called HDMI over IP, uses an existing ethernet infrastructure to distribute HD video signals from one source to an unlimited number of screens.
- HDMI Over IP Receiver for ST12MHDLAN - HDMI® Extenders | StarTech.com - HDMI Video Over IP Gigabit Ethernet Receiver for ST12MHDLAN
- Misc
- kwmobile F-Type Keystone Modules (Pack of 12) - Snap-In Patch Panel, Patch Bay Keystone Jacks for DVB-S, DVB-S2 F-Type Coaxial Cables | Amazon
- Everything You Need To Know About Coaxial Cable | RS - Everything You Need To Know About Coaxial Cable | RS Components In our comprehensive guide, we look at what coaxial cable is and what it’s used for, the different types of coaxial cable that are available, and compare it to other types of cable for completing various tasks.
- TV Aerial + HDMI + CAT6 Socket - Clear White – Corston - A combi utility socket
- TV over Ethernet
- METRONIC TV Cable for RJ45 Wall Socket - Coaxial Male/Male 5 M white | Amazon - Ethernet to coax cable
- 1pcs Rj45 Male Plug To F Tv Female Jack Rf Adapter Connector Coaxial Barrel Coupler High Quanlity - Connectors - AliExpress - Smarter Shopping, Better Living! Aliexpress.com
- Digital Antenna over ethernet? : networking
- Can I run an amplified coaxial antenna signal from this antenna/amp over cat5? I want to put the amp in the basement on the other end of this cat5 and use some sort of converter to get cat5 to the coaxial (preferably without power) outside at the antenna.
- Coax Cat 5 Balun is the search term you probably want.
- A balun is going to be the easiest and cheapest solution. Effectively it is just an adapter so you can send the TV signal over the cat5.
- Shielded Cat5 Balun II, Twin Pack - 500306 - 2PK | CPC - The shielded CATV balun allows RG6 coaxial cable to be replaced by Cat 5e/6/7 STP or UTP cable in the terrestrial RF environment.
- Satellite over ethernet
- Question - Sky Coax over Ethernet | AVForums
- To be clear you wish to run satellite down feeds from the LNB over cat6?
- As I understand it there are whole load of technical reasons why you can’t, that people more knowledgeable than me can probably explain.
- LNB signal over cat5e is it possible??? — Digital Spy
- I have a customer who has a fully cat5e wired house and wants a freesat plasma installing in the bedroom but the only problem is getting the satelite feed to the screen, there are two cat5e sockets behind the tv as the house currently has a scion system running in it, it is not practical to run a coax, and i was wondering if there are any baluns out there( i have searched with no luck) that any one knows about that would carry the signal over cat5e?
- You can't run a satellite LNB feed over cat5e
- But you CAN run RGB video over cat5e, so could you locate the satellite box at the comms rack and get a coax feed there
- Question - Sky Coax over Ethernet | AVForums
My Atari ST Notes
These are my Atari ST notes
- Websites
- Atari-Forum - A forum about Atari 16/32 computers and their clones. This forum is in no way affiliated with Atari Interactive.
- General
- Skip Long Memory Test - On TOS 2.06 to bypass the long memory test, just press any button.
- Atari ST Documentation Written/Modified by DrCoolZic - This page groups most of the documents that I have written under the name DrCoolZic or Jean Louis-Guerin.
- Emulators
- Steem Engine
- The Steem Engine is a free Atari STE emulator made with ease of use in mind.
- This is not updated anymore
- STeem SSE download | SourceForge.net
- Steem SSE ('ST Enhanced Emulator Sensei Software Edition' in full) is an updated version of Steem. Features have been added and emulation has been improved.
- The menu is hidden, press Alt to unhide it.
- The keys you need to know:
- F1: help (when not running)
- F11: mouse control
- F12: start/stop
- Alt: classic menu (when not running)
- Page Up: ST Help
- Page Down: ST Undo
- The code execution cannot proceed because d3dx9_43.dll was not found.
- ReInstalling the program may fix this problem.
- How to Restore a Missing DirectX DLL File - Need to restore a DirectX DLL file? This is a common problem with games. Learn how to restore the file properly from the DirectX installation package.
- How to Fix D3dx9_43.dll Is Missing or Not Found Errors - D3dx9_43.dll Not Found errors usually indicate a DirectX problem. Don't download d3dx9_43.dll, fix the problem the right way.
- Download DirectX End-User Runtime Web Installer from Official Microsoft Download Center - The Microsoft DirectX® End-User Runtime installs a number of runtime libraries from the legacy DirectX SDK for some games that use D3DX9, D3DX10, D3DX11, XAudio 2.7, XInput 1.3, XACT, and/or Managed DirectX 1.1. Note that this package does not modify the DirectX Runtime installed on your Windows OS in any way.
- Missing d3dx9_43.dll | Microsoft Community - I downloaded World of Tanks, I hit play, it says "The code execution cannot proceed because d3dx9_43.dll is missing". Reinstalling the program may fix this problem. I tried that twice, didn't work. Looked in system 32 folder, there is no d3dx9_43.dll, it goes from d3dx9_24.dll to d3dx9_32.dll.
- How to Fix d3dx9_43.dll Missing Error for All Games & Apps in Windows | YouTube | MJ Tube - Fix d3dx9_43.dll Missing Error in Windows 10/8/7
- Hatari - An Atari ST emulator for Linux and other systems that are supported by the SDL library.
- Easy to use
- Hatari User's Manual - User's manual for the Atari ST emulator Hatari
- F12
- Brings up the menu
- Pauses emulation
- Releases the mouse
- Mouse going all over the place
- This is a typical problem if you don't use the full screen mode
- Press AltGR+m to lock the mouse pointer into Hatari's window. On Mac use the keyboard combination Command+m (Apple key + m)
- You can't click on your OS then but the emulated mouse for the ST will be fine.
- Press it again to release the mouse again to the host OS.
- Steem Engine
- TOS Sources
- EmuTOS
- EmuTOS is a Free operating system for Atari ST computers, and more.
- An open source TOS replacement
- TOS Images collection | avtandil.narod.ru - An extensive list of TOS in both bootdisk and IMG format along with descriptions and proper names, remember Rainbow TOS
- ROMs Atari ST - Atari ST - TOS - [IMG] - Planet Emulation - A large list of TOS
- TOS ROM › :: ATARIworld :: Do The Math :: - A large list of TOS
- Steem TOS - Download a limited set of TOS from here.
- The most compatible TOS is the TOS1.02(UK)
- EmuTOS
- How much RAM
- Use SYSINFO.PRG and this will show technical information of your Atari including TOS and RAM.
- SysInfo - Atari ST - Essential software (The List) - Atari ST - Essential software (The List)
- Atari ST Sysinfo | atarimania.com - Sysinfo for Atari ST
- Test RAM
- YAART - RAM testing program | Atari-Forum - It always bothered me that RAM test software for the Atari was mostly very simplistic in their test algorithms. There are much better ways to find (especially subtle) faults, which are for example used by Memtest86 on the PC. So I ported a selection of these tests to Atari. I humbly named it YAART, Yet Another Atari RAM Test, but I think it provides better test coverage that the usual RAM test software for Atari systems.
- ROM Sources
- Atari ST ROMs | Emuparadise
- TOSEC: Atari ST (2012-04-23) : Free Download, Borrow, and Streaming : Internet Archive - There is a single file you can obtain from the Internet Archives that seems to have every ST program made stored in it
- Atarimania's ST-section! - What you see here is the start of the biggest Atari ST / TT / Falcon030 software database in Atari history. So far we've been working hard on the games section, and work has already started on the utilities and the demos sections too. They do all the other old Atari machines aswell.
- Introduction to the Discovery Cartridge | Info-Coach
- Russ' files
- This is Russ' games and utilities database for the Atari Series of handhelds and computers, you will find many directories including one called Atari ST STX Files, plus lots more , everything that he has collected in the last 3 years is there both in zip files and in downloadable .ST files.
- from here
- exxos Atari Pages
- Magazines, PD and various hardware articles. All ST Format disks and their scans are present.
- Hardware forum aswell
- Other Software
- The LaST upgrade - PART 10 GemBench 6
- For many years GemBench has been one of the best benchmarking apps on the ST. Ofir Gal's last release was GB4 where he was kind enough to allow me to use his source code to update GemBench. After many weeks of work, GemBench5 was born and ultimately GB6.
- Can tell what TOS you are running.
- Might be able to see how much RAM you have.
- NeoBench
- The LaST upgrade - PART 10 GemBench 6
- Hardware
- Atari ST Memory Information - Memory for Atari ST/Falcon/TT computers
My Sweet Home 3D Notes
Thanks to Emmanuel Puybaret for this amazing and free software.
You can buy a version with more models and support the project, a paid version available on the Microsoft Store, automatically updated and bundled with 1500 pieces of furniture and 418 textures.
Sweet Home 3D is a free home design software. It is not developed to be be a full CAD system but aimed for people to do interior design which it does really well.
I had some issues when using this software dues to the feature set or how they are implemented.
These are my notes which will help people new to the software be able to use it and answer all of those question I had.
Getting Started
- Download
- Sweet Home 3D
- Official Model Libraries and import them.
- Official Texture Libraries and import them.
- Download and Install these plugins
- AdvancedEditing: Adds extra functionality to manipulate elements after their creation
- 3D Pan with middle mouse button: Adds 3D image panning and adds a Exponential mouse wheel option
- Wirings: Add wiring to your 3D image. Excellent for networks, central heating and basic electrics.
- ExportToSH3F: This will allow you to make your own Sweet Home 3D models in the native format.
- CopyAsNewFurniturePlugin: Copies the selected objects in plan as a new piece of furniture into the clipboard
- ExportPlanImage: Export plan to image to a to PNG or JPEG format at the size of your choice
- GenerateRoof: - Generate a roof with various slope angles from the shape of the selected room
Read this
- if you are going to do a precise plan
- Backup often, especially before big operations or resize (keep versions)
- Make use of dimension lines to record your true measurements
- When making or editing walls beware of the fact that a wall might be longer than you want so as to allow it to join, and consequently when you delete a wall it might have a different length than you initially expect.
- My Jigsaw method is better for precise plans when you are cobbling them together when going round your house getting random measurements
- Wall thickness is a one you have to be careful about (unless using Jigsaw method)
- Un-joined walls sometimes have a habit of moving or appearing to move, zoom in and out to make sure it is not just a drawing issue
- If you use the resize feature, sometimes assets locations and measurements get messed up. Backup before you use this in any complex scenario.
- When you have created a room sometimes the asset selection can get mixed up and you move something you did not want to.
- Install all the recommended plugins from the official plugin page
- Read the forum, many answers to many problems in easy to read responses
- YouTube has a lot of tutorial videos (many referenced on this page)
- This article has answers to many newbie questions, because i had them and then wrote the answers down.
Notes
These will help you understand home Sweet Home 3D works:
- Official Sites
- Sweet Home 3D / Feature Requests - Request Features here
- Sweet Home 3D / Bugs - Report bugs here
- Sweet Home 3D Blog - Sweet Home 3D Blog with many tutorials and useful articles.
- Sweet Home 3D : Tips - Tips taken from the blog and list for ease of use. Great articles.
- Overview (Sweet Home 3D 7.0 API) - All the functions and API are documented here.
- Sweet Home 3D : Exported homes manager - Based on the Export to HTML5 plug-in, this service lets you upload your Sweet Home 3D files on this web server,
to display their 3D view with any browser compatible with WebGL.
- I feel this that this software is well suited for making 3D models from scratch but has some issues when trying to recreate an already existing building. Once you know the software and the relevant workarounds Sweet home 3D can be quite powerful.
- Get your floor plans right before adding any furniture or adding rooms and also keep a copy of this vanilla floor plan so if you ever make mistakes you can go back.
- By default you can only edit dimensions when creating an object, after that you have to use the mouse
- When you start and finish your first boundary (or subsequent boundaries) of the object/room, i.e. after the second click, immediately press enter and this allows you to edit the dimensions, this one time only
- Select room, In (Plan --> Edit points) you can change the boundaries of the room by changing their points on a room – this is a bit fiddly but you can change things
- Connection of walls is done from their middle.
- This can potential change room areas depending where you join a wall.
- You need to make sure you account for the width of the wall.
- When you change the thickness of a wall, the expansion/shrikage is done from the middle of the wall.
- This can potential change room area.
- This can potentially change the length of attached walls.
- When you delete a wall from a joined wall section the original wall length in not restored.
- When a wall is joined the joining walls are stretched so the centres of the walls meet before the wall is merged.
- Newbies - don't use automatically joined walls as they will not work as you expect if you want rooms with exact areas.
- Read these notes and I would recommend the Jigsaw method
- Cannot pan the 3D view
- Sweet Home 3D / Plug-ins / #39 Pan with middle mouse button - This plugin will solve this issue
- Sweet Home 3D Forum - View Thread - Pan in aerial 3d view
- Panning the 3D view isn't possible.
- This thread has some workarounds
- Straight Lines
- Like most design software, if you hold down the shift key linear objects (i.e. lines) will snap to the perpendicular (right angles)
- Make labels or text smaller
- select whatever object you what it's text to go smaller
- press Ctrl + Shift + Alt + K
- I got this shortcut from the menu (Plan --> Modify text syle --> Decrease size)
- It does not matter if there is not a door that 100% matches yours, same for windows and other stuff. If it is, go on the internet and find one, or make one and then upload it for everyone to use.
- Measurements and accuracy
- The measurement lines must transect what you are measuring, that is why there are two lines indicating the spot
- The software suffers from rounding issues.
- It is not accurate to 1mm because I can have a room with 4 equal sides but with slightly difference lengths on the wall depending on how I measure them. They will only be out by +/-0.2 at worst.
- as some people saying because of the roundings but more like 1cm at best 5mm but with rounding this is reduces accuracy to 1cm
- Figures are not always re-calculated on the fly
- When you measure with the measuring tool, you are measuring the edge and not the middle of a wall.
- How to hide all measurement lines
- This is not currently an option but there is a workaround
- Sweet Home 3D / Feature Requests / #847 Hide text and dimensions
- Add them to a separated level at the same elevation as the level where you want them to appear. Then you can make that level viewable or not. If you already drew your texts and dimension lines, cut them and paste them in that level.
- If lines (or objects) are not level but should be, scroll in and out etc.. and they will be redrawn
- Sweet Home 3D : Translations
- Sweet Home 3D is available in 29 different languages.
- It uses the SH3L format.
- Sweet Home 3D file extensions - The list of file extensions associated with Sweet Home 3D - A free interior design program
- Zoom
- In the 2D plan, if you hold Ctrl and use the mouse wheel it will zoom in where the cursor i. This will be consistent with how AutoCad works
- File Locations (Windows 10 64-bit)
- Install Directory: C:\Program Files\Sweet Home 3D\
- Paid Version Install Directory
- The paid version 6.6.1 doesn't run online and is installed in the hidden folder
- C:\Program files\WindowsApps\eTeks.SweetHome3D_6.6.1.0_x64__y7v7etvrysvmm
- Plugins: C:\Users\username\Application Data\eTeks\Sweet Home 3D\plugins
- Default Furniture Library: C:\Program Files\Sweet Home 3D\lib\Furniture.jar
- Imported Furniture (SH3F): C:\Users\username\AppData\Roaming\eTeks\Sweet Home 3D\furniture
- Default Textures Library: C:\Program Files\Sweet Home 3D\lib\Textures.jar
- Imported Textures (SH3T + others?): C:\Users\username\AppData\Roaming\eTeks\Sweet Home 3D\textures
- Imported OBJ
- An imported 3D model and its icon are stored in .pref files in the folder C:\Users\username\AppData\Roaming\eTeks\Sweet Home 3D
- These files are then referenced in the file C:\Users\username\AppData\Roaming\eTeks\Sweet Home 3D\preferences.xml.
- Merging models in a SH3F file would lead to slower and slower operations when many models are imported.
- General - Under Windows Vista / 7 / 8 / 10, imported furniture, textures, plug-ins and user preferences are saved in the C:\Users\user\AppData\Roaming\eTeks\Sweet Home 3D folder and its subfolders ; user preferences handled with version 2.6 and previous versions are saved in the HKEY_CURRENT_USER\Software\JavaSoft\Prefs\com\eteks\sweethome3d folder of Windows registry.
- Cant Open SH3D file
- Sweet Home 3D Forum - View Thread - Can't open file
- If you use Sweet Home 3D under Windows, check in the subfolders of C:\Users\user\AppData\Roaming\eTeks\Sweet Home 3D\work (where user is your login) if there are some files starting by open and ending with .sweethome3d. If such files exist, copy the most recent one, change its extension by .sh3d and try to open it with Sweet Home 3D.
- If you're under Mac OS X, you should rather search in the subfolder Library/Application Support eTeks/Sweet Home 3D/work of your user folder
- and if you're under Linux, in the subfolder .eteks/sweethome3d/work of your user folder.
- Sweet Home 3D Forum - View Thread - Can't open file
- Opening Sweet Home 3D files for manually editing
- All the native Sweet Home 3D files are ZIP files with different file extensions. Within these files are text files and assets.
- You can open these files by dragging or opening them in WinZip or WinRAR etc.. (not by double clicking though)
- Make 2D plan grid bigger
- Just drag and drop what you want to move. When the mouse pointer is on the border of the plan, it will automatically enlarge.
- 3D View colours don't match those in the 2D view
- Sweet Home 3D / Bugs / #1122 Incorrect rendering of floor color in 3D plan
- Objects color may change in the 3D view according to their orientation towards the light sources and their brightness. You may adjust light brightness in the 3D view modification pane. The color/texture of the rooms is always lighter in the plan because they are displayed half transparent.
- To make the colours look correct you need to:
- Right click on the 3D view
- select Modify 3D view
- Under the 3D rendering section set Light brightness to 50%
- Sweet Home 3D / Bugs / #1122 Incorrect rendering of floor color in 3D plan
- Constant/regular backups as are a must
- The undo i think only has 5 steps. add this at the top
- Store the backups as version so you can go back further if you need to.
- You can set the position of the sun
- Base Plan
- Base plan is a term that includes lockable objects, includes walls and rooms. Anything labelled as windows, doors or staircases are also automatically included in base plan (not movable).
- Other furniture is by default not part of base plan. But you can control by checking/unchecking "Part of base plan" in the furniture dialogue
- When the base plan is locked, only movable furniture can be selected and moved in the plan.
- It's typically used for windows and sanitary.
- The reason for this feature is that you can make the house and then move all your furniture about as you want witout breaking all of your hardwork
- The plan can be locked/unlocked here (Plan --> Lock base plan)
- If you group your windows, doors, stairs or invisible boxes with an object that is not part of the base plan, the whole group can be unlocked from the base plan.
- Elevation, Levels and floors
- You cannot edit a plan's elevation until you have layers
- Walls from the layer below will appear as a greyed out background.
- Constructing the same walls on you new level
- Copy and paste method
- Copy the assets from below
- Create a new level
- Paste
- Delete the unwanted parts.
- Copy from below
- Trace the grey out walls from below.
- This might not be the most accurate especially for complex projects.
- A cross hair will appear when you are aligned with the wall below.
- Not sure how this works for basements
- Copy and paste method
- How to design a split-level house - Sweet Home 3D Blog
- This tip shows how to design a split-level house based on the "shop-house" example.
- A complex example of elevation and levels
- Select (Plan --> Levels --> Add level) to create a new level.
- Level 0 and Level 1 tabs now appear above the plan as show below.
- Level 0 contains what you drew until now in the default level and Level 1 is automatically selected and displayed in the plan
- How to increase ground floor height in sweet home 3d | Youtube | ABJECT SAGA CREATION
- Shows you a basic example of levels and how to change elevation of a floor.
- SH3D Lesson 6 - Basement & Second Floor Levels | Youtube | TJ FREE
- Sweet Home 3D Levels & Images | YouTube | Kingenuity Designs
- Multple Height Floor in Sweet Home 3D | YouTube | SBCODE
- How to do mezzanine floors or just different floor heights in the same room
- Sweet Home 3D Forum - View Thread - Ceiling on lower floor overridden with floor on upper floor
- Probably, elevation of upper level is not enough and equal to height of the lower level. Floor goes down and mixing with ceiling.
Check the elevation of second level, it should be Height of first level + floor thickness of second level
- Probably, elevation of upper level is not enough and equal to height of the lower level. Floor goes down and mixing with ceiling.
- Added a new level and there is space between them
- When you create new level, the default value used for elevation (start height) might not be the same as the value you set for you ground floors height (ie.e your wall heights)
- This default height is taken from (File --> Preferences --> New walls height) so make sure this is set correctly as this is used to figure out how height to place the new level. this can be changed afterwards i thought if you have forgot.
- Level 0 does not have a floor thickness beca\zsue it is the ground and that is about 32km thick.
- Sweet Home 3D Forum - View Thread - Space between levels?
- Most probably the open space is the thickness of the floor.
- Solutions: double-click the tab of the top level, then:
- decrease elevation of the top level, or
- insert a floor.
- If a wall protrudes up into the new level it will not show in the usual grey but will appear as a normal wall on that level, and if you delete it, it will be deleted from all floors.
- Floors will not go in until your create a room so they will appear transparent.
- Manually cut out a hole in the floor.
- Sweet Home 3D Forum - View Thread - Cut outs of the floor
- Q: I'm building a 3 floor building in sh3d and in the middle of the rooms I want to cut out a part of the floor so that you can look from the top floor all way down to the ground floor.
- Q: Is there an easy way to do this as I only found a PDF but this I did not understood. https://www.sweethome3d.com/SVGPathMiniManualForSweetHome3D.pdf
- A: Sorry about the SVG manual, but there is no need to do anything that drastic just for an opening.
- A: Two simpler options spring to mind:
- Draw the floor manually with the floor drawing tool, leaving a hole/cut-out where you want it.
- Import one (or more) boxes as staircases. The boxes should be invisible, which you can get by using an invisible texture (like invisible.png). If you size and lift the box(es) to the ceiling below, they can cut out the hole you need. The boxes are possibly faster to change later, but may be in the way when you work on the ground floor (in which case you can make an intermediate level just under the ceiling just for the cut-out boxes).
- Sweet Home 3D Forum - View Thread - Cut outs of the floor
- Sweet Home 3D Forum - View Thread - Adding a crawl space afterwards
- Q: I am trying to add a crawl space after I have designed the other levels (my mistake). So I added a new level with some walls, set elevation to 0 and added the height of the crawl space as elevation value to the other levels (3 levels). All elements, furniture etc. are now correctly elevated but the walls are not elevated. The walls of the ground floor are e.g. still on the ground (and therefore obscuring the crawl space). They should be on top of the crawl space. I have done houses with basements before (negative elevation) but then I have always started with the lowest level. Now I am trying to add it afterwards. What am I doing wrong?
- A: The height of a wall placed in a level is actually the height you set in its modification dialog box + the floor thickness of the level. May reduce the floor thickness or elevate the level above the crawl space a little more.
- Uninstalling or updating Sweet Home 3D
- Sweet Home 3D Forum - View Thread - furniture library copy
- Imported furniture, textures and plug-ins are not removed when you install a new version and when you uninstall Sweet Home 3D (if you want to delete them, see How can I uninstall Sweet Home 3D? in the FAQ).
- In the case of the portable version, imported stuff won't move automatically and you may have to copy or update some data as explained in the README.TXT of the portable version.
- In the case you are under Mac OS X and moved from the free version to the Mac App Store version, the folder where imported stuff is stored may have to be copied.
- Sweet Home 3D Forum - View Thread - furniture library copy
- How to generate a log
- from Sweet Home 3D Forum - View Thread - SH3D app will not open on Win 10
- type Windows + R keys, type cmd and <enter> (run a command prompt)
- drag and drop SweetHome3D.exe from an Explorer window (probably found in C:\Program Files\Sweet Home 3D or C:\Program Files (x86)\Sweet Home 3D folder) in the cmd window you opened in previous step
- type a space then 2>log.txt in cmd window to obtain a command like:
"C:\Program Files\Sweet Home 3D\SweetHome3D.exe" 2>log.txt
- type <enter>
- The program will fail but this time it will create a log.txt file in your home folder that could contain some useful information to understand your issue. Please copy paste its content here.
- from Sweet Home 3D Forum - View Thread - SH3D app will not open on Win 10
- 3D view
- You can store a point of view and then go to it at a later time. Useful if you get lost.
- Make the Aerial view centered on selection
- (File --> Preferences --> Aerial view centered on selection)
- How can I make the furniture catalogue searchable
- (File --> Preferences --> Furniture catalog view: Searchable list)
- Adding a spot lights
Plugins
- File Format
- SH3P - A native plugin file
- Instructions
- How to install plugins
- Download the plugin file which should have the extension .sh3p
- In windows, just double click the downloaded file
- Restart Sweet Home 3D
- The new options should appear under the edit menu or the feature will be enabled.
- How To uninstall a plug-in,
- Remove its SH3P file from the plug-ins folder of Sweet Home 3D, and restart the application.
- This folder is shown when you double click on any filename of a SH3P file listed in the Plug-ins section of the 'Libraries in use'.
- The latter pane is displayed by clicking on the Libraries... button shown at the bottom of Sweet Home 3D About dialog box.
- (Help --> About --> Libraries --> Libraries in use)
- C:\Users\username\Application Data\eTeks\Sweet Home 3D\plugins
- Get plugin version number
- Goto (Help --> About --> Libraries --> Libraries in use)
- Official Plugin User Guide | sweethome3d
- How to install plugins
- Sites
- Sweet Home 3D - Draw floor plans and arrange furniture freely
- Free interior design software. Draw the plan of your home or office, test furniture layouts and visit the results in 3D.
- Official Website
- This is an excellent resource with links to additional assets and plugins.
- Sweet Home 3D / Plug-ins | Sourceforge
- An offcial Sourceforge website for plugins. All plugins seem to be here.
- Sweet Home 3D : Plug-ins and tools
- This page lists the most interesting plug-ins developed by eTeks or by the developers who proposed them in Plug-ins Contributions Tracking System.
- Not as upto date as Sourceforge.
- Sweet Home 3D Forum - New Versions
- Look in the new version forum area for unofficial or new plugins
- Sweet Home 3D - Draw floor plans and arrange furniture freely
- The Plugins
- Sweet Home 3D Forum - View Thread - Wirings plugin
- This plugin brings to SH3D the capability to draw 3D polylines that will snap to floors, walls and ceilings, directly in the 3D view. This could be useful to draw electrical installations, plumbing, and simple decorations.
- Good for electrics, pipes and probably ethernet.
- Sweet Home 3D Forum - View Thread - Wirings plugin
- Sweet Home 3D / Plug-ins / #39 Pan with middle mouse button
- This plugin allows to pan both the home plan and the home 3D view using the middle mouse button. There are no settings, everything works out of the box!
- Exponential mouse wheel - This options speeds up the zomm in/out massively
- This allows you to use the middle wheel to pan on both the 2D and 3D
- AutoDimensioning
- Adds a menu item which allows to generate dimension lines for the whole plan. Available on the official plugin page.
- AdvancedEditing Plugin
- Resize selected objects, edit room points, connect walls that allow to modify the selected objects in plan.
- Adds the menu items Edit > Rotate, Edit > Move, Edit > Flip, Edit > Resize, Furniture > Elevate, Plan > Edit room points, Plan > Connect walls which allow to modify the selected objects in plan
- 3D dimension lines
- Sweet Home 3D / Plug-ins / #42 3D dimension lines - Download here from Sourceforge
- Sweet Home 3D Forum - View Thread - 3D dimension lines plugin - Forum thread
- This plugin brings to SH3D the capability to draw 3D dimension lines that will snap to floors, walls and ceilings, directly in the 3D view. This could be useful to give precise directives to installers.
- CopyAsNewFurniture
- The purpose of this is to select a group of objects and paste them back into the plan as a single object
- Copies a model as a OBJ so as a consequence strips Sweet Home 3d extra properties such as door and window archs, also it strips the window/door/stairs tags.
- Hot to USe
- Right click on copy the object in the 2D pane
- (Tools --> Copy as new furniture)
- Paste in the 2D pane
- You can now also export as a OBJ if you want.
- Sweet Home 3D Forum - View Thread - Wirings plugin
Walls
Walls are one of the building blocks of Sweet Home 3D. Learn how to use them well by seeing how they work before building your master project.
- Wall Joining functions
- Join walls
- (Plan --> Join walls)
- This allows you to freely make walls and then join them. This is not required if you use the Jigsaw method.
- The walls have to be touching
- The walls do not need to touch on the Center point
- The centre of one of the walls will shift to match therefore changing its length
- Walls might get cut at one end to allow the walls to join. There is always Ctrl+Z
- The order in which you select the wall might affect how the wall joins. All walls are treated as lines in the software.
- The direction of the wall will make a difference to how the wall is joined.
- It joins two walls, keeping the parts, but forming an elastic bond.
- Usage
- Make sure the walls are close together (obviously)
- Select both walls
- Use (Plan --> Join walls)
- If you use the wall join tool then you can have some of the following issues.
- There are some weird effect when using the join tool, such as if a wall is longer than your room then it will get truncated (cut down), which is easy to fix, just add another wall on to it. You would generally come across this while messing about but it is not a big thing.
- The other issue is if the wall direction is not compatible, so if you join 2 walls of your room and it goes wrong, undo the change, reverse the direction of one of your walls and re-join.
- Once you have connected all of your walls, you can then use the room tool to create a perfectly sized room. This them makes it easier to start to build the rest of your house as generally the wall builder will work as expected from now because you always have a wall to work from.
- If you have to ever replace a wall for instance because you made it thicker due to an earlier mistake, remember that joined walls join in the middle. So this is a good reason not to join the walls until later.
- Connect walls
- (Plan --> Connect walls)
- This is similar to how using create wall tool is and extensively will allow you to join the walls together so they behave in the same way
- The order in which you select the walls makes a difference, the first walls selected will move to connected to the second wall selected.
- The end of the first wall will connect to the beginning of the second wall
- First a rotation will occur to align the walls, then an elongation (possibly shrinkage) will occur so the walls can marry up
- It joins two walls, keeping the parts, but forming an elastic bond.
- The main difference between this and the Join walls tool is that this tool will move and alter the first wall to meet the second wall as required.
- Usage
- Select both walls in the correct order
- Use (Plan --> Connect walls)
- Join walls
- Cannot join walls – they always go funny / don't have smooth connections.
- Walls can be joined only at their ends.
- Zoom in to see what is going on
- Disable/Enable Magnetism might help
- The walls are probably not aligned with each other so that is why the join appears off.
- The directions of the walls might need to be in the same direction.
- Split the wall and re-join
- this might cause you to have more wall segments (not sure)
- Rooms can cause issues with walls connecting, so delete the rooms and see if this fixes things.
- How to edit a wall
- Select the pointer arrow/cursor from the menu
- Press Ctrl + Shift + E
- This brings up the modify wall.
- This in combination with multi-selecting walls allows you to edit many walls at a time i.e. setting exterior wall sizes
- Split Wall
- Sweet Home 3D Forum - View Thread - Join walls
- The easiest way to really split walls and remove the joint (in my view) is to split a wall in three, then delete the middle part, and reconnect the remaining parts. Then, by hand, you correct the coordinates to where the split/joint should be.
- Sweet Home 3D / Feature Requests / #848 Detach walls
- There is no detach wall option.
- The workaround for this feature isn't so difficult:
- Cut and paste the wall you want to detach
- then select with the Shift key pressed the wall you want to keep it attached to
- and... join them again.
- Sweet Home 3D Forum - View Thread - Join walls
- Stretching Walls
- Select the wall with the cursor tool and then move your mouse over the end of a wall where it should change into a cross hair, then click and hold and alter as required.
- If the wall is only anchored at one end it will lengthen or shorten against this anchor.
- If you resize a wall at a joint you will actually be altering 2 walls against their relative anchor points.
- When you stretch a wall, it will show you the real values of the wall. A lenght of a wall can be longer than its sides in a room, but this issue might only occur when using un-joined walls, I have not tested this aspect.
- Moving Walls
- Select the wall with the cursor tool and then move your mouse over the middle of a wall where it should change into a 4 way arrow icon, then click and hold and alter as required.
- This will keep the wall in the same orientation, Height and thickness but when you move it it will alter the parent (or connected wall) accordingly to allow you to move this wall with out changing its shape.
- Putting a curve in
- Select the wall with the cursor tool and then move your mouse over the single blue arrow icon in the middle of the wall where it should change into a 2 way arrow icon, then click and hold and alter as required.
- Tutorials
- Sweet Home 3D - How to Connect walls | YouTube | Vedran - You will see two methods to join walls in Sweet Home 3D and this tutorial shows you how to use them.
- Sweet Home 3D How to Join Walls | YouTube | SBCODE - A quick tutorial on how to join walls in Sweet Home 3d.
- Sweet Home 3D Create Walls and Rooms | YouTube | EdTech 536 - Tutorial on how to create walls and rooms in Sweet Home 3D.
- Glass Wall
- Sweet home 3D - Glass wall | YouTube | RedTop Learning
- How to make a part of the oval shaped wall entirely out of glass using Sweet home 3D.
- And how to save it for future re-use
- Sweet home 3D - Glass wall | YouTube | RedTop Learning
- Measurements and accuracy
- Draw lines with the cross hair tool and use this to help make your walls, all other measurements seem to be inaccurate. Also zoom in when you do this as the lines will not be precisely placed.
- The figures that appear when you stretch a wall or use cross hair dont seem to be accurate, actually draw a line with the cross hair tool to check the value of a walls length etc..
Rooms
- Create your rooms with double click after you have added all your walls, chimneys and weird shapes into your 2D plan.
- If you have created a room and then added doors and windows, you should recalculate all the rooms so the room flows under the door to prevent tearing in the 3D view and get more accurate square footage. Do this by
- Cut room
- Create room again with the room tool
- Paste style
- Add the room name in again
- When you hit an absolute corner of a wall, the cross hair will become highlighted in a blue circle, which is useful.
- Create a room
- Option 1 - Enclosed area already created
- The area must be enclosed.
- Selected the room tool
- Double click in this area and a room will be created
- NB: Note also that a room created with a double click will include the half doorstep of each door placed on its walls. This feature ensures rooms join each other correctly in the 3D view when the doors between rooms are opened.
- Option 2 - Draw a room
- Select the room tool and draw a room as required
- At each corner (or end of your room's wall) you should click to continue to the next point or you can press enter to add more precise measurements.
- To add walls just double click on the new room
- Select the room tool and draw a room as required
- Option 1 - Enclosed area already created
- Room tool general
- Automatically created walls will all be joined together
- If you try and make the walls thicker it will reduce the area within the room because the thickness is expanded/shrunk equally from the middle of the wall.
- Quickly put walls around a room
- Select wall tool
- Double click in the room
- Issues with creating a walled room with a set area
- Sweet Home 3D Forum - View Thread - Length of a wall
- Wall length is measured from middle of wall.
- For rectangular walls, the maths is straightforward:
Inner length = Wall length - wall thickness
Outer length = Wall length + wall thickness
- Sweet Home 3D Forum - View Thread - Problem with wall thikness and room surfaces.
- This describes an issue I had where i made a room, automatically created walls but then increased the thickness of a wall which reduces my room area which can be confusing. Look at my Jigsaw method to get around this limitation.
- This discussion is as old as SH3D. It has been going on in various ways with suggestions for all kinds of solutions. However, none solves all problems, none is as intuitive as the current procedure.
- Note that SH3D isn't meant to draw architectural plans of houses. There are other programs better suited for that kind of work.
- Sweet Home 3D Forum - View Thread - Set walls by interior dimensions?
- Brand new to this program but want to make a layout for my house. The question I have is, what's the best way to do a room layout. When I measure my walls, I'm obviously measuring the interior dimensions. When I draw a wall and drag to the length of wall I want, it seems to mark the middle of the wall at that point instead of the edge of the wall.
- Sweet Home 3D / Feature Requests / #1059 Demanding adjustment of wall thicknesses
- This is a feature request to allow the live editing of a wall thickness with the ability to select an anchor point for the expansion or shrinking of the girth.
- Sweet Home 3D Forum - View Thread - Length of a wall
- Rooms do not recalculate area when you add things like chimneys (walls) in or alter the wall configuration. So I would generate the rooms last or at worst delete and re-add but don't do complex styling and you will be fine either way
- Moving room labels
- Hover over the room blue manipulation arrows until the cursor to changes to a cross hair (cross in a square box), you can now drag and move the label.
- Recalculate Room areas
- There is currently not inbuilt option to do this.
- Sweet Home 3D Forum - View Thread - Recalculate Room Points
- Official workaround
- cut the room
- create the room with double click
- (Edit --> Paste style)
- You will need to add in the room name again
- If you do not use the auto room tool
- then where the doors are, the ground will be seen so if you use grass for the ground you will appear to have a green floor.
Create a room with a specific floor area and different wall thicknesses
Like most people I went around my house with a measuring gizmo and measured the rooms and walls because I do not have the blueprints but will use the rooms and their measurements to build a complete model of my house with correct dimensions for use with future projects, and yes, interior design. My house is old and has different thicknesses of walls.
These instructions are based on my rooms all having straight walls at 90 degrees. The methods will translate to odd shaped walls but that is outside the scopes of these instructions.
Using your floor plan as a background image can help when drawing your rooms but is optional. See this video How to design rooms from their inner dimensions | YouTube | SweetHome3D
These are the available methods below with their pros and cons.
Method 1 - Room Tool
Great for making a room with walls that are all the same. Can be used as a base for making rooms with different wall sizes but will require some extra work.
- Create a room with the create a room tool.
- Then select the wall tool and then double click on the room so it will add walls to that room.
- The walls are created using your default wall values set here (File --> Preferences)
- Once you have created your walls for this room, you might consider changing these values back to your preferred defaults.
- The room is now created with well placed walls all with the same thickness and height.
- Now because the room I have has different wall sizes, I need to edit the thickness of one wall to match the real values
- Altering the thickness of an attached wall
- The thickness is increased from the middle of the wall and you cannot control the anchor point, this means if you alter one wall's thickness as the room area will no longer be correct because the wall will expand into the room.
- You need the need the ability to set an anchor point before altering the wall's thickness.
- I have updated an issue at sourceforge for this. p.s. I would not use the word demand but did not want to create a duplicate issue.
- Delete a wall so you can put another wall in place with a larger thickness
- You will find that the remaing walls (where the deleted wall was attached) are longer than you expect because because they were joined in the middle rather than being side by side. This allows for angled joins.
- This is fine
- Reduce the protruding walls by half of the thickness of the wall you just deleted and the walls will then end where they should.
- Create a wall to match you specs elsewhere and then drag next to the protruding walls of your room.
- You will need to select this new wall and the 2 other walls and perform a join on them using (Plan --> Join walls)
- The walls must be placed next to each other.
- Remember that wall direction can affect how the walls connect.
- Inspect the wall lengths are correct and alter as required.
- Altering the thickness of an attached wall
Method 2 - Manually draw walls around the room
This method can be tricky to get the room dimensions right.
- Create a room with the create a room tool (optional but makes placement a lot easier)
- Manually draw the first wall against the bottom of the room making sure it is correctly placed.
- Setting the required thickness
- Press enter after drawing the line.
- Use the zoom function to make sure the placement is precise.
- Be aware that when you draw the wall your cursor is following the middle of the wall not an edge.
- Setting the required thickness
- Draw the second wall starting at the corner of the last and repeat this until you have done your wall.
- Follow the procedure as for drawing the first line (thickness and placement)
- When you get to the exact corner, the cursor will will show vertically and horizontal lines.
- There seems to be no way to stop walls snapping together so they can be altered before putting in place.
- Is there a way to disable walls automatically joining so they can be treat as separate entities allow thickness change until I want to join them? so they can be treated independently.
- Now because the room I have has different wall sizes, I need to edit the thickness of one wall to match the real values
- See Method 1 for reasons why you cannot use this to create a room with different wall sizes
Method 3 - Jigsaw (wall by wall)
This method allows you to build your house will all independent walls (or as required) giving you the most freedom to alter wall thickness without affecting any other wall. This is my preferred method because I did not know the thicknesses of my my house and had to change and alter them as a I went along.
This method prevents any distortions caused by changing thickness when building you room and also prevents automatic joining.
I currently have only ever used this to make my house which has all square rooms and is why I have included the methods above as-well just in-case one of those is a better fit. This method is a lot more fiddly because you constantly have to use the zoom to make sure walls are where they should be. I have found that wall measurements are not as precise as they should be but i don't know if that is because of using this non-standard way of joining walls.
- Make sure magnetism is disabled.
- Create a wall of your desired thickness, length and height, not on your floor plan where you are going to build your room but a temporary area.
- Move this wall to your the area you are building your room and place as appropriate
- Place a dimension line for the second wall
- I used dimension lines extensively during my build period. It allowed me to make an accurate plan and see any discrepancies I missed.
- Create your second wall
- Place the second wall next to the first wall which you are are connecting to
- Joining/Placing the wall
- Using the mouse move the wall over to your build area
- Use the cursor keys to move the wall in to it's final position which is when the walls appear to join
- When the walls are close but not touching you will see a single black line, but if you keep moving them closer the line will disappear and the walls will be joined.
- press cursor once, click off and see if joined, if not repeat
- You might need to add a small amount to each end of the wall to make internal walls join but keep their required length for the room.
- I recommend 0.1mm additional on the walls length to allow the overlap, however this is not always needed. 0.1mm is within the calculation tolerance of this software so is not always needed.
- If you have longer overlaps I don't this this will break anything as long as they are not too long.
- Don't worry this is not an elastic bond (permanent join)
- When the walls are close but not touching you will see a single black line, but if you keep moving them closer the line will disappear and the walls will be joined.
- Check the walls length
- Use the dimension line you drew earlier to check
- Sometimes due to this merging the wall will actually loose some of its length
- You can stretch the wall normally to make up the shortfall
- If the you are building a square room, 2 walls of the room will be longer to allow for the thickness fo the other 2 walls to maintain a correct internal area for your room.
- Only the dimension tool seems to be accurate, the rest of the figures move about because of rounding (and I am sure other mathematical calculations)
- Repeat and place your next wall
- When you have built your 4 walls (room), you can create a room by selecting the room tool and then double clicking in the middle of your 4 walls.
Notes
- This requires you to put a bit more maths in to your build and what I mean by that is that you need to take into account the thicknesses or not of other walls you are going to connect too.
- Because the walls don't snap together you need to check the joins are next to each other. I also would not be in a rush to join them if not needed.
- The walls are joined but do not sufferer any of issues when joined automatically.
- You can delete a wall and re-add a thicker wall and there is no shift of the join points.
- What I would say is to just check the actual XY coordinates in the wall properties
- I have founds sometimes after a save or moving around some of these walls move fractionally and then appear out of place. This is possibly because the on-screen rendering is not quite as accurate as what is stored. As you must appreciate we are not using the automatic tools here so this logic might not be as well looked after or needs work.
- I would always keep my external walls as separate, this allows for easy adjustments.
- Sometimes a room is sealed even thought it shows it isn't, this is because Sweet Home 3D works with a 1mm tolerance
- These thread helped me
- Sweet Home 3D Forum - View Thread - Some notes after first usage
- This outlines the problem I had and that still needs to be fixed programmatically once a method is figured out
- Sweet Home 3D / Feature Requests / #750 Draw wall by know dimensions from inside or outside room, alignment and capture
- Sweet Home 3D Forum - View Thread - How to draw precisely -mini tip
- This is similar to my method but not the same
- I struggled to follow the whole process here.
- The resize option is for the length of the wall and not the thickness
- Sweet Home 3D Forum - View Thread - Some notes after first usage
- Once your floor plan is complete use the join tool
- Walls can be joined only at their ends.
- you can probably use the join tool on all your walls which might help with automatic value calculations.
- joining walls once you are done prevents the plan walls breaking (If you use longer overlaps this is less likely)
- If you walls are now joined and you delete one you will still have context so replacing the wall is a lot easier.
- Make Walls transparent
- How to show interior parts hidden by walls - Sweet Home 3D Blog - You want to show the external structure as well as the interior parts of the beautiful home you designed? Or more simply, do you need to view inside a small room where walls hide its interior?
- Sweet Home 3D Forum - View Thread - cut holes in the floor for the image rendering
- Read the full thread for all of the information
- Q: I modeled a house. I would like to cut the model for the render. The invisible box is not working, playing with the walls is a little bit time consuming. Are there any other way to do that (like the invisible box was)?
- A: You could import and use one or more large invisible boxes to cut the walls they will intersect, as in the file attached to this post.
Don't forget to select the Door or window at the 3rd step of the import furniture wizard, and then disable magnetism when you move the box so the program doesn't try to place the moved box on the closest wall. Note that those boxes will cut only walls and not other doors and windows, and if you import an invisible box as a staircase it will similarly cut all the floors. - SweetHome3DExample3WithCutWalls.sh3d
Method 4 - Using Dimension lines
- How to make 3D Floor Plan in Sweet Home 3D Best method (Modeling) | YpuTube | SCIENCEMAN
- I found this video (not english) where the man draws his rooms out with dimension lines and then draws walls around them.
- This is an easy method but will have all the downfalls of elastic bonds.
- Will only work for rooms with straight walls
- This method is just put here for reference
Furniture / Objects
- Supported Formats
- SH3D - Project file
- SH3F - Native furniture/object library can have a single or multiple models in it.
- External formats supported - OBJ, DAE, KMZ, 3DS or ZIP containing said formats
- COLLADA files use the .dae extension, which stands for digital asset exchange. A COLLADA file can store a diverse range of content, including images, textures, and 3D models.
- Can export to SVG but I am not sure why you cannot import them
- Downloads
- SVG Path Mini Manual For SweetHome3D.pdf - Helps you with technical aspects on making your own objects.
- Sweet Home 3D : 3D models import
- Download and import models for Sweet Home 3D official download page
- Also a variety of external links to other resources.
- Sweet Home 3D / 3D Models - Official model collection on Sourceforge
- Sweet Home 3D Forum - List Attachments - Search the post attachments on the Sweet Home 3D forum for models.
- Sweet Home 3D : Search free 3D models - Search a 3D model among more than 1400 objects
- Articulated mannequin
- is in the 'Miscellaneous' category and is called 'Mannequin' and is already included in Sweet Home 3D.
- How to customize mannequins | YouTube | SweetHome3D
- Customization for the Forensic Police - Sweet Home 3D Blog
- Many extra assets that the French Police use for making their crime scenes
- Download them from this page however some of the assets are on the standard download page.
- Free 3D models for blender, sweethome3d and others | Blogscopia
- ArchiBit Generation s.r.l. - 3D models - Free 3D models but NOT for commercial use
- Importing
- This is a useful option
- Some things like windows and door opening arcs are only stored in teh Sweet Home 3D native formats.
- Sketchup previews look like pencil drawings, but when you import into sweet3D they look normal.
- Just make sure you use a compatible file type such as Collada (.dae)
- If you have the 2D pane selected then your import will go directly to the plan and will only be saved in the library if you select the option 'Add to catalog'.
- If you have the libraries pane selected (it does not mater which folder or item) then the model will be imported into your library
- Imported furniture can be recognized easily, because the names are in italic font.
- Imported Models not showing
- The model ID needs to be unique.
- If this is a SH3F fiel you have created from other SH3F assets then it is lekly you have not changed their ID
- This can be done via the Furniture Library Editor
- (Edit preferences --> Furniture ID:) set to `Editable`
- Edit the model ID
- Save and re-import the SH3F
- Cannot import models
- Sweet Home 3D Forum - View Thread - Uploading my own models from Tinkercad and Blender to Sweet Home 3D -
- I have created my own 3D model with Tinkercad, and I exported it as an OBJ file, but the furniture import wizard refuses to let me import it.
- Just open the MTL and remove the line "illum 0.0"
- illum is supposed to be followed by an integer not a decimal number.
- Sweet Home 3D Forum - View Thread - Import *obj - files created MS 3DBuilder not possible
- I tried to import furniture created with MS 3DBuilder. But SW3D displays only an error message that the *.obj-Files has a wrong format.
- OBJ and MTL files can be edited with any text editor.
- OBJ file specification
- MTL file specification
- Sweet Home 3D Forum - View Thread - Uploading my own models from Tinkercad and Blender to Sweet Home 3D -
- Export the whole 2D plan as an SVG
- Right click on the 2D plan
- Select 'Export to SVG format'
- choose where to save it.
- Export an object from the plan
- You cannot export directly from the library, use Furniture Library Editor for that.
- There will be 2 files created
- .obj - The vectors of the object
- .mtl - The materials file, stores colours and textures etc.
- How to
- Select the item you wish to export on the 2D plan
- Go to (3D view --> Export to OBJ format)
- Choose where to save it.
- Currently the export will strip any Sweet Home 3D specific code because it is saving it as a OBJ which cannot store these properties.
- Export all Models
- There is no native method to export all or even singular items from the library.
- You can copy the relevant files from
- Default Furniture Library: C:\Program Files\Sweet Home 3D\lib\Furniture.jar
- Imported Furniture (SH3F): C:\Users\username\AppData\Roaming\eTeks\Sweet Home 3D\furniture
- You can export all user imported models using the ExportToSH3F plug-in to a furniture library.
- Export a single object from the library
- This is a workaround
- Open the relevant SH3F (or JAR) file with Furniture Library Editor
- find the model you want to export
- delete all other models
- Save library in a different file
- You now have a library file with just one model in it with all of its properties saved
- Combined 2 models together to make one single OBJ
- Select multiple objects and export as OBJ
- This is easy and works as expected although as normal with a OBJ export Sweet Home 3D parameters are removed
- Select items you want to combined
- Export to an OBJ
- (3D View --> Export to OBJ format)
- Save
- You now have a new single model made from different models.
- Import OBJ and add options as required.
- 'CopyAsNewFurniture
- This strips all SH3F properties and more, I would not recommend uising this method
- Select 2 or more objects
- (Tools --> Copy as new furniture)
- Paste
- This object will not have any of the special tags present such as staircase, Door/Window...
- Export as OBJ
- (3D View --> Export to OBJ format).
- Save
- You now have a new single model made from different models.
- Import OBJ and add options as required.
- Select multiple objects and export as OBJ
- Remove unwanted models from default library to allow for distribution
- Sweet Home 3D Forum - View Thread - Remove default libraries from Sweethome
- Default library is stored in the furniture.jar file found in the lib subfolder of Sweet Home 3D installation folder. You can delete that file if you want, or move it elsewhere.
- You could edit the furniture.jar file with 'Furniture Library Editor' but this would get overwritten with updates.
- located at C:\Program Files\Sweet Home 3D\lib\Furniture.jar
- Sweet Home 3D Forum - View Thread - Remove default libraries from Sweethome
- SH3F Format
- Format Explained
- SH3F is a standard zip file with a different file extension
- In the root is a LICENSE.TXT (might be optional)
- Each language has a properties file in the root and it is this file where the extra information specific to SweetHome3D is stored which can be edited by the Furniture Library Editor such as door/window openings.
- There is a single folder that seems to be the same name as the zip fileneame (excluding extension). You might find these 2 dont have to match but the do.
- In side this single folder you will find more folders and each of these folders relates to a model.
- Within each model folder you will find the following
- MTL
- OBJ
- Textures
- So as you can see SweetHome3D is:
- OBJ and MTL files with a properties overlay
- has the convenience of including the textures
- includes the model icon for displaying a preview in the software
- category
- the model name, creator and of course this is all translatable.
- Can hold a single or multiple models (there is no separate format for single models)
- Example layout
/contributions/ /contributions/1DoorLowerCabinet/ /contributions/1DoorLowerCabinet/1DoorLowerCabinet1.jpg /contributions/1DoorLowerCabinet/1DoorLowerCabinet2.jpg /contributions/1DoorLowerCabinet/1DoorLowerCabinet3.jpg /contributions/1DoorLowerCabinet/1DoorLowerCabinet.mtl /contributions/1DoorLowerCabinet/1DoorLowerCabinet.obj /contributions/ButterflyFrame/ /contributions/ButterflyFrame/Butterfly.jpg /contributions/ButterflyFrame/ButterflyFrame.mtl /contributions/ButterflyFrame/ButterflyFrame.obj LICENSE.TXT PluginFurnitureCatalog.properties PluginFurnitureCatalog_fr.properties
- Sweet Home 3D Forum - View Thread - 3D models specifications?
- A detailed forum thread on on converting objects and references for the SH3F specification
- As for the SH3D specifics you may want to have a look at the FurnitureLibraryEditor (see download page) which will allow you to supply additional model information
- For instance: .obj (and other import) files do not support some more advanced features like window/door cut-out, but this can be added with the FurnitureLibraryEditor. If you need light sources in the model and other advanced properties, you may just need to dive a little deeper into the file specifications (see Sourceforge docs)
- SVG is used for customised cut-outs in walls (windows/doors) and ceilings/floors (staircases).
- Format Explained
- Create your own SH3F
- Sweet Home 3D Forum - View Thread - Create own SH3F file (Puybaret)
- From version 1.5, you can create a SH3F file containing the furniture imported in Sweet Home 3D catalog with the plug-in ExportToSH3F
Once you downloaded this plug-in, copy it in the plug-ins folder of Sweet Home 3D, which depends on your system as follows: - under Windows 7, this folder is C:\Documents and Settings\username\Application Data\eTeks\Sweet Home 3D\plugins
- under Windows 10, this folder is C:\Users\username\Application Data\eTeks\Sweet Home 3D\plugins
- under Mac OS X, it's the subfolder Library/Application Support/eTeks/Sweet Home 3D/plugins of your user folder
- under Linux and other Unix, it's the subfolder .eteks/sweethome3d/plugins of your user folder.
- Relaunch Sweet Home 3D, and you'll see the new menu item "Export imported furniture to SH3F..." in Furniture menu. At this time this will work, only if you installed Sweet Home 3D 1.5 with its installers. If you installed it with Java Web Start, it may not work for security reasons and you'll have to download the installer.
- About your second question, if you want to add some furniture to the program, the easiest way is to generate a SH3F file with the aforementioned plug-in, rename its PluginFurnitureCatalog.properties entry as com/eteks/sweethome3d/io/AdditionalFurnitureCatalog.properties, and add the modified SH3F file to the classpath of Sweet Home 3D.
- !!!Caution!!! Take care of the license of the models you export to a SH3F file. Almost all free models can't be redistributed, and the fact that Sweet Home 3D is free doesn't change anything to that. That's the reason why I had to create some models for the first versions of Sweet Home 3D!
- From version 1.5, you can create a SH3F file containing the furniture imported in Sweet Home 3D catalog with the plug-in ExportToSH3F
- Sweet Home 3D Forum - View Thread - Create own SH3F file (Puybaret)
- Make your own Furniture/Objects/Models
- This is for the programmers or the more enthusiastic person and is a good reference for me.
- For complex model designs you will need to use an external 3D design software such as
- MS 3D Builder (apparently this is different to MS 3D Paint)
- Sweet home 3D - Create basic models with SH3D | YouTube | RedTop Learning
- Create basic models using Sweet home 3D.
- Watch this if you want to make 3D models with Sweet Home 3D
- If you make an object transparent using a texture such as HalfTransparentGrey.png and then export and re-import it as another object, then that object will be permanently transparent.
- Combine several objects into a single model in Sweet Home 3D by using CopyAsNewFurniturePlugin, and then export it or save to library as required.
- The Furniture Library Editor apparently has the ability to add a door/window arch but I cannot figure this out.
- Make objects transparent
- Sweet Home 3D Forum - View Thread - d value in .mtl can be edited in sh3d
- If you want to make a color transparent, you can replace its material by a half transparent texture in Materials modification dialog box.
- Import as a texture the HalfTransparentGrey.png attached to this post and use it in the Material dialog box to replace the material you want transparent.
- Sweet Home 3D Forum - View Thread - How to import model of a cabinet with transparent glass panel?
- Sweet Home 3D Forum - View Thread - d value in .mtl can be edited in sh3d
- Draw a Glass Wall
- Sweet Home 3D Forum - View Thread - glass wall
- You can't draw glass walls in SH3D.
- The workaround is a as follows:
- Insert a door frame or a service hatch in your wall and give it the correct dimensions
- Download one of the glass boxes in the Attachments section
- Import the glass box
- Resize and insert the glass box in your door frame or service hatch.
- Sweet home 3D - Glass wall | YouTube | RedTop Learning
- How to make a part of the oval shaped wall entirely out of glass using Sweet home 3D.
- Sweet Home 3D Forum - View Thread - glass wall
- How to add a glass panel and glass door for Kitchen?
- Sweet Home 3D Forum - View Thread - How to add a glass panel and glass door for Kitchen?
- Download one of the glass/transparent boxes in the Attachments section
- If you change the dimensions, you can use it as a glass pane for a door or window.
- Sweet Home 3D Forum - View Thread - How to add a glass panel and glass door for Kitchen?
- how to make window with a glass 3d model in sweet home 3d #- 03 | YouTube | up see - how to make window with a glass 3d model in sweet home 3d
- Turn off window opening directions in Plan
- Sweet Home 3D Forum - View Thread - Window opening directions
- There is not an option in the GUI, If you want to turn off this drawing from a plug-in, it's not possible.
- You'll have to modify the furniture library SH3F file where these windows come from, removing the properties starting by doorOrWindowSash from the PluginFurnitureCatalog.properties file found in the SH3F file (see also this thread). For the windows in the default catalog, change the same properties in the DefaultFurnitureCatalog.properties file found in Furniture.jar file. This file can be found in the installation folder of Sweet Home 3D.
- There is a workaround to achieve this: Export the door or window and import it again as door or window. Since it now doesn't come from the furniture library it also doesn't have the extra properties to display the opening. Make sure you give it a recognizable name because it will look the same as the original furniture but without the display of the opening in the 2D view.
- Sweet Home 3D Forum - View Thread - Window opening directions
- I wouldn't use windows. Just create glass walls using boxes and glass.
- Sweet Home 3D Forum - View Thread - Window opening directions - by Keet
- If you are creating your own custom conservatory I wouldn't use windows. Just create glass walls using boxes and glass. Your model will be smaller and without the unneeded opening displays.
- To create glass use a box the size of the glass you need. Export the box and name it "Glass.obj". Edit the Glass.obj and Glass.mtl files like this:
- Edit the Glass.obj file and replace "usemtl bottom", "usemtl top", "usemtl left", "usemtl right", "usemtl back", and "usemtl front" with "usemtl Glass". This should result in having 6 times "usemtl Glass" in the Glass.obj file.
Save the file. - Edit the Glass.mtl file and remove everything under the top comment lines (#), then insert this block of code:
newmtl Glass illum 2 Ka 0.0 0.0 0.0 Kd 0.009412 0.009412 0.009412 Ks 0.039062 0.039062 0.039062 Ns 1.960784 Ni 1.45 d 0.5
- Save the file.
- Import the Glass.obj file and you have a Glass object that you can resize to any format. You can still change the colour of the glass.
- You can use this same glass object for any other furniture you create that needs glass. You now also know how to change a property in existing furniture to glass.
- Sweet Home 3D Forum - View Thread - Window opening directions - by Keet
- Models come with pre-determined measurements
- their defaults can be set or altered in the Furniture Library Editor.
- Open / Close all windows at the same time?
- Sweet Home 3D Forum - View Thread - Open / Close all windows/doors
- Is there an automated way of opening/closing all doors or windows (to a certain literal degree), be it in the interface, or even search/replace some value in the Home.xml that is present in the .sh3d (ZIP) file?
- Just add the element <transformation> you found to each <doorOrWindow> element in the Home.xml file. This will work only for a given model.
- Editing an object
- if you just change colour you will replace all editable colours of all assets of the model.
- Too edit individual parts of the object (if possible) then you need to modify via (Modify furniture --> Color and texture --> Materials --> Modify)
- When you select an individual material in (Modify furniture --> Color and texture --> Materials --> Modify) the relevant part of the model will flash on the preview image.
- You can modify imported OBJ furniture stored in your library by right clicking on them in the library pane and selecting 'Modify furniture'. Native SH3F models cannot be modified like this.
- Rotating an object on the horizontal axis
- Sweet Home 3D Forum - View Thread - Rotation of windows along x, y and z axis
- Doors and windows can't be rotated around an horizontal axis. This is on purpose because Sweet Home 3D is able to make window holes only in vertical walls.
- If you want care about the hole that a window could make in a slopping surface, don't import it as a door or window, or if it's already in your catalog, add it to your home, export it to OBJ format and reimport the exported OBJ file as a furniture without selecting the Door or window option in the Furniture import wizard.
- If you want a hole, please reading the tip How to design a sloping ceiling with a window.
- I have done this to make my conservatory assets
- This article shows you how to change the orientatial of an object by using the import process (sneaky !!!)
- Window movements are maintained.
- You can combine objects together after import.
- Sweet Home 3D Forum - View Thread - Rotation of windows along x, y and z axis
- Can you explain the furniture 'Movable' option?
- When the base plan is locked, only movable furniture can be selected and moved in the plan.
- It's typically used for windows and sanitary.
- Furniture Library Editor
- Sweet Home 3D Forum - View Thread - Furniture Library Editor released - This is the forum thread for the software and has the latest
- This software allows you to add Sweet Home 3D specific code to models/furniture
- When you rename a model it's assets stored in the SH3F are renamed also. See Sweet Home 3D / Feature Requests / #1128 Furniture Library Editor - inconsistent intername file handling
- Copy and Paste
- Hidden assets are not copied unless you select them in the furniture pane
- My Colours I used
- Wood: #91530B
- Gold: #CCBA78
- Sweet Home 3D Default background colour: #A8A8A8
Staircases
Staircases are a special type of model in Sweet Home 3D
- How to customize staircases - Sweet Home 3D Blog - This is a good opportunity to explain how to use staircases in Sweet Home 3D and the new Invisible material option added in the version 5.2.
- Sweet Home 3D Forum - View Thread - Modifying Staircase to Prevent Floor Hole - This has great explanations and solutions.
- Sweet Home 3D Forum - View Thread - Stairway Holes - I was experimenting tonight with making holes between floors to accommodate custom stairways as regular (non-stair) objects.
- Sweet Home 3D Forum - View Thread - How to fix a hole in the floor
- To avoid the automatic cut-out of holes over a staircase:
- Select the staircase,
- Export selection as .obj.
- Import the .obj file without selecting the Staircase option.
- Draw the room on the floor above manually (to create a hole for the stairs).
- BTW: Make sure you leave enough headroom between the steps and the ceiling in the staircase. Not only is this a legal requirement many places, but banging your head in the ceiling above a staircase can hurt, badly. Grew up in an old house made for the vertically challenged. Permanent bump in the head.
- To avoid the automatic cut-out of holes over a staircase:
- Remove an unwated hole caused by stairs
- Sweet Home 3D Forum - View Thread - What happened to the floor?
- The easy way to fix this would be to add a box where you wish to cover the stairs (you have to paste it at the first level).
- The perfectionist way is to edit the staircaseCutOutShape in the home.xml in your sh3d file.
- Sweet Home 3D Forum - View Thread - What happened to the floor?
- Sweet Home 3D Forum - View Thread - Distribute elevation plugin - This is a plugin to make your own stairs from blocks.
- Sweet Home 3D / Feature Requests / #1132 Hide stairs with room properties
- Workarounds / Other solutions
- You can export the stairs model and re-import it not as as a stairs object and then make your holes in the floors manually
- Edit the SH3F model's cut-out in the object
- modify the stairs properties in the home.xml
- create level on the same elevation and add another floor (not tried this one)
- Use the box model and cover the hole.
- Workarounds / Other solutions
- how to make stairs with a glass 3d model in sweet home 3d | YouTube | up see
Doors and Door Frames
There are a few things about how doors and their frames work to get the best out of them.
- Doors
- When you drag a door into a wall, the white area (door cartridge) snaps into place in the wall and the door is sized correctly so the cartridge is exactly the same width as your wall. The door will be ratioed correctly so it looks nice and normal.
- Make sure that the door has snapped into place. sometimes if the door is much thick than the wall then snapping might not work 100%, so what i would do here is pull the door of, reduce it's width and replace it back into the wall. Remember that the white cartridge area should bridge the wall all the way through.
- When placing a door the white square bit is the cartridge (door, door and frame) the extra bits indicated by an area surrounded by a grey line is the potential area door furniture can possibly use.
- Door furniture are things like door handle or letter box.
- It makes a difference in which way you drag the door into the wall. This can be fixed by vertical and horizontal flipping.
- The depth of the door includes the lined areas not just the cartridge.
- Only reduce door depth if you want to recess it.
- To make my recessed external doors I made my door depth the exact same width as the exterior wall and then i moved the whole door including all of the lined area into the wall as well which gives a nice fit and a recessed door effect.
- The arc indicates which way the door will open and seems to always be the same side as the larger lined area.
- There is sometimes a very small lined area on the other side of the door and this will depend on the door you use. Again this is probably to allow for door furniture.
- When measuring for a door, make sure you know if the door object you are adding has a frame, not all doors have a frame.
- Sweet Home 3D Forum - View Thread - Doors "keep proportions" feature
- Q: Once opened in "modify openings" they get "keep proportions" permanently ticked on and that's the end - sizes get updated into something irrelevant and can't be adjusted.
- A: This is because it’s too complicated to compute the adjustment of the 3D model of this kind of objects without deforming it when only one dimension is changed. Just close the door, change its size and reopen it.
- Door and Door frame (combining 2 objects)
- You should choose a door with the door frame (or not) you want rather than trying to select a door and then put a door frame around it, however this is not impossible just a bit fiddly.
- There are no direct interactions between a door and a door frame. They will only appear to be a pair because they are placed next to each other and the objects act like layers.
- Calculate your door frame width and then add your door into the frame unless a precise size of the aperture (i.e. door width) is needed
- There is currently no way to set the aperture of a door frame
- You could work our the size of frame required to give a specific aperture (door width) from the figures of a newly created door placed in a newly created frame.
- Create a door frame
- Drag a door (without a frame) from the catalogue into the door frame
- You can now see how big the door is for a given frame width, record these figures.
- Make the door frame wider and then record these figures
- You should now be able to work out the ratio of aperture size to door width. You might find that there is not a ration but just additional width and height added on for the frame.
- Add a Door swing and arch
- Sweet Home 3D Forum - View Thread - Door swing in plan
- Unless you know how to program OBJ files, there's no way to add the doorswing to an imported door. However, there's an easy workaround.
- Insert a hatch into your wall, then insert the door into the opening of the hatch. Rotate it 45 degrees or so, and you have a custom open door.
- There's no way to specify a door swing in OBJ format. The OBJ format isn't that clever!
- If you want to achieve that with your own model, you should create a custom SH3F file containing your door model (use Furniture Library Editor if you want to), and add the following properties in the PluginFurnitureCatalog.properties file contained in the SH3F zipped file (where n is the number of the model).
- This has all of the relevant code for you to look at, if you want to make your own door, read this thread.
- Unless you know how to program OBJ files, there's no way to add the doorswing to an imported door. However, there's an easy workaround.
- This would be similar for adding a swing to a window.
- Sweet Home 3D Forum - View Thread - Door swing in plan
Conservatory
There is no native support for conservatories in Sweet Home 3D but there are workarounds such as the one below which allowed me to draw my full height PVC Double glazing conservatory.
I have made a conservatory.sh3f library with a few useful assets in, i will release it when i sort the licensing out
Create the conservatory room with a wall
- Draw your conservatory's floor plan out as you would any other room (pick your method)
- Use the measurements of your double glazing cassettes (Window height, Trim height, thickness) to make the wall.
- or use possibly a wall that is 0.1mm high. I think using the full wall height will allow the roof to work better and keep the measurements correct.
- You can always use these examples measurements that i have used for my UK 28mm cartridge double glazing conservatory.
- Window Height: 210cm
- Trim Height: 15cm
- Height: 225cm
- Thickness: 7cm
- Use the measurements of your double glazing cassettes (Window height, Trim height, thickness) to make the wall.
Create your glass pane
- Method 1 - Export Window/Door model as an OBJ
- This gives me the object as a standalone model but with the door/window arches stripped.
- Windows and doors are still articulated and can be moved.
- We need to create a glass pane without any opening window (optional - there might be conservatory assets available, but this is a quick workaround)
- Drag a windows/door eg `Window (91cm x 34cm x 174cm by eTeks)' onto your conservatory wall you made earlier
- Make the handle and any joints invisible by modifying the objects properties.
- Export this as an OBJ (3D view --> Export to OBJ format)
- Once you have exported the object, imported it using the wizard (Furniture --> Import furniture)
- Tick the box 'Door or window'
- Give it a decent description such as 'Conservatory - Glass Pane'
- Put in the exterior category
- You now have a glass pane with no window arc
- The window can still be rotated via it's properties.
- Drag a windows/door eg `Window (91cm x 34cm x 174cm by eTeks)' onto your conservatory wall you made earlier
- Method 2 - Export Window/Door model as a SH3F
- Design objects as required in Sweet home 3D
- use `Furniture Library Editor` to export default objects in sh3f format from furniture.jar
- Currently you can only export the whole library, so I will make a copy of furniture.jar and delete every model except the one I want top export and then save it as a different file
- This gives me the model with all of the SH3D properties such as door arches intact.
- The objects are not in their own folder so a little tidying might be required. file locations are in PluginFurnitureCatalog.properties
- Look in contributions.sh3f for a good layout
- Repeat this process for each model you want to export.
- create a new SH3F called conservatory.sh3f
- Import all of the models you just exported as sh3f
- You need to use the 'merge' feature, NOT import.
- Using `Furniture Library Editor`
- Alter the models default settings to match those in your design
- In Sweet Home 3D I built a wall that was the same as my real conservatory measurements (225cm(h) x 7cm(thickness)) and then dragged my newly imported models on to them.
- I then made a note the updated thickness value of the assets which were caused by magnetism snapping the model to the wall.
- I updated my conservatory.sh3f library with these new thickness, saved it and then re-imported.
- You do not need to do this step but I did so all assets matched my walls and did not need to be modified.
- Make sure all of the doors and windows are the same way in the preview.
- The Front View should always be what you see from the inside.
- Alter the models default settings to match those in your design
- Manually edit conservatory.sh3f and go through the following
- The SH3F is a zip file with a different file extension so pick one of the following:
- Open the file as is in WinRAR
- Change the file extension, unzip, edit hte files, then re-zip and then finally change the file extension back to SH3f
- Update language files in conservatory.sh3f
- If you make changes to the names and descriptions, these will need changing in the SH3F file or you can just delete the extra language files.
- Add the following files into the root of your conservatory.sh3f file
- README.TXT - Add any notes you need to here suach as where you downloaded the textures from.
- CHANGELOG.TXT - This is useful to keep users upto date and know what version they have.
- LICENSE.TXT - Fill in with the relevant license if you are distributing
- Edit the colours in the SH3F as required, such as adding glass effect (optional)
- The SH3F is a zip file with a different file extension so pick one of the following:
Assembling the conservatory glass panels
Now you have the assets you have just made, it is time to use them.
- Now go around your conservatory wall and populate it with the a combination of the following assets:
- 'Conservatory - Glass Pane' (from above, by eTeks) - use this to create large glass panes
- 'French window' (91cm x 34cm x 210cm by eTeks) - this can be used for single doors or windows
- 'Double French window' (132 x 34 x 210 by eTeks) - use this for double doors
- NB:
- Set all assets to have 0 elevation and all be the same height and width where required.
- Make sure magnetism is on
- Your 'wall' might have different proportions which is fine.
- Adding Roof, to follow.
Notes
- Conservatory model examples
- Sweet Home 3D Forum - View Thread - Lean-to conservatory - Thius was done with only Sweet Home 3D assets.
- Four Seasons Conservatory | 3D Warehouse - Conservatory 15' x 14', large one with a dude by Patrick F. Windows were not transparent when I imported it.
- Four Seasons Conservatory | 3D Warehouse - 15 x 11 Four Seasons Sunroom, shorter version by Patrick F. Windows were not transparent when I imported it.
- Conservatory In Bethesda, MD | 3D Warehouse - Large glass conservatory by Adam Patrick Ford - This imports the whole house, but the conservatory glass is transparent.
- Make the walls transparent
- You can make your conservatory walls and instead of installing models you can just make the walls transparent giving a sort of glass effect. (see wall section for instructions)
Roof
- Sweet Home 3D Roof Tutorial | YouTube | SBCODE - How to make a roof in Sweet Home 3D.
- Sweet Home 3d Velux Roof Window Tutorial | YouTube | SBCODE - How to create a simple Velux style roof window and then a more advanced version but with the window open.
- Sweet Home 3D : FAQ - How can I create a roof on top of a house?
- Sweet Home 3D supports the creation of ceilings seen from below, but doesn't propose some simple way to create roofs yet. Nevertheless, you can use various tricks to cover a house: if the roof is flat, you can draw rooms in a level matching that roof.
- If you want to add a sloping roof, you may assemble blue slate roof, red slate roof or polygonal roof 3D models available at the 3D models import page, as well as the ones available in 3D Models Contributions Tracking System like Krams036's models and OK Hoff's models.
- From the version 5.5, you may also assemble boxes and triangles of the Miscellaneous category that you'll flatten and rotate around their horizontal axis, like in the house demos available in the dialog box shown by the File > New from demo menu item.
- Finally, the Roof Generator plug-in developed by Dorin Vatavu with the help of Daniele Lombardi is useful to create roofs with various slope angles.
Wiring and Pipes
The wiring plugin notes will go here.
- How to quickly draw water pipes in Sweet Home 3D | YouTube | SBCODE
- This method might be redundant now because of the wiring plugin
- I quickly demonstrate how to draw water pipes in Sweet Home 3D. It is a manual process where I resize and colour a standard cube object.
- It can be useful to visualise the plumbing of your house when planning any your work that may need doing.
- This video shows my heating water pipes, hot cold pipes and radiator placement, and is a work in progress.
Textures
- Supported formats
- SH3T - Native 3D texture library
- External formats supported - BMP, JPEG, GIF, PNG
- Sweet Home 3D : Textures import
- Download and import texture images for Sweet Home 3D official download page
- Also a variety of external links to other resources.
- Sweet Home 3D Forum - List Attachments - Search the post attachements on the Sweet Home 3D forum for textures.
- Free Textures for blender, sweethome3d and others | Blogscopia
- Copy all textures from one PC to another
- Sweet Home 3D Forum - View Thread - copy the library with the textures that I created on my pc to another computer
- You have to copy the preferences.xml file too.
- Caution! Once preferences.xml is copied on the destination computer you'll will loose all the furniture and textures you imported on that computer. So create a backup of Sweet Home 3D directory first.
- Portable version is covered here as well.
- Sweet Home 3D Forum - View Thread - copy the library with the textures that I created on my pc to another computer
- How to view the textures catalogue
- I don't see texture catalogue in the catalogue panel. Also, if I import a texture, where do I get to see it?
- The catalogue at the top left of a Sweet Home 3D window displays only objects.
- The imported textures appear in the texture modification dialogue box displayed when you want to change the texture of furniture, wall sides, room floor and ceiling and 3D view ground and sky.
- Frosted Glass
- My Method
- Download this texture Wall texture png overlay, abstract | Free PNG - rawpixel (you must attribute)
- Import it to Sweet Home 3D and accept the new resolution of (512px x 341px)
- Give it a size of (30cm x 20cm)
- Modify one of your windows and change the glass to use this texture
- Set the scaling of the texture to be 1000%
- The effect is not bad and with some experimentation and maybe changing the opacity of stuff could look really good.
- Sweet Home 3D Forum - View Thread - Glass blocks
- Getting a frosted glass effect is not really feasible in Sweet Home 3D.
- This thread develops a frosted glass block that you can use. It is an OBJ and not a texture.
- Some frosted glass textures I found
- Glass Texture Images | Free Vector, PNG & PSD Background & Texture Photos - rawpixel
- Glass Texture · High resolution authentic textures & backgrounds. Vector, PNG & PSD formats. Paper, wood, marble, nature, industrial, vintage, grunge and more. Safe for commercial use.
- Some really good options here.
- Frosted glass texture Images | Free Vectors, Stock Photos & PSD - You can find & download the most popular Frosted Glass Texture Vectors on Freepik. There are more than 4,000 Vectors, Stock Photos & PSD files. ✓ Remember that these high-quality images are free for commercial use
- Frosted Glass Texture Png - Kitchen Cabinet Transparent PNG - 520x650 - Free Download on NicePNG - Download Frosted Glass Texture Png - Kitchen Cabinet for free. NicePNG provides large related hd transparent png images.
- Sweet Home 3D Forum - Attachment Search Form - Search for frosted glass
- Cotswold - Pilkington Glass - This image will be copyrighted and is here for my reference
- Glass Texture Images | Free Vector, PNG & PSD Background & Texture Photos - rawpixel
- My Method
Tutorials
Tutorials, tutorial series or ones that don't fit elsewhere.
- Sweet Home 3D : User's guide - Learn how to use Sweet Home 3D quickly and efficiently from this official easy to follow guide.
- Best video tutorials about Sweet Home 3D - Sweet Home 3D Blog - There are hundreds of Sweet Home 3D tutorials on YouTube! Short or long, mute or spoken in many different languages, good or less attractive, oldies or recent videos, unique ones or parts of a serial, popular or unknown...
After viewing most of them, I made the drastic selection below. - Get started with Sweet Home 3D on Linux - This tutorial will guide you through the first steps in designing with Sweet Home 3D.
- How To Import Autocad File In Sweet Home 3d?
- How to import Autocad/FreeCAD file into Sweet Home 3D
- And load of other stuff and tutorials
- SH3D Lesson 6 - Basement & Second Floor Levels | YouTube | TJ FREE - How to create a second floor.
- SH3D Lesson 12 - Create Custom Textures and Paint Colors | YouTube | TJ FREE
- How to Draw a Floorplan and get a 3D picture with SweetHome3D | YouTube | DrZzs
- Tutorial Series
- Sweet Home 3D YouTube Channel - Official tutorials here.
- Sweet Home 3D : Tips - Lots of official videos here.
- Sweet Home 3D Tutorials | YouTube | TJ FREE - Learn SweetHome3D in this free tutorial series. Sweet Home 3D is a great, free, professional 2D and 3D floor plan drawing software. You can download it for free on Window, Linux, and Mac.
- Sweet Home 3D | YouTube | SBCODE - All Sweet Home 3D Tutorials by SeanWasEre
- Sweet Home 3D | YouTube | RedTop Learning - More technical videos
- Move the whole project on the plan
- Sweet Home 3D Forum - View Thread - Moving entire plan within grid
- Chose Select all or Select all at all levels in Edit menu, then drag and drop your design.
- Select All at All Levels doesn't seem to be working, lots of items are still not selected on the list on the left. Other options? It’s probably because you locked the base plan. Unlock it first.
- Sweet Home 3D Forum - View Thread - Moving entire plan within grid
- Magnetism
- This helps you draw rooms with 90 angles and sticks assets to the grid lines. 15 degree angles are allowed.
- It helps placement of doors and assets by making them snap in place and resize as needed to correctly fit into a wall.
- How to control magnetism | YouTube - Many actions are helped by magnetism, in Sweet Home 3D. This tutorial shows its advantages and when to disable it.
- Creating a video walkthrough in SweetHome3D | YouTube | Loreto College Coorparoo
Resizing Assets
Once you have created an asset (objectys, lines, rooms etc...) in Sweet Home 3D you can only modify the object in the following ways:
- Use the mouse on the 2D plan
- Select the object and manipulate as required
- Edit Points (AdvancedEditing plugin required)
- Select the object you want to resize
- Goto (Plan --> Edit points)
- Alter as required
- Resize (AdvancedEditing plugin required)
- Select the object you want to resize
- Goto (Edit --> Edit Resize)
- Alter as required
- Object that do not have 4 sides will be wrapped in a square, which is then modified.
Notes
- This process can sometimes alter other assets on your paln if you are not careful.
- Sweet Home 3D Forum - View Thread - Modifying dimensions once after they have been added
- You can modify dimensions only with the mouse.
- If you want to enter a precise value, type <Enter> when you initially draw it. See included help for more information.
- Or Install AdvancedEditing plugin from the Sweet Home 3D : Plug-ins and tools
My Wall Mounted Network Cabinet
There are 2 ways to mount this cabinet to a wall and then the fixing method depends on the type of substrate you are attaching too (BRick/Concrete/Drywall/Plasterboard)
Both methods require the use of some sort of Anchor Bolt........ get proper name
In the box 4 are included but it is unclear which method they are suitable for.
Method 1 - Mounting plate
Pros
- Easier to mount because you place and attach the mounting plate without the bulk of the cabinet
- Allows easy removal of the cabinet by just undoing to non-load bearing screws.
Cons
- I feel that over time if the cabinet is heavy, that this will eventually pull the mountings out or damage the drywall because the cabinet will always be pulling on an angle rather than straight down.
Method 2 - Large Bolt Holes
Pros
- Will hold heavy weight without fear of the bolts coming out over time for the Drywall failing
- Because you are using 4 holes the weight is more evenly spread and there is a modicum of cantilever effect happening, to a different extent depending on the substrate being attached too.
- The holes might be set at an industry spacing so could allow for easy replacement of the cabinet.
Cons
- Harder to install
My Citizen CLP-521 Thermal Printer Notes
These are a collection of notes to help me use my Citizen CLP-521 Thermal Printer
The first label printed after power on is always corrupt
This issue has been plaguing me for a while and is shown in the image below:

Whenever I turn the printer on, the first label I print is always corrupt and has cost me a fair few labels.
Cause
- Using Windows 10 and the USB connection on the printer
- It most likely is a speed issue of the USB driver.
- This printer might only like USB 1.1
- The reason the first label gets corrupted, is the data is sent to quick over USB 2.0, but the subsequent communications over USB are clocked down to USB 1.1
- It could be an issue with the Seagull driver itself, but this is a legacy printer so this issue is unlikely to get fixed in the driver.
Notes
- You could try a better USB cable
Solution
- Make sure your Windows OS is up to date.
- Download and install the latest drivers for your printer (completely uninstalling might be better)
- Optionally, factory reset your printer and recalibrate you label sensor
- Factory reset did not seem to make any difference for me, but will definitely get rid of bad settings.
- Connect you printer via one of the following methods
- Parallel Port network print server such as the HP JetDirect Ex Plus (J2591A) Print Server. Configuration instructions can be found here and I have used this particular print server with the CLP-521 so I know it works.
- A real Parallel port
- COM port - I have not tested this, but I would guess it will be very slow.
Bartender prints first label blank after power down on Citizen CLP521
These solutions have only be tested using standard labels with the transparency sensor
Solution 1 - Correctly position the label before the sensor
Before powering on the printer, load the labels as shown below. You are going to position the head of the first label just before the paper sensor, but not over the sensor. This allows the printer to find the front of the first label. If you have too much space on the roll before the first label, this method will not work and the first label will probably be discarded. If the label is actually over the sensor, this will cause the first label to be discarded.


Solution 2 - Run a dummy single label through first
This was my first solution I figured out but might have relevance for further fixes.
Keep a single label on its backing paper. This backing paper should be long enough to be loaded into the printer with the label being towards the end of the paper and can be positioned before the paper sensor.
- Load the single label into the printer before the sensor.
- Hit the feed button
- The label should be loaded into the correct position.
- Print your label and one of 2 things will now happen:
- The label will print
- A blank label will print
- The label was expelled out the front and the feed continued until the backing paper was out as-well
- A beep and print error was showing indicating paper out
- Put your single label paper to one side. You might need to use this in the future as printer power downs.
- Load your main roll of labels so the first label is behind the label sensor
- Press STOP to cancel beeping
- Press FEED to load the label or just hit print
- The will feed the label correctly and your labels will now print as normal.
Notes
- Bartender prints first label blank after power down on Citizen CLP521 – BarTender Support Portal
- Hello, on Citizen CLP521 Bartender prints first label blank after power down. As I understand the printer checks where the start of the label is, but can't this be turned off if I never remove / change paper ?
- I believe that will be the printer itself trying to find the correct start of print position. Not sure on the Citizen but on some devices you can disable this via a front panel option but then this can cause the first label to be printed incorrectly as it starts part way through the label and only looks for the gap/mark after it has printed the first label.
- I would suggest when you power up or reload the paper that you feed a label first to make sure the device is in the correct position to start printing.
- Dirty paper sensor - This might causes issues
- Do i need set on the printer the label size? Can this be causing an issue?
Reset Printer to factory defaults
When following these steps, messages will be printed so make sure you have paper in the printer.
- When turning the printer on press and hold the MODE/REPEAT button.
- Press PAUSE
- Press and hold the FEED button for 3 secs.
- Press STOP
- Press STOP
- Press STOP
This is an image of the printed messages you should expect:

You will now need to calibrate your label sensor.
Sensor Adjustment
This process allows you to swap between the reflective and transparency sensors. This process is covered in the manual (Page 34) for both types of mode but we will configure for standard sticky labels (i.e. transparency mode)
- Enter sensor adjustment mode 3 buttons
- Turn on the power while pushing the PAUSE key, FEED key and STOP key simultaneously.
- Set the sensor mode (Transparent <--> Reflective)
- For this we will enable the transparent sensor
- Transparent sensor is the default
- See page 34
- To switch from transparent to reflective sensor, ensure the CONDITION LED is lit then hold down the MODE/REPEAT key and then press the STOP key.
- Each time you press the STOP key, you switch back and forth between the two sensor types.
- If the transparent sensor is selected, the PRINT LED lights up and the buzzer sounds once. If the reflective sensor is selected, the PRINT LED flashes slowly and the buzzer sounds twice.
- Make sure top and bottom sensors align
- Install the label paper roll but with the with the labels removed at the beginning so the print sensor can see through the paper. It cannot see through labels.
- Hold down MODE/REPEAT and press PAUSE and release
- If successful, the PRINT LED and CONDITION LED return to their original status.
- Press STOP to exit out of this sensor adjustment mode.
LabelPrinterUtility
If I could get this utility to work with the CLP-521 then I could configure everything from a proper Windows computer instead of using printouts and wasting a lot of paper.
- This use to be called BarcodePrinterUtility.
- Also the last version of this named utility (barcodeprinterutility1202.exe) worked just the same, so this older version made no difference to compatibility.
- Use the Printer Model: CL-S5xx
- This does not fully work with my printer in Windows 10. It might work better in Windows 7.
- Only the Receive 'INFORMATION' option seems to work
- This is good for setting up the label sensor, has pictures as-well
Label Settings
These are some examples of the wheel settings for some label types
- Small White
- Thickness (Vertical Wheel): 1
- Width (Horizontal Wheel): 5
- Settings in Seagull Driver
- Name: Small Labels
- Type: Die-Cut Labels
- Label Size: Width:73.0mm, Height:51.0mm
- Exposed Liner Widths: Left:2.0mm, Right:2.0mm
- This label Manufacturer said they were 76mmx50mm Direct Thermal Labels and the same size as Datamax 420069. (2" x 3")
- This label is almost the same as the Datamax 420069, but the label is a bit smaller on the width. The label backing is 3" across.
- The Datamax Labels has been renamed to the Datamax-O'Neil Labels.
- This actual label is 2" x 2.87"
- 6x4
- Thickness (Vertical Wheel): 1
- Width (Horizontal Wheel): 9
- Media thickness from the manual (page 42)
Media Thickness Dial Position Suggested media type 0 Direct thermal media (thin media) 1 Standard Label media, Direct thermal media 3-5 Thicker backing paper labels 6-9 Cards, tags, thicker media stock. * These values are guidelines. The exact media being used must be matched with the correct media thickness adjustment position. - When shipped from the factory, it is set at dial 1. - The offset adjustment varies according to the thickness and the hardness of the media.
NB: The closes the head is to the labels the more wear is likely and the life of the head is reduced.
Misc
- Downloads
- Downloads for the Citizen CLP-521 | CITIZEN SYSTEMS JAPAN CO.,LTD. - Here, you can download Official User's Manuals, Drivers, Utilities, SDKs and more. The driver here is an old Seagull one.
- Citizen CLP-521 Printer Drivers by Seagull Scientific
- Citizen CLP-521 Windows printer drivers by Seagull Scientific make it easy to print labels, cards and more from any Windows program, including our BarTender software.
- These will always be the latest drivers
- Download Utility | CITIZEN SYSTEMS JAPAN CO.,LTD. - Download LabelPrinterUtility and other utilities here. I have used a cached version so the downloads will appear.
- barcodeprinterutility1202.exe File Download & Fix For All Windows OS | pconlife.com - This is an old version of LabelPrinterUtility and is here for reference only.
- Citizen CLP-521 : Printer User Manual | Manual Shelf - Find and download user guides and product manuals
- Citizen CL-S521 User Manual | ManualsLib - Alternative download location for the manual.
- Settings
- Setting the following will make graphics better (Printing Preferences --> Graphics --> Dithering: Ordered)
- Replacement Guide
- CLP-521 --> CLS-521
- CL-S521 | Citizen Systems - The successor of the CLP-521
- Errors
- How To Diagnose Configuration Issues with Citizen label printers | citizensystems | YouTube
- Producing a diagnostic self-test from and configuration print from our label printers including CL-S521, 621, CL-S700, CL-E720, CL-S6621 and CL-S400.
- how to do a self test print.
- When trying to print, the CONDITION and ERROR lights keep coming on.
- When trying to print and condiition and error lights keep coming on | fixya
- When trying to print, CONDITION and ERROR lights keep coming on. also when pressing feed it feeds through more than one label and then shows the condition and error lights.
- Most common cause for this is sensors not positioned correctly. Make sure that the white arrow on the top sensor is aligned with the bottom sensor. See you user manual.
- Also check that the sensor used is the correct one for the media (i.e. black mark or transmissive).
- How To Diagnose Configuration Issues with Citizen label printers | citizensystems | YouTube
- Maintenance and usage
- How to change the media sensor for a Citizen CLP521 | BOXwise | YouTube - How do I adjust the Threshold Setting? By following the simple procedure outlined in this video.
- cls521 labels | Doug Morton | YouTube - Citizen cl-s521 label loading and sensor placement.
- Media Width and Thickness Adjustment for Citizen CL-S521/621 and CL-E720 Label Printers | citizensystems | YouTube
- Using the media adjustment dials or ‘wheels’ to set correct media width and media thickness on the CL-S521, CL-S621, CL-S631, CL-E720 and CL-E730 models as well as earlier CLP ranges
- Blue Wheels
- CL-S521-CBI printer Instructions | Alicia O'Neill | YouTube - Citizen CL-S521-CBI thermal printer - How to load label and armband media.
- Media Width and Thickness Adjustment for Citizen CL-S521/621 and CL-E720 Label Printers | citizensystems | YouTube - Using the media adjustment dials or ‘wheels’ to set correct media width and media thickness on the CL-S521, CL-S621, CL-S631, CL-E720 and CL-E730 models as well as earlier CLP ranges
- Most Common Thermal Printer Faults and How to Resolve Them | Latest News - Thermal printers are a popular choice for businesses who want to create high quality, durable labels while saving valuable time and money.
- When feeding labels, you must remember the label that is hanging out might have already past the print point so it is the label behind it will be the first to be printed on. Obviously this depends on label length.
this is not true
- PRN files
- These files are just copies of the information sent to the printer, not error logs.
- What's a PRN file, why do I need it and how do a make one? - NeuraLabel Blog - A PRN file is simply a printer file that is created for a specific printer in a language that the printer understands. Therefore PRN files are printer model specific and will not work with other types of printers.
Call waiting is not working on my Android phone
Have you had the following error when you try to swap calls or put a call on hold. This article will bring together all of the causes and solutions.
Error message Can't switch calls.
Background
Before we get started I need to explain a few things
This is a message I got from my provider which helped me understand things:
4G calling uses your 4G data connection to carry your phone and video calls, rather than the 2G or 3G networks.
It also works alongside WiFi calling, so you'll automatically switch between them without your connection dropping.
If your device supports 4G calling, you've already got access to it, but you may need to switch it on your phone's settings, or you can check in our device guides - choose your device, then tap Specifications and scroll down to Communication > VoLTE – 4G calling. It will state here if your device is compatible or not.
The following points are important:
- 2G/3G use a different technology than 4G/LTE for handling voices calls and therefore also Call Waiting is handled by the corresponding technology/protocol.
- Networks can enable/disable Call Waiting for both of these technologies independently
Prerequsites
- Update all of your apps. This probably wont make any difference but it wont harm.
Causes
- Call Waiting is not enabled on your contract
- Call Waiting is not enabled on your phone
- Call forwarding is redirecting all calls before you get them
- Carrier does not support Call waiting on their 2G/3G networks, only 4G/LTE and upwards.
- Phone/ROM not support VoLTE
- Why is this specifically and issue. Most phones support Call waiting on 2G/3G networks but these networks are now being shutdown, but your phone is still working you ask! Carriers will start by shutting down all non-essentials services such as Call waiting on these old networks and hope that customers migrate naturally to newer phones that support 4G/LTE and of course VoLTE. so while the 2G/3G networks are still working these extra features are not. If you do not have VoLTE you cannot utilise Call waiting on the newer network.
- When the 2G/3G networks are shutdown, if your phone does not support VoLTE then you will not be able to makes voice calls.
- Modem is too old
- Technology that handles calls changes, but this technology is not supported in older modems
- Modern phones and carriers require VoLTE
- The Custom ROM such as LineageOS, does not always support VoLTE
- LineageOS that Support Volte? - F-Droid Forum - Is there any way to tell if a LineageOS phone supports Volte?
- Notably anything older than 2016, does not support VoLTE, devices then used non-standard IMS stacks.
- You can check the sources to see if it supports it, but even then your carrier may not allow it or it may lack the required configs for your carrier.
- What exactly should I be looking for when I look at the source code?
Check for an ims.apk in the proprietary.txt files for your device. And because some devices use a common device tree, find the command device tree name in the lineage.dependencies file and check the proprietary.txt files in that repo too.
- Another way to see if you phone can use VoLTE is when you make a voice call, 4G/LTE changes to 2G/3G/H/H+
- This is caused by the phone have to downgrade the connection type to allow a voice call to be made
- VoLTE Questions And Where To Go From Here? : LineageOS
- Users With VoLTE Working : LineageOS
- Determining VoLTE support on a device : LineageOS
- Due to the closure of 2G and 3G networks drawing closer all over the world - the latest date I'm aware of is mid-late 2022, and there are networks that will shut down earlier - devices must support VoLTE to connect to the network.
- In order for VoLTE to work properly, carrier configuration and APN must be correc
- For example stock Samsung OS supports it but LineageOS for S5 klte + variants does not support VoLTE (Voice over LTE).
- You should be able to use the dialer code *#*#4636#*#* --> "Phone Information" to determine if VoLTE is working.
- Dialler storage and cache is corrupt
- Dialler does not have all required permissions
- Carrier configuration and APN are incorrect
- Because VoLTE uses data, it is important for this to be working.
Solutions
These solutions might not work and might not all be relevant to your phone.
- Enable Call Waiting on your contract
- Ring your provider and make sure this feature is enabled and available.
- Enable Call Waiting on your phone
- or *#43# to check (add these notes
- LineageOS 18.1: Dialler --> 3 Dots --> Settings --> Calls --> GSM call settings --> Additional settings --> Call waiting
- Disable Call forwarding
- So you can rules this out. It can be put back on later.
- LineageOS 18.1: Dialler --> 3 Dots --> Settings --> Calls --> GSM call settings --> Call forwarding
- Update Phone Modem (to give VoLTE support)
- Stock ROM: Updating your stock ROM will also update the modem
- LineageOS: You will need to update the modem manually by the relevant method (not covered here)
- Clear the Dialler storage and cache stores
- I have seen people mention this one, but I suspect this only fixes the issue if it was working one day and then not the nexxt rather than after a phone or network update
- Done through the 'App Manager'
- Open the Dialler App properties and make sure it has all permissions enabled
- Re-setup your APN
- Use WiFi calling
- I have not tried this, but if you can install the app, just try and see.
- Get a new modern phone
- This is a last case scenario
Other Notes
- The Android Dialler uses an API to communicate with the modem so it is unlikely to be the dialler causing any issue.
- What is VoLTE? - VoLTE stands for voice over LTE and it’s more or less exactly what it says on the tin. It's voice calls over a 4G LTE network, rather than the 2G or 3G connections.
- Call waiting commands (from Vodafone)
- To activate - enter *43# followed by SEND
- To accept the incoming call and end the original call - press 1 then SEND
- To hold the original call and accept the incoming call - press 2 then SEND
- To swap between calls - press 2 then SEND
- To end present call and return to holding call - press 1 then SEND
- To cancel - enter #43# then SEND
- Phone Information - *#*#4636#*#* then SEND
- Vodafone 845 - Turn call waiting on or off | Vodafone UK - When call waiting is turned on, you can hear and answer a new incoming call while you're on the phone. Follow these instructions to turn call waiting on or off.
- How To Fix Error Message Can't Switch Calls Problem Solved in Android - In this blog, I am going to tell you How To Fix Error Message Can't Switch Calls Problem Solved in Android.
- How to Set Up Call Waiting on Android: 3 Methods | JoyOfAndroid
eBay Android app will no longer install or upgrade on Lineageos
I am using the eBay app as an example here because it is an issue for my, but these instructions and notes should apply to most apps.
The eBay app will not longer update or when you search for it in Google Play on your phone it is not found in the search results
The Errors
You are going to see one of these when trying top install the eBay app when your device is no longer supported
On Google Play via your PC's browser
This app is not available for your device

Via the play store on your phone
This is not possible because Google actively hides the app from you here.
Via the browser on your phone
This work around requires us to search for the `eBay android app`on the Google search engine
Click on the install button and you will now see the following error message;
Your device isn't compatible with this
The Cause
eBay has flagged your device by:
- Device name / Model Number (i.e. SN-9005)
- Android version
- Both
This is why most apps still works but these bigger apps actively remove older device and OS from the compatibility lists.
Have a read of this articl as-well
- Why Can't I Download Certain Apps on the Google Play Store? - Seeing "this app is not available for your device" on Google Play? Learn why some apps aren't available to install from the Google Play Store.
The Solutions
- Upgrade Android OS
- Update your Android version to the latest. It must be a modern version that supports eBay.
- Patch releases are very unlikely to fix this issue.
- Make sure you have GAPPS installed and it is the latest
- A lot of apps depend on services this package installs.
- PICO/NANO/FULL I am not sure if this version makes a difference.
- Clean Caches
- Wipe Data + cache for Google Play
- Wipe Data + cache for Google Services
- This did not work for me
- FIX: “Your Device Isn’t Compatible with This Version” on Android - While downloading specific apps on your Android device, you might find that the Play Store displays a “Your device isn't compatible with this version” error, implying that your device isn’t compatible with the app.
- Change the phones model number - There are a couple of different methods to achieve this:
- Change Model number in the firmware before flashing
- This will cause issues with signatures unless you are the one signing it
- Change the model number on a live phone via ADB and Fastboot
- On a firmware upgrade these settings will be lost
- How to Change Android Device Model Number and Name - DroidViews - If you own a rooted Android device and want it to display a different model number than it really is, you can change it.
- Use Magisk to change the model number
- Magisk Official Sites
- [MODULE] MagiskHide Props Config - SafetyNet, prop edits, and more - v6.1.2 | XDA Forums - Official thread
- MagiskHide Props Config - Magisk - This module is a very complicated way of doing something very simple. Complicated for me, that is... The aim is to make it easy for you, the user. The module changes prop values using the Magisk resetprop tool, something that is very easy to do with a Magisk boot script and some simple commands.
- Magisk and MagiskHide Installation and Troubleshooting guide - I think this is the developers site
- Common
- The options set here should be kept after an in-place upgrade
- The options are loaded at boot and make no physical changes to the firmware
- Edit device fingerprint method (option 1)
- Select another phone that is not blocked by eBay from a list supplied by Magisk in the wizard and then apply it. This fools eBay and Google Play into think you have a different phone.
- This does not make any changes to your phone, it does all of this in RAM via a boot-time script.
- This method has a wizard and is very easy to do.
- [SOLVED]Android 10 build.prop how to change model?? | XDA Forums - [SOLUTION] Solution Find and select the fingerprint of the model you changed in Magisk Hide Props Config (option 1) and restart it.
- Add and submit your own fingerprints to Magisk
- Add/edit custom props (option 5)
- I have not tried this method
- You can edit the relevant config settings here but it is not as complete as the option above
- ro.product.model and ro.product.brand
- builds - Change device model on Android 10 - Android Enthusiasts Stack Exchange - Change phone model with "MagiskHide Props Config"
- Magisk - Device simulation - If you want to simulate a specific device (to get access to device specific apps in the Play store, as an example), you can activate this option. It will pull information from the currently used fingerprint (has to be set by the module) and use this to set a few certain props to these values.
- Change device model on Android 10 | AndroidHiro.com - Change device model on Android 10.I have Realme X2 (RMX1992) phone with Lineage OS 17.1 with root.
- Magisk Official Sites
- Change Model number in the firmware before flashing
Change the Phone Model Number - The Best Solution
This method makes no permanent changes to your phone and is very easy to do when you have instructions and we will be using:
- Magisk
- MagiskHide Props Config
- Terminal
Install instructions
- Install Magisk (I did this via TWRP Recovery)
- Reboot your phone
- Update Magisk to the latest version
- Download and copy MagiskHidePropsConf-v6.1.2.zip to your SD Card
- README.md - MagiskHidePropsConf · GitHub - MagiskHidePropsConf instructions.
- MagiskHide Props Config - Magisk - Download here - This module changes prop values using the Magisk resetprop tool, something that is very easy to do with a Magisk boot script and some simple commands.
- Open Magisk in android and update it if required
- Click on the `Modules` button at the bottom right
- Click on `Install from storage`
- Find the file MagiskHidePropsConf-v6.1.2.zip and double click it to install
- Reboot when prompted
- Now install a terminal so we can use MagiskHide Props Config
- Terminal Emulator for Android - Apps on Google Play - Access Android's built-in Linux command line shell. Unleash your inner geek!
- Just give this app temporary superuser access when prompted, this prevent issues or accidents.
- Run the terminal app and follow these instructions
- type: props
- select: Edit device fingerprint / 1
- Make a note of your current fingerprint, i use screenshot for this
- select: Pick a certified fingerprint / f
- select brand:
- My new phone brand: Samsung / 26
- select model:
- New model for my phone: Samsung Galaxy S8 SM-G950F (8.0.0) / 58
- select yes to confirm
- reboot phone when prompted
Notes
- This allowed me to download ebay from the play store.
- Lineagos still shows my phone as a SM-N9005
- eBay app would not let me log in / Invalid request
- I then tried the clear storage and cache which did not fix anything
- I rebooted my phone, i can now log into eBay.
- My phone still shows as a Samsung SM-N9005 on the Google Play store
